Under Armour Data Breach: Ultimate 2025 Insider Report

Hoplon InfoSec
18 Nov, 2025
Late in 2025, the Everest ransomware group publicly claimed a massive data breach against Under Armour, saying they were able to steal 343 GB of internal data. This shocking claim, if true, could change how people think about security in the world of sportswear and consumer brands.
This armor data breach (pun intended) brings up a lot of difficult issues, not just about customer privacy, but also about the security of company systems, supply chains, and proprietary information.
Everest is not a shady cyber gang. They have a scary list of well-known victims. These are not just random small businesses; they are big companies that do business all over the world. This means that the Under Armour data breach could have effects that go beyond the company's own walls.
Who are the people behind the Everest Ransomware Group?
You need to know who Everest is to understand how bad this under armor data breach is. HC3's profile of a threat actor says that Everest has been around since at least 2020. It started out as data extortion and then grew into full-fledged ransomware operations.
They are well-organized when it comes to technology. Everest uses tools like ProcDump to get LSASS memory, which helps them get passwords. They move laterally by using real credentials, scan the network with tools like netscan.exe, and use WinRAR to compress stolen data before sending it out.
They often use double extortion, which means they not only encrypt data (like most ransomware does), but they also steal sensitive information and threaten to make it public if their demands aren't met.
-20251118111502.webp)
What did Everest say in the Under Armour breach?
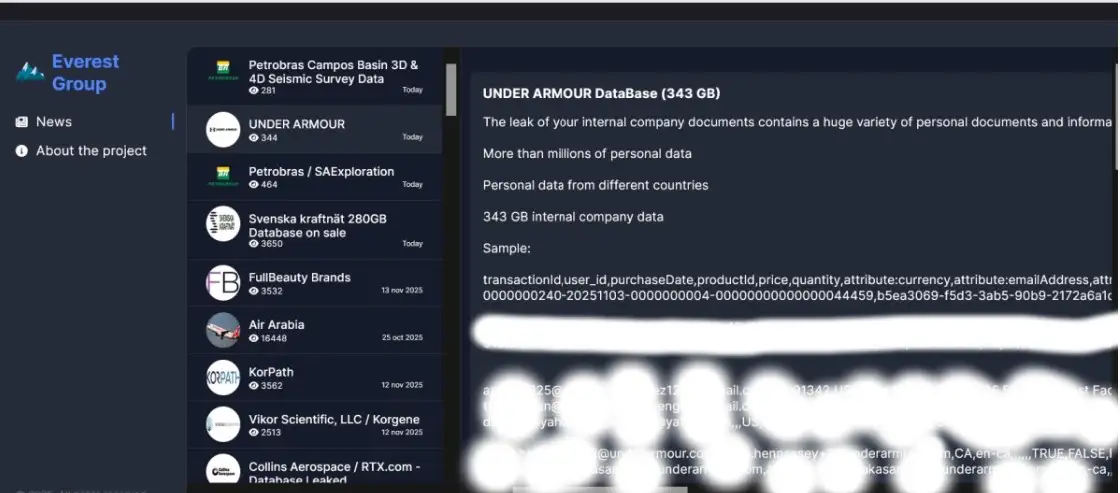
Several cybersecurity news sites say that Everest put up a post on their dark web leak site saying they stole 343 GB of data from Under Armour. They say they took customer data, employee information, and internal corporate documents, so this isn't flimsy stuff.
The group is said to have made some sample data public, which includes: • Customer identifiers (user IDs), emails, city or region, and gender.
• Purchase history: SKUs, prices, quantity, when things were bought, and whether or not something was returned.
• Logs related to marketing, like deep-link tracking and campaign entries.
• Product catalog data includes SKUs, sizes, colors, descriptions in different languages, inventory status, and prices.
• Employee information, such as their personal and work email addresses, where they work, their team, and their addresses.
Everest also told Under Armour that they had seven days to get in touch through Tox messenger before they would give them more information.
Why the Armour data breach is important: it's not just a risk to customers
1. Risks to the privacy and identity of users
Everest says that the breach may have exposed millions of customer records. There is no credit card information in the sample, but the PII (personally identifiable information) is enough for identity theft or phishing attacks.
When attackers have names, addresses, purchase histories, and even logs of people's behavior, they can run social engineering campaigns that are more convincing. The effects could be huge if this information gets into the wrong hands.
2. Data about employees getting out
It has been said that leaked internal documents include not only transactional data but also personal information about Under Armour employees, such as their email addresses, home addresses, team assignments, and more. For employees, that's a big privacy problem, and for Under Armour, it's a risk to their reputation and the law.
3. Business and Competitive Intelligence
Under Armour isn't just any store; it's a global performance brand that comes up with new ideas, makes new products, and has its own designs. The files that were supposedly stolen contain detailed information about products, including their catalog, SKU-level inventory, prices, and shipping information.
-20251118111504.webp)
If these claims are true, it's a big deal because competitors or people on the black market could use that breach to hurt Under Armour's edge in innovation or even copy designs
.
4. Effects on operations and strategy
The leak could include more than just product information. It could also include internal and strategic company documents like planning decks, board materials, supply chain data, vendor contracts, or internal memos. That could have an impact on Under Armour's long-term partnerships, the trust of investors, and even its place in the market.
Everest's History: Not a One-Time Deal
It looks like the Under Armor data breach is part of a bigger pattern. Over the past few years, Everest has taken responsibility for a number of high-profile events:
• Dublin Airport: The group says that around 1.5 million passenger records were stolen, including names, travel information, frequent flyer information, and baggage tag numbers.
• Coca-Cola (Middle East): Everest is said to have leaked HR information about employees in the UAE, Bahrain, and Oman, such as their salaries, visa papers, and internal structure.
• A Law Firm in the U.S.: Cyber Press says that Everest hit a law firm in Illinois and stole 150 GB of private client and legal data.
These examples show that Everest is going after not only consumer brands but also very sensitive corporate and institutional systems.
How Everest Does It: Technical Tactics
According to threat intelligence reports and security research:
• Initial Access: Everest often gets in using stolen credentials, RDP (Remote Desktop Protocol), or other remote access tools.
• Lateral Movement: Instead of just using malware, they use real user accounts to move around hacked networks.
• Credential Harvesting: They use tools like ProcDump to dump LSASS memory and get account credentials. They also copy NTDS (Active Directory) databases.
• Collecting and stealing data: After scanning the area, they use WinRAR to compress files and then steal them with remote tools like Splashtop.
• Covering Their Tracks: They often delete tools and reconnaissance artifacts to avoid being found.
• Tortion Tactic: They say they will leak data if ransom demands are not met, even if they can't or don't encrypt everything.
Why choose Under Armour? Why now?
Under Armour is not just a brand of clothes. It is a global business that works in retail, digital fitness (like MapMyRun or MyFitnessPal), partnerships with athletes, research and development, and more. Because of that ecosystem, it's a great target for hackers like Everest.
Everest may be trying to get a big payout by stealing 343 GB of data, but they may also be trying to control public relations. The gang could leak the data if Under Armour doesn't pay attention to them, which would be a huge blow to their reputation.
Second, as brands become more data-driven by using information about customer behavior, the supply chain, and new products, they become more appealing to cybercriminals. This breach could be a sign of a bigger trend: ransomware actors are no longer just encrypting files; they want to get deep commercial access and intelligence.
What does Under Armour need to do, and what can customers do?
For Under Armor:
• As soon as possible, make a public statement about the breach. It matters that things are clear.
• If the breach is real, use forensics to figure out exactly what was taken.
• Get a ransomware negotiation or incident-response team to help.
• Follow the rules for data breaches and let regulators, customers, and employees know.
• Put more money into making internal systems, access controls, and network segmentation stronger.
For Customers:
• Keep an eye on your email, transaction history, or account activity on Under Armour.
• Change your Under Armour password, and if you can, turn on two-factor authentication.
• Be careful of phishing: hackers may send you "urgent breach" emails that look like they come from Under Armour.
• If you're worried that your personal information might be used in a bad way, look into credit or identity monitoring services.
The Big Picture: What This Breach Could Mean for Cybersecurity
This supposed under armor data breach is more than just a brand getting hacked. It's a sign of trouble. Attackers like Everest are changing their tactics. They're no longer just encrypting data and asking for money; now they're going after the brains of modern, data-rich businesses. When a company's private designs, customer information, and business plans are all at risk, the stakes are higher.
If Everest's claims are true, it could change how companies in the consumer sector think about cybersecurity. Athletic companies, fashion brands, and stores may need to change how they protect their internal data, not just the systems that customers use.
source: cybernews
Final Thoughts: A planned breach that could have serious consequences
It is very worrying that the Everest ransomware group says they got into 343 GB of Under Armour's internal data. Not only did Everest hack customer data, but they also said they might have access to Under Armour's operations, product roadmap, and people.
Under Armour's problem won't just be whether or not to pay a ransom; it'll also be how to rebuild trust and make its defenses stronger. For customers, the breach is a reminder that cyber risk is very real, even in a lifestyle brand.
In the end, this Under Armour data breach (again, no pun intended) could change how companies outside of the "tech space" think about ransomware and data theft.
Questions and Answers
Q: Has Under Armour confirmed the 343 GB data breach?
A: Not yet. Everest has taken responsibility for the breach and released sample data. As of now, Under Armour has not publicly confirmed how big the leak is.
Q: Do the leaked files have credit card numbers?
A: Everest has shared sample data that shows no credit card information has come to light. But they say that the breach includes personal and transactional information like email addresses, purchase history, and addresses.
Q: Why does Everest want to go after Under Armour?
A: Probably blackmail for money. Under Armour's business has valuable commercial data like product catalogs, customer behavior, and inventory, which makes it a very valuable target for hackers.
Q: Has Everest hacked into other businesses?
A: Yes. Everest has taken credit for other well-known attacks, such as those on Dublin Airport (passenger data), Coca-Cola (employee HR data), and a U.S. law firm (legal documents).
You can also read these important cyber security news articles on our website.
· Windows Fix,
· WordPress Issue .
For more, please visit our Homepage and follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :