Google Cloud Security Summit 2025: Alert Triage Preview
-20251118102718.webp&w=3840&q=75)
Hoplon InfoSec
23 Nov, 2025
A New Beginning for Security Teams
Picture yourself as a security analyst at a company that is not too big. Every morning, when you log into your SecOps dashboard, you see hundreds, maybe even thousands, of alerts. Some are bad, some are good, but going through them all is like drinking from a firehose.
Now imagine an AI-powered assistant that not only looks over those alerts but also looks into them, builds a logical tree of processes, and gives you a verdict, all without you having to do anything. Thanks to Google's latest announcement at the Google Cloud Security Summit, where the public preview of the Alert Triage and Investigation Agent was shown, that future is becoming real.
What the Google Cloud Security Summit Means
At the Google Cloud Security Summit, Google shared a big idea. The company isn't just adding AI to existing tools; they're thinking about how AI can completely change how security operations centers (SOCs) work. The summit wasn't just a way to sell things; it was also a plan for the future of cloud-native security. There were many big new ideas announced, but the alert triage and investigation agent may have been the most interesting.
There is more to this than just hype. Google's leaders talked about how this agentic AI can cut down on the amount of work that needs to be done by hand, speed up response times, and give clear reasons. That matters a lot because alert fatigue is a real thing. For a lot of SOC teams, the number of alerts they get every day is too high. Google is making that daily grind easier by adding an intelligent, self-driving assistant.
What is the Alert Triage and Investigation Agent, really?
The Alert Triage and Investigation Agent (also known as the triage agent) is an AI assistant that was made specifically for Google Security Operations (SecOps) to handle the first steps of alert processing automatically.
It works by dynamically looking into alerts, gathering context, adding threat intelligence to data, analyzing command-line activity, reconstructing process trees, and finally coming up with a verdict: true positive or false positive. This isn't just a guess; it's based on Mandiant's analyst principles.
One of the best things about it is how easy it is to understand. It doesn't just give you a result when it's done with an investigation; it also gives you a structured reasoning trail. You can see how the agent came to its conclusion, what queries it ran, what data sources it used, and how sure it is. That openness helps human analysts trust you.
How It Works in Real Life
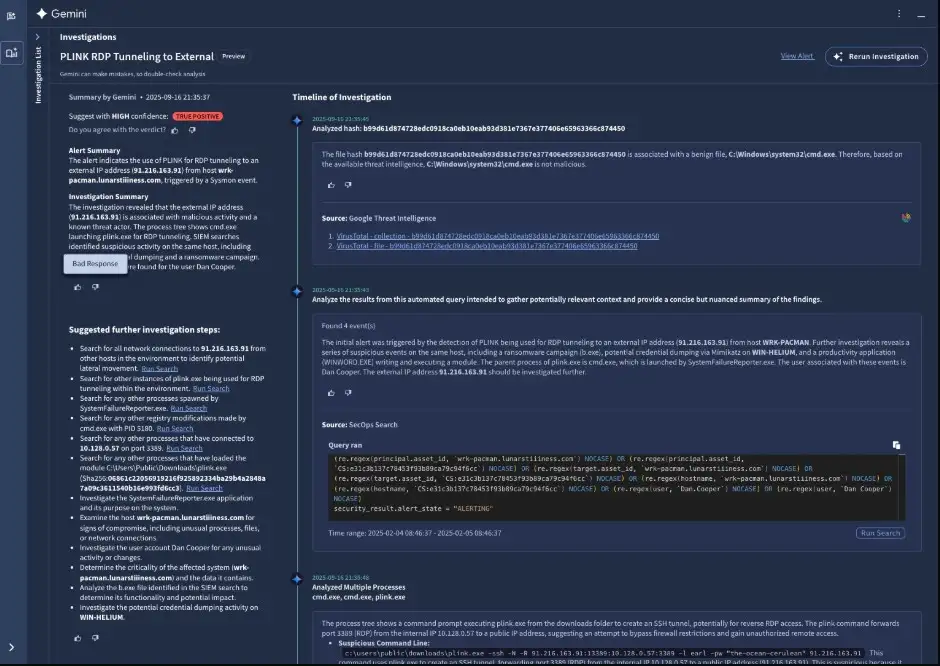
So, how does this agent work behind the scenes? According to Google's documentation:
Search Queries That Change
It runs search queries in SecOps to get logs, events, or telemetry that are related. These don't stay the same; the agent changes and improves its plan as it looks into things.
1. Adding to Threat Intelligence
It works with Google Threat Intelligence (GTI) and Mandiant data to put indicators of compromise (IOCs) like domains, file hashes, and URLs into context and then links them to the current alert.
2. Analyzing the Command Line
The agent can read alerts that involve command-line execution (even commands that are hard to read), explain in plain language what is likely going on, and point out strange behavior.
3. Process Tree Reconstruction. It makes a process tree from the system telemetry, which shows how child processes were created, the order in which they were created, and then uses that to figure out the bigger picture.
4. The decision and suggested next steps
Lastly, the agent gives a verdict, which can be either "true positive" or "false positive," along with a score of how sure they are. But that's not all; it also suggests what to do next, like whether to escalate to a human analyst, suggest more research, or suggest fixes.
One of the best things about it is how fast it is. Most investigations take 3 to 5 minutes, and the system can run itself or be triggered by you.
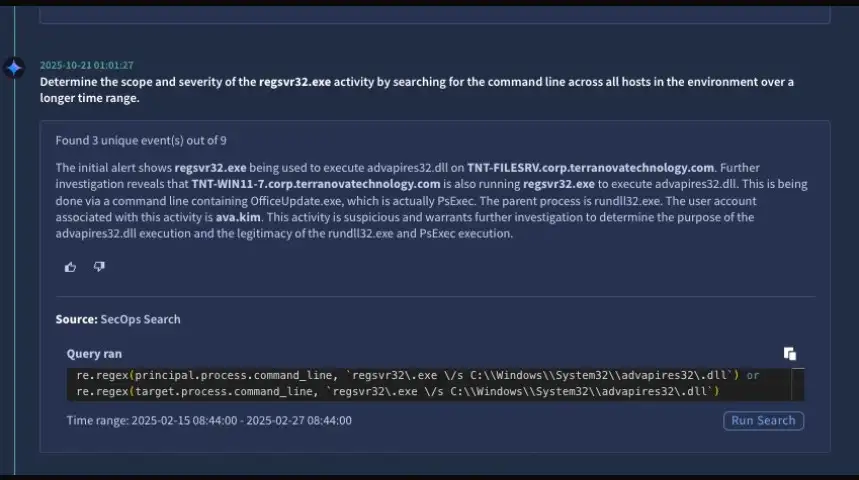
Why This Matters: Effects in the Real World
Google stressed at the Google Cloud Security Summit how this agent could make things much easier for Tier 1 and Tier 2 analysts. In real life, that could mean:
• Less stress. People say that security teams are always too busy. Defenders can get back time to think strategically by letting AI do the same investigations over and over.
• A quicker response. When the agent does the first triage and investigation, alerts that need immediate attention can be escalated more quickly.
• More accurate. The agent's decisions are based on real-world threat hunting and investigation knowledge because they use best practices from Mandiant senior analysts.
• Openness and faith. Because the agent keeps track of its reasoning and gives a clear chain of evidence, analysts can check and confirm its work instead of treating it like a black box.
Google gave a real-life example: during the private preview phase, the agent had already handled hundreds of thousands of alerts for a financial services company. Their analysts say that the summaries made by the agent helped them make quick choices, like whether or not the alert was likely to be malicious. What should we do now?
Another customer, a big US retailer, said that this agent's ability to save time and make things clearer was "drastic" because it combined investigation data and cut down on repetitive questions.
The Big Picture: Agentic SOC
Google showed off the agentic SOC at the Google Cloud Security Summit. The Alert Triage and Investigation Agent is part of this bigger plan. It's not about getting rid of people; it's about giving them AI agents that work together, automate, and help them.
In this future SOC, you could have more than one agent: one for sorting through alerts, one for analyzing malware, one for hunting threats, and even one for building detection systems. They all work together, passing off tasks, sharing information, and letting human analysts know when they need to.
A system like this can help tired people find things in big spaces and let people who know a lot about a subject do the hard work of figuring things out that need context, creativity, and judgment.
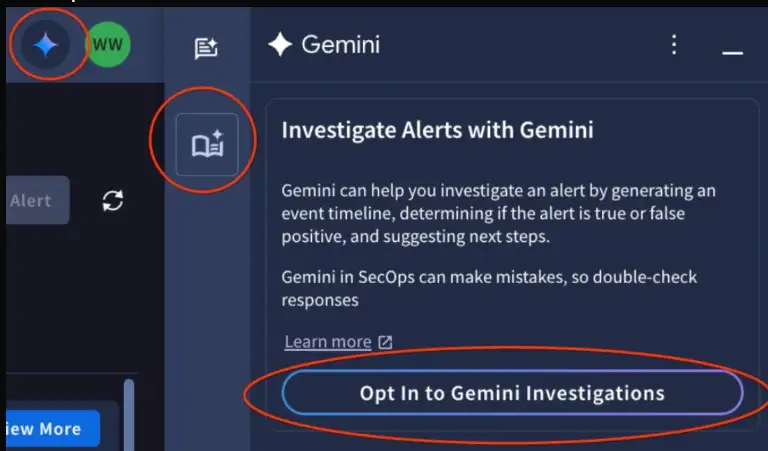
That being said, this technology isn't a magic wand. There are some important things to keep in mind:
1. Pre-GA feature: The Alert Triage and Investigation Agent is now in public preview, but not available to everyone. That means there might still be restrictions or changes.
2. Support limits: The paperwork says that investigations are limited to 10 per hour per tenant, with limits on manual vs. automatic.
3. Data scope: The agent only works on alerts that come in through Google SecOps SIEM, not through all types of connectors (for example, not through some SOAR connectors).
4. Trust calibration: Analysts need to figure out how much they can trust the agent's decision, even though it explains why it made that decision. It is not taking the place of human judgment; it is adding to it.
5. A feedback loop is needed: Google asks users to give feedback by clicking on thumbs-up or thumbs-down icons in the UI. This feedback loop from the real world is very important for making the model better all the time.
What This Means for the Future of Cloud Security
This preview is a big step toward making AI a full-fledged member of security operations, not just a toy project but a real, logical partner. Google is sending a message that it sees AI agents as the building blocks of future SOCs by launching at the Google Cloud Security Summit.
This also makes cloud security harder: security teams not only have to protect data and workloads, but they may also have to protect their own AI agents. The agentic SOC idea means that security teams need to think about identity, access control, governance, and the life cycle of the agents themselves.
Taking part in the preview gives businesses a chance to get early access, help shape the feature, and get their teams ready for a future that is more automated and smart. Defenders can use AI to make their work easier, faster, and more strategic.
End: A Smart Assistant Joins the SOC Team
The public preview of Google's Alert Triage and Investigation Agent, which was announced at the Google Cloud Security Summit, is more than just a cool demo; it's a real change in how SOCs work. Google is giving security teams an AI assistant that works like a junior but learns quickly by using Mandiant's knowledge, clear reasoning, and threat intelligence.
This doesn't take the place of human analysts. Instead, it helps them by taking away their triage fatigue, speeding up investigations, and letting them focus on the big, tough problems. This agent can only get smarter, more accurate, and more trusted as more organizations choose to use it and give feedback.
If you're in a SOC, now is a good time to look around. Try out the preview, test the workflow, question the agent's decisions, and help shape the future of security operations. Smart defenders deserve smart assistants, and Google's preview could be the start of a safer, faster, and more efficient time.
FAQ
Q1: Who can see the preview of the Alert Triage and Investigation Agent?
A1: Only Google Security Operations Enterprise and Enterprise Plus users who meet certain requirements can see the public preview.
Q2: How does the agent tell if an alert is a real or false positive?
A2: It uses a mix of dynamic search queries, threat intelligence enrichment (through GTI and Mandiant), command-line analysis, and rebuilding the process tree. After looking at all the evidence, it gives a verdict and a score of how sure it is.
Q3: Is it clear how the investigation works?
A3: Yes. The agent makes a timeline of the investigation, writes down each step it took, explains why it took each step, and gives the sources of its data. Analysts can look at how it came to its conclusion.
Q4: What are the problems with this preview?
A4: As a preview (pre-GA) feature, there are limits on how many investigations can run per hour, and it only works with certain types of alerts that come from SecOps SIEM.
You can also read these important cybersecurity news articles on our website.
· Apple Update,
Share this :