Cyber Threats in 2026: The Hidden Risks Businesses Ignore

Hoplon InfoSec
25 Dec, 2025
Are the cyber threats of 2026 really going to be worse than what businesses face now?
Most experts agree that the answer is clear but not easy to hear. Yes.
Security researchers, enterprise CISOs, and threat intelligence teams are all saying that the next wave of attacks won't depend on chaos or noise as of December 2025. Digital Journal and global cybersecurity firms that support their reporting say that cyber threats in 2026 will be quieter, more planned, and much more harmful to business operations than previous attack cycles.
It's not just new technology that makes this change scary. It's how well attackers now know how businesses work, how decisions are made, and where the real pain is.
What Makes Cyber Threats in 2026 Different from the Past
Attackers Don't Hurry Anymore. They look
One of the most important changes in cyber threats in 2026 is being patient.
In the past, attacks were quick and clear. Files were encrypted. Warnings flashed on screens. Within minutes, companies knew something was wrong. That model is going away.
Attackers these days often spend weeks inside a network before they do anything bad. They listen in on conversations inside. They find out which systems are the most important. They quietly chart the permissions and identity flows in the cloud. Damage is already strategic by the time it shows up.
This change is why many experts say that the cybersecurity threat landscape in 2026 will be driven by intelligence instead of tools. The goal is not to damage systems. The goal is to use leverage.

Companies Have More Options Than They Think
Connections are what make modern companies work. Services in the cloud. APIs. Tools for SaaS. Access from afar. Partners. Vendors.
Every connection solves a problem for the business. Each one also makes a new way in.
More and more cyber threats and incidents in 2026 don't even involve malware. They begin with stolen login information, cloud roles that aren't set up correctly, or API keys that are out in the open. Everything looks real on the outside, which makes it hard to find and slow to do so.
Security teams often find out about these breaches only after they notice strange patterns in data access or billing activity. By that time, attackers may already have several ways to get into the environment.
The Cyber Threats Experts Say Will Be the Most Important in 2026
Several types of attacks keep coming up in threat intelligence reports, breach investigations, and real incident trends.
• AI-powered cyberattacks that change messages in real time
• Ransomware evolution in 2026 that focused on disruption instead of encryption
• Cyberattacks on the supply chain through trusted vendors
• Zero-day attacks in 2026 that target cloud services
• Deepfake cybercrime that goes after executives and finance teams
• Identity-based attacks that take advantage of legitimate access

Attacks that use AI need to be looked at closely. Attackers are using automated tools to make phishing messages that sound like they come from real coworkers. The language sounds real. It seems like the right time. It's hard for regular filters to find them.
Ransomware has also gotten better. In 2026, cyber threats often start with stealing data and then selectively disrupting the most important systems. The pressure comes from the fact that all three of these things can happen at once: damage to reputation, legal exposure, and operational downtime.
Supply chain attacks are still very dangerous because companies often trust their vendors too much. One weak partner can ruin years of work on internal security.
Why Cyber Threats in 2026 Are a Business Problem, Not an IT Problem
The biggest mistake that companies still make is thinking of cyber risk as a technical problem.
Business cyber threats in 2026 have a direct impact on sales, customer trust, regulatory standing, and the credibility of leadership. The costs of recovering from cyberattacks are no longer the only ones that matter.
Executives are often shocked by how long the effects last. Reviews by lawyers. Insurance disputes. Customers leaving. Deals that fell through. These effects don't show up until months after the breach.
Regulation puts even more pressure on things. Disclosure requirements are closely related to the risks of data breaches in 2026. If reporting times or communication aren't handled properly, even small problems can get worse.
This is why boards are starting to ask not just if systems are safe, but also if the business is strong.

A Realistic Example From the Field
A regional services company saw small problems in its cloud audit logs in late 2025. No alarms. No note asking for money.
Weeks later, a number of clients said they had received convincing emails that included private account information. Investigators found that the problem was caused by API credentials that had been stolen from a third-party tool.
The attackers never turned off the systems. But the damage was real. Trust fell apart quickly. Contracts were put on hold. Leaders had to answer tough questions.
This event is a perfect example of new cyber threats in 2026. The damage was done by losing trust, not by broken infrastructure.
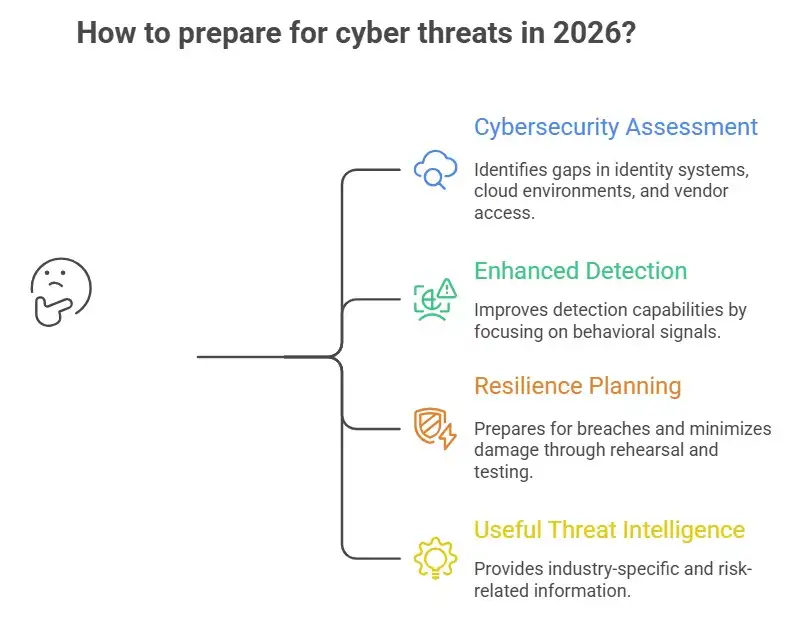
How Businesses Can Get Ready for Cyber Threats in 2026
Being honest is the first step in getting ready.
First, businesses need to be seen. A good cybersecurity readiness assessment can help find gaps in identity systems, cloud environments, and vendor access.
Second, detection needs to get better. Just stopping it isn't enough. Managed detection and response services and SOC modernization look at behavioral signals instead of static alerts.
Third, planning for resilience is more important than ever. Planning for cyber resilience means that you expect breaches to happen and work to limit the damage. Rehearsing and testing response plans at the executive level makes a big difference.
Finally, threat intelligence needs to be useful. Alerts that are too general don't help. Businesses need information that is directly related to their industry, technology stack, and level of risk.
In 2026, being ready for cyber threats means being aware, not scared.
Frequently Asked Questions About Cyber Threats in 2026
What will be the biggest threat to computers in the future?
Identity-based attacks and AI-driven social engineering are likely to do the most damage.
How will AI affect cyberattacks?
AI lets attackers target more people, make their lies more believable, and change their plans faster than campaigns run by people.
Is ransomware still a big problem?
Yes, but it's changing from just encryption to data pressure and operational disruption.
What can businesses do to get ready for future cyber threats?
By making things more visible, making identity controls stronger, and making sure thatthe cybersecurity strategy is in line with business goals.
The End
In 2026, cyber threats aren't any louder. They are more intelligent.
Attackers are learning how companies work and where they are most vulnerable. The businesses that do well will be the ones that know what risks they face, find problems early, and respond clearly.
The next step that makes the most sense is easy. Be honest about how ready you are. Be aware of what you can see. Know what you can't do. And think of cybersecurity as a business skill, not just a technical task.
You can also read these important cybersecurity news articles on our website.
· Apple Update,
For more Please visit our Homepage and follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :