Chrome Zero Day Exploit: 5 Powerful Fixes to Stay Safe

Hoplon InfoSec
06 Nov, 2025
This month, when Google pushed out an emergency update, it wasn't the usual routine fix. Researchers say that this update closed a live attack vector that was already being used in the wild and was linked to a Chrome zero-day exploit. The alert came quietly but urgently, and the best thing everyone with the browser can do right away is to update Chrome to avoid being an easy target.
What makes this feel different?
A zero day means that attackers have code or methods that work before most users and many defenders know how to stop them. In this case, the vulnerability chain could let an attacker run code on a victim's computer just by getting them to visit a bad page or load bad content.
That's the worst-case scenario for browsers because it makes it easier for attackers to get in. When you talk about a Chrome zero-day exploit, it helps people understand how serious it is without going into too much detail.
What the emergency patch did to fix
According to Google's advisory and several security teams, the update fixes several problems in important parts like the JavaScript engine and graphics layers. Some of these flaws include problems with memory corruption and type confusion that can let attackers run code from a distance.
-20251106054300.webp)
The emergency release focused on a group of CVEs related to the V8 engine and the browser's graphics processing. These are the areas where small bugs can lead to big problems for the whole system. This patch is not normal, so don't worry about it. That's why the update was sent out right away.
Who should be concerned, and who should do something?
Everyone who uses Chrome should do something. The exploit can start without any special permissions, which puts home users, journalists, and employees who work with sensitive data at risk.
Attackers usually look for the easiest way in, and a Chrome zero-day exploit is just that: a way into a target that doesn't take much work but has a big effect. System administrators should make it a top priority to roll out the patch to all managed devices. To make sure they are on a patched build, each user should do the following:
How to quickly check and update Chrome
To let Chrome check for updates, open it, go to Settings, and then About Chrome. If you restart, any fixes that are still pending installation will be. Push the updated package from your deployment system as soon as you can for managed Windows, macOS, or Linux environments. You are good if the version number matches the emergency release notes. If not, don't put it off. A Chrome zero-day exploit gives attackers speed and ease; they count on people to wait.
If you can't update right away, take these steps.
If you can't apply an update right away, lower your exposure. Don't open links you don't trust, turn off plugins you don't need, and use a different browser profile that blocks JavaScript by default until you can safely patch. For businesses, think about separating high-risk users and turning off Chrome extensions that haven't been approved by the whole company. These aren't permanent fixes, but they give you time when a Chrome zero-day exploit is going around.
-20251106054306.webp)
What researchers saw in the real world
Security teams keeping an eye on these events saw drive-by attacks that used fake web content and weaponized media or script payloads. Some intrusions seemed to be planned, while others were random searches for any browser that wasn't up to date.
That mix is common: a well-made Chrome zero-day exploit can be used for both spying and big crimes. Government and industry groups put out public warnings that active exploitation was happening and told people to patch right away.
Why browsers are still a good target
Almost everything we do online starts with a browser. They make email, banking sites, and document viewers work. Attackers can get around a lot of security measures and run any code they want if they find one working exploit in a popular browser.
This time, Google fixed security holes in parts that deal with graphics or scripts. If you don't patch a Chrome zero-day exploit that affects those parts, it could corrupt memory and let someone take full control of your computer.
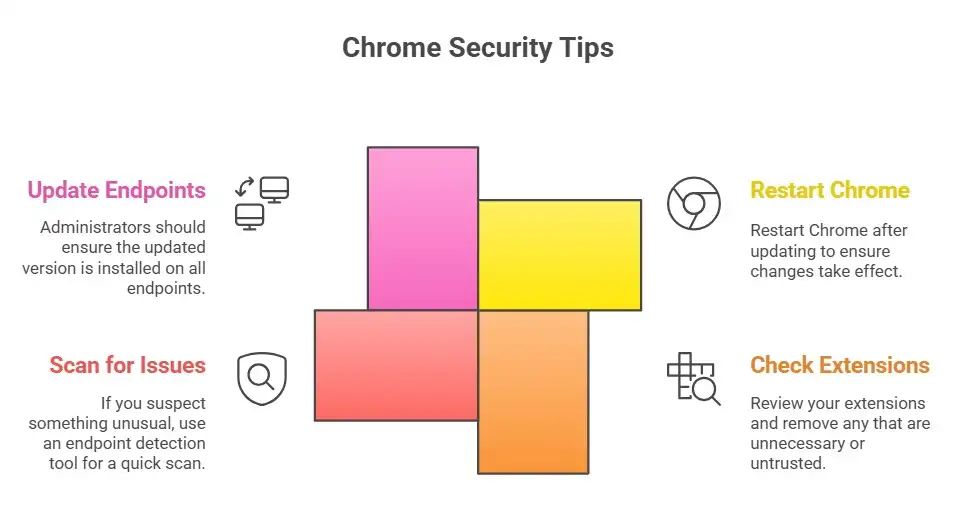
Helpful tips for readers
First, restart Chrome after updating it.
Second, check your extensions and get rid of anything you don't need or trust.
Third, if you think something is strange, use an endpoint detection tool to do a quick scan.
Fourth, for administrators, make sure that the updated version is on all endpoints and keep an eye on logs for strange connections or process launches. Check for updates on a regular basis. These steps make it less likely that a Chrome zero-day exploit will work.
What does this mean for habits that keep you safe in the long run?
Patching is important, but it's not enough. Use a layered approach: keep your software up to date, enforce the least privilege principle, teach users about links that look suspicious, and add extra security measures like application allowlisting and network segmentation. A Chrome zero-day exploit is a good reminder that attackers will always look for weak spots and that basic security is important.
Final thought
The most recent emergency update shows that browser security is still a problem. Google and its partners worked quickly to close the gap, but the work only protects users who install the patch.
Update now, keep your exposure to a minimum while you wait for patches to spread, and take browser alerts seriously.
Follow official advice and well-known security publications that keep track of CVEs and active exploitation if you want to stay up-to-date. The next Chrome zero-day exploit could come at any time, so the best way to protect yourself is to be ready.
You can also read these important cybersecurity articles on our website.
· Apple Update,
For more, please visit our Homepage and follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :