Palo Alto VPN Attack 2025: 5 Critical Facts to Know
-20251120053036.webp&w=3840&q=75)
Hoplon InfoSec
20 Nov, 2025
Sometimes in cybersecurity, the numbers hit you before the whole story does. It felt like one of those times when hackers tried to break into exposed GlobalProtect VPN portals more than two million times.
It first showed up in security forums, and then analysts started to see odd traffic patterns on networks that used the platform. This quickly became a big story. The Palo Alto vpn attack situation quickly got out of hand and became something that businesses couldn't ignore.
It wasn't just the size of the attempts that worried people; it was also how quickly they were growing. Some groups said scans happened every few minutes. Some people saw automated attempts to stuff credentials, as if someone was testing millions of combinations just to find one weak password that would work.
This is why the Palo Alto vpn attack talk has become one of the biggest security stories of the year. It's not just about one vendor or piece of technology. It shows how good attackers have gotten and how quickly they change when they see a hole in your defenses.
-20251120053037.webp)
What's Going On with GlobalProtect
You need to have a clear picture of GlobalProtect in order to understand what's going on. It is a popular VPN portal that lets employees safely access internal networks. That sounds easy at first, but things in the real world don't stay easy for long.
Security researchers began to say that automated bots were attacking GlobalProtect portals in waves. It looked like a normal scan at first. Then there were more than 2.3 million attempts at the activity. That's when experts figured out that this wasn't just random noise. The goal of the targeted Palo Alto vpn attack campaign was to find and exploit weaknesses and get valid login information.
A lot of businesses use this VPN to keep their remote employees connected. The effect on the whole world is huge when something like this happens. Your front door to the network suddenly feels open, which is never a good feeling for a security team.
Patterns started to show up as more data came in. Attackers were looking for systems that hadn't been patched, configurations that were out of date, and passwords that were easy to guess. Old-fashioned methods, but done on a scary scale and with a lot of time.
Why This Attack Is Important
The Palo Alto vpn attack is a sign of a bigger problem in the industry as a whole. Attackers are most interested in remote access tools because they are right on the edge of the corporate network. If someone gets in, they can move around without making any noise.
When hackers try millions of times to get into one type of portal, it's time to wake up. Organizations with few security staff may not have the time or money to check every attempt. Just the amount of work can be too much for smaller teams.
This is also a reminder that attackers don't always have to find a new weakness. Sometimes all they need to do is find someone who hasn't patched yet. That's how most ransomware groups get into networks. They wait for someone to get behind.
From my own experience working with companies that rely on VPNs a lot, the difference between being safe and being vulnerable is often just one setting that is missed. It could be a policy that doesn't require strong passwords. It might be a plugin that is no longer supported. Or it could be that someone thought a firewall rule worked when it didn't.
-20251120053037.webp)
Attack in Steps
The way the Palo Alto vpn attack works isn't hard to understand, which is one reason it's so dangerous. Attackers usually start by looking for open VPN portals on the internet. These scans happen all the time, even when there isn't a big threat in the news.
They start credential stuffing attacks as soon as they find an open portal. This means they use usernames and passwords that have been stolen in the past. Every minute, they try out thousands of different combinations. A lot of them still work because a lot of people use the same passwords on different sites.
If the portal has a known security hole, attackers will try payloads that are meant to run code on the remote machine. Even if the system is patched, the number of attempts is so high that it can slow things down or make security teams lose focus.
The last step only happens if the attackers are successful. They move sideways into internal systems, looking for privileged accounts, private information, or access points that can help them reach more people.
How quickly it gets worse
Researchers recently heard from a mid-sized financial services company about their experience. They saw that people kept trying to log in over the weekend but failing. They thought at first that it was just noise from machines. By Monday morning, there had been more than 80,000 attempts.
Their logs showed a clear pattern. The attackers were going through every possible username in alphabetical order. The company was lucky to have multifactor authentication and GlobalProtect patches that were up to date. But the noise made them nervous.
-20251120053038.webp)
This event shows that even when controls are in place, constant stress can make a company less confident. And in cybersecurity, confidence affects response time more than most people know.
Risks for Businesses
The biggest risk in the Palo Alto vpn attack activity is not the attack itself. This is what happens if attackers find a portal that is weak.
Attackers can move quickly when one system is set up wrong. They can get around logging, turn off security tools, or put in backdoors. Some attackers don't use the access right away. They wait until the business is busy with something else.
Using the same credentials again is another risk. Attackers know that a lot of workers use the same passwords for different tools. This means that one successful login could lead to more opportunities than anyone thought possible.
Identity providers also work with GlobalProtect portals. If attackers get around authentication systems, they can pretend to be real users on the network.
Ways to Lower Risk
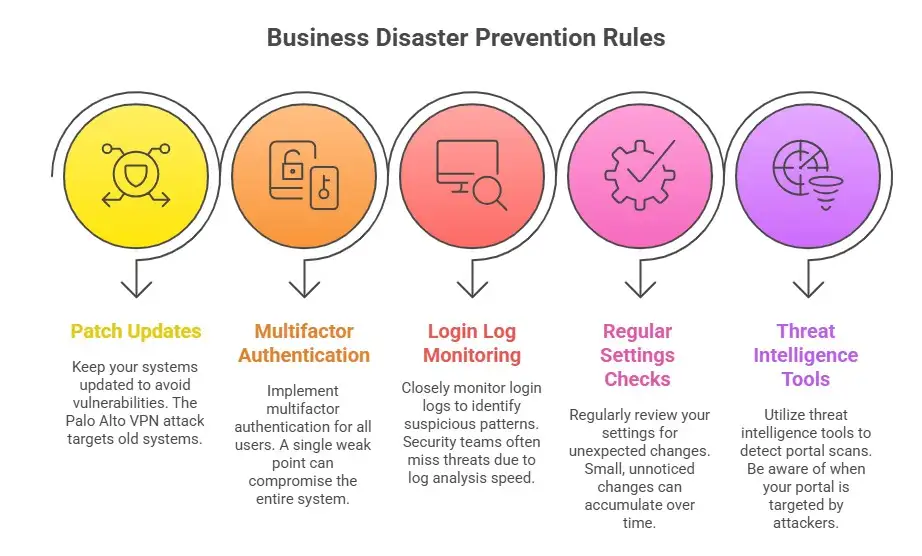
I've seen businesses avoid disaster by sticking to a few simple rules. None of them are hard, but you have to do them all the time.
First, make sure your patches are up to date. The Palo Alto vpn attack tries to get into old systems more than anything else.
Second, make sure that multifactor authentication is used everywhere. A weak point is created if even one user doesn't have it.
Third, keep a close eye on the login logs. Security teams often miss patterns because they can't read logs fast enough.
Fourth, do regular checks on your settings. People think that settings will never change. No, they don't. Over time, small changes happen that people don't always notice.
Fifth, use threat intelligence tools that let you know when your portal is on a list of sites that attackers are scanning.
Tools for Protection
Businesses are starting to use external vulnerability scanners, SIEM platforms, VPN monitoring systems, and identity access managers. Some teams use automation to find login attempts that are higher than normal. Some people use behavioral analytics to find patterns that look suspicious.
The key is to use these tools together in a way that helps the team instead of making it harder.
Finish Up
The Palo Alto vpn attack story has led to more and more attempts, which shows how important remote access security has become. There are millions of automated hits on GlobalProtect portals, so the message is clear. Hackers are patient, persistent, and always looking for the one door that someone forgot to lock.
Organizations that stay on top of things, keep their systems up to date, and keep a close eye on who has access have a much better chance of staying ahead of the threat. These habits are more important than ever as more people work from home.
FAQs
1. What makes GlobalProtect portals such a popular target?
Because they are on the edge of corporate networks and often give direct access to internal systems.
2. Is everyone who uses GlobalProtect in danger?
Only systems that are exposed or not patched are at high risk, but all organizations should check their configurations.
3. Can MFA stop most attacks?
It stops a lot of credential-based attacks, but it needs to be used on all accounts all the time.
4. How often should businesses update their VPN systems?
As soon as patches come out, especially when there are active threat campaigns.
You can also find these important cybersecurity news stories on our site.
· Apple Update,
Author: Hoplon Infosec
Bio: Security enthusiast with over 10 years in mobile cybersecurity. Connect with me on LinkedIn.
Address: 1415 W 22nd St Tower Floor, Oak Brook, IL 60523, United States
Phone: +1 773-904-313 , Contact: [email protected]
About/Privacy: At Hoplon Infosec, we provide expert insights into cybersecurity. Our editorial policy: all articles are written by in-house specialists or thoroughly reviewed by them to ensure accuracy, credibility, and up-to-date information.
Share this :