Docker Compose Vulnerability: Major Security Risk You Must Know

Hoplon InfoSec
16 Nov, 2025
When most developers think about Docker, they think about efficiency, scalability, and modern DevOps automation. However, a recent Docker Compose vulnerability has reminded the community that even trusted tools can become potential attack vectors. This flaw allows attackers to overwrite arbitrary files on the host machine, creating a pathway for serious compromises if left unpatched.
Docker Compose is widely used for defining and managing multi-container applications. Due to its deep integration with local file systems and configuration files, any security flaw can propagate across multiple environments, ranging from developer laptops to production clusters. Understanding this vulnerability isn’t just about patching a bug; it’s about recognizing how containerization, while powerful, also carries shared responsibility for security.
Understanding the Docker Compose Vulnerability
At its core, this vulnerability stems from how Docker Compose handles file paths and symbolic links during the build and deployment stages. In specific configurations, a malicious actor could craft a Compose file that points to sensitive directories or overwrites critical files on the host system.
Think of Docker Compose as a blueprint for your application’s architecture. It defines where images, volumes, and networks live. But if an attacker can manipulate that blueprint even slightly, they might redirect those definitions to overwrite system files such as configuration settings, SSH keys, or sensitive application data.
Security researchers noted that this flaw can be exploited both locally and in shared development environments where developers run untrusted Docker Compose. YML files. This makes the issue particularly concerning for organizations that rely on collaborative DevOps workflows.
In some reported cases, arbitrary file overwrite attacks were demonstrated by embedding harmful paths within Docker Compose volume mappings. When executed, the Compose tool didn’t adequately validate these paths, allowing overwriting of host-level files outside the container’s intended sandbox.
How Attackers Exploit This Flaw
To grasp how dangerous this is, imagine you download a seemingly harmless project from GitHub that includes a Docker Compose. yml file. When you run docker-compose up, the system builds containers and mounts volumes just as expected. However, a malicious actor could have inserted a path like ../../etc/passwd in the volume section.
Without proper checks, Docker Compose might follow this path and overwrite sensitive files, effectively granting an attacker system-level control or breaking the host configuration.
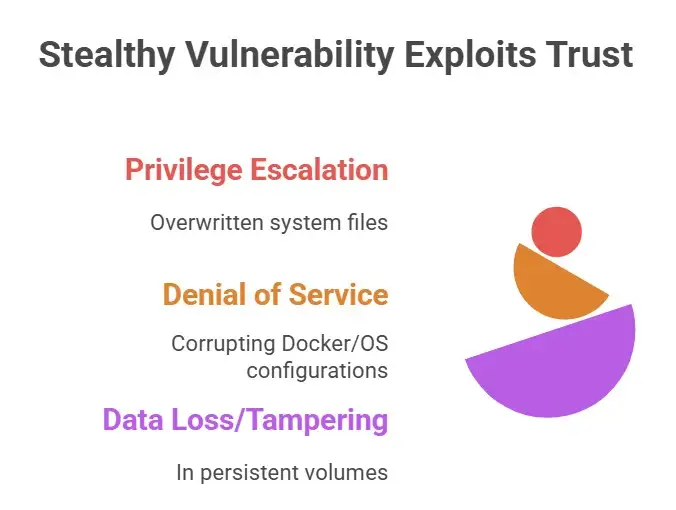
This vulnerability doesn’t rely on traditional code execution exploits; it leverages misconfiguration and trust. That’s what makes it stealthy and difficult to detect. A simple oversight during configuration can lead to catastrophic consequences, including:
· Privilege escalation through overwritten system files.
· Denial of Service (DoS) by corrupting essential Docker or OS configurations.
· Data loss or tampering in persistent volumes.
In a real-world scenario, an attacker might not even need direct shell access. By sharing a poisoned Compose file within an open-source project or internal repository, they can cause damage once unsuspecting developers execute it.
Potential Impact on Systems and Developers
The Docker Compose vulnerability hits hardest in environments where automation and CI/CD pipelines depend on Compose definitions. Once a malicious Compose file is introduced into an automated build or deployment, the consequences can spread across multiple services or even an entire Kubernetes cluster.
The most severe impact lies in the loss of data integrity. Imagine a configuration file holding database credentials being replaced or corrupted. Not only does this disrupt workflow, but it may also expose sensitive credentials to unauthorized users.
Developers, especially in fast-moving teams, often run Compose files without reviewing every line, a practice attackers count on. Since these YAML files are meant to be convenient and portable, they naturally invite sharing and reuse, which ironically amplifies risk.
Enterprises that use Docker Compose in multi-tenant environments or cloud-based CI/CD systems face even greater threats. If multiple users share the same build environment, a single exploit can cascade across containers, compromising isolation boundaries.
Mitigation and Fixes
Docker’s security team acted quickly once the issue was reported. Patches have been released in the latest Docker Compose versions, closing the arbitrary file overwrite loophole by enforcing stricter path validation and sandboxing mechanisms.
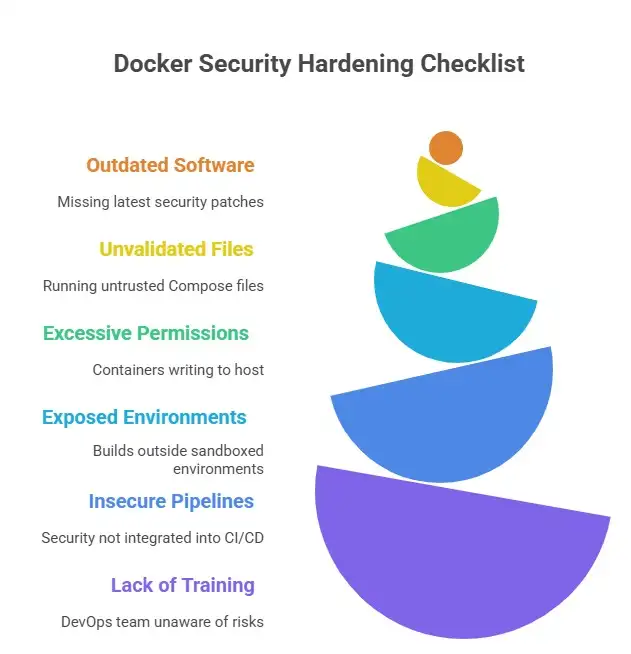
However, updating isn’t the only step you should take. Here’s a practical checklist for mitigating similar issues:
1. Update Docker and Docker Compose
Always upgrade to the latest stable version. Many vulnerabilities, including this one, are fixed silently through regular updates.
2. Validate Compose Files Before Use
Never run third-party or unverified Compose files. Use tools like Docker Scout or static analysis linters to scan configurations before deploying them.
3. Use Read-Only Volumes and Limited Permissions
When defining volumes, specify them as read-only wherever possible. This prevents containers from writing to the host unnecessarily.
4. Employ Namespaces and Isolated Environments
Run Docker builds in sandboxed environments or within virtual machines to limit exposure. Tools like Podman or Docker Desktop’s sandbox mode help reduce risk.
5. Integrate Security into CI/CD
Make security scanning part of your build pipeline. Include automated Compose file validation to flag unsafe volume paths or potentially harmful directives.
6. Educate Teams
Human error remains the biggest vulnerability. Regular training on container security best practices ensures your DevOps team recognizes potential risks before they become incidents.
Lessons for DevOps and Security Teams
This vulnerability highlights a recurring theme in cybersecurity: the trade-off between convenience and control. Docker Compose was built to simplify complex multi-container setups, but that very convenience can mask dangerous oversights.
For DevOps teams, this incident is a reminder that infrastructure as code (IaC) must be treated with the same security scrutiny as application code. Version control, peer review, and access restrictions are essential safeguards.
Security teams, meanwhile, should implement runtime monitoring tools like Falco or Aqua Security to detect abnormal container behavior, for example, attempts to write outside defined volume boundaries.
Organizations that adopt a zero-trust philosophy can mitigate most of these risks. Instead of assuming that Compose files or images are safe by default, enforce verification policies that validate every configuration and artifact before deployment.
Final Thoughts
The Docker Compose vulnerability serves as a wake-up call for developers and DevOps professionals worldwide. While the immediate threat has been patched, it underscores the importance of security hygiene, configuration validation, and team awareness in every containerized environment.
Container technology has revolutionized software delivery, but it hasn’t eliminated security risks. Staying proactive, updating regularly, and treating infrastructure definitions as critical assets will help prevent such vulnerabilities from striking again.
FAQs
1. What is the Docker Compose vulnerability about?
It’s a security flaw that allowed attackers to overwrite arbitrary files on the host machine through manipulated volume paths in Compose files.
2. How can I fix the Docker Compose vulnerability?
Update to the latest Docker Compose version, validate Compose files, and avoid running untrusted configurations.
3. Can attackers gain system access through this exploit?
Yes. If exploited, the vulnerability could enable privilege escalation or system compromise by overwriting sensitive files.
4. How do I secure my Docker environment against similar threats?
Use read-only volumes, implement CI/CD security checks, and maintain least-privilege principles for all containers.
5. Is this vulnerability still exploitable today?
Not in the latest patched versions, but unpatched systems and outdated Compose files remain at risk.
You can also read these important cybersecurity news articles on our website.
· Apple Update,
Share this :