Penetration Testing Meaning: Ultimate Guide to Secure Systems

Hoplon InfoSec
30 Oct, 2025
Picture this: you own a cozy little shop in town, you lock your door each night, and you feel pretty safe. But one day you invite someone in at night, and someone pays someone authorized to walk through as a “burglar” and try your lock, your windows, and your camera system.
You watch what they do. You learn where you’re exposed. That, in effect, is what the phrases "penetration windows" and "penetration testing" mean and what "penetration offers" to a business in the cyber‑world. "Inviting someone to try the break-in" means you can fix it before a real thief shows up.
So, what does “penetration testing” really mean? Why do so many organizations now talk about pen tests, ethical hacking, vulnerability assessments, security testing, organizations, and the like? Let’s dive in.
What is penetration testing? What does it mean to test, and why does it matter?
At its core, penetration testing means simulating an attack on a computer system, network, or application to identify exploitable weaknesses. It’s sometimes called a pentest, and it’s one of the most hands‑on approaches in the toolbox of offensive security.
Why does this matter? Because standard automated scans, or “vulnerability assessments,” often only show you that something is wrong. A penetration test goes further; someone uses hacker‑mindset tactics to exploit that something to show you what the impact might be.
Imagine you know your door lock is weak. A scan tells you “lock is old.” A penetration test says, “Someone got in, stole the cash, and disabled the alarm.” That difference in insight is huge.
And given how many high‑profile data breaches we keep hearing about, the meaning of penetration testing shifts from “nice to have” to “must have.” According to reports, the global penetration testing market is growing fast; organizations are increasingly realizing that vulnerability scans alone are not good enough.
From definition to context: how to understand it fully
When exploring the meaning of penetration testing, you’ll often see distinctions drawn. For example:
· A vulnerability assessment is about scanning and listing weak points.
· A penetration test simulates real attacks to exploit those weak points.
· Ethical hacking is the broader field: everything from threat modeling to malware analysis and pen testing is one technique within that broader umbrella.
Also, in official standards like National Institute of Standards and Technology (NIST) or National Cyber Security Center (UK) guidance, the term is defined clearly: “A method of testing where testers target individual components or the application as a whole to determine whether vulnerabilities can be exploited to compromise the application, its data, or its environment resources.”
So “penetration testing meaning” isn’t just “run a scan.” It’s about a full‑blown real‑world attack simulation, overseen by approved professionals, to probe the essentially weakest links: people, configuration, code, and network.
-20251029222431.webp)
Types of penetration testing: the variety behind the meaning
If you pause and think about it, there’s more than one way to attempt a breach. When exploring the “penetration testing meaning,” we need to appreciate the types and flavors. Meaning, “Here are some of them:
· Network (external & internal): Testing from the outside world into your network, then from inside once you’re “in.”
· Web application / API testing: Checking web apps or APIs for things like injection flaws, “in” flaws, and broken authentication.
· Wireless / IaaS and IoT testing: Devices on WiFi, smart devices, and IoT smart devices are sometimes less hardened than corporate servers.
· Social engineering / human‑based attacks: Phishing, impersonation, smart devices, impersonation, and attacking staff because sometimes the “lock” is the human element.
· Cloud and hybrid environment testing: As more companies shift to the cloud, impersonation and the meaning of pen testing expand into new attack surfaces.
By identifying the type, you sharpen “penetration testing meaning” from generic into concrete: “we will test web apps” or “we will test staff via phishing.” the cloud,
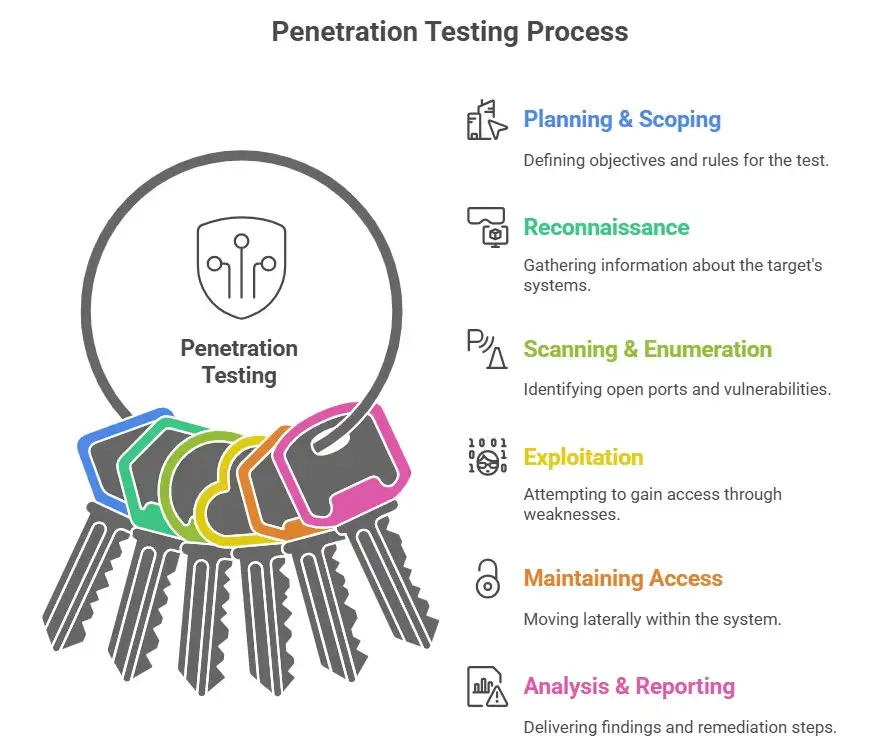
The process: what happens in a penetration test
Understanding the meaning of “phishing” and penetration testing Understanding the meaning of also means understanding how it is carried out. The standard process often follows phases like
1. Planning & scoping: Define objectives, systems, rule systems, and modes of engagement (what is allowed).
2. Reconnaissance: Collect information about the target’s systems and what’s exposed, and if there is anything there.
3. Scanning & enumeration: Use tools to identify open ports, services, known exposed services, and vulnerabilities.
4. Exploitation / gaining access: Try to use identified weaknesses to get in.
5. Maintaining access / pivoting: Once internal, try to move laterally, services, and laterally and see how far you can get.
6. Analysis & reporting: Deliver findings, severity, business risk, laterality, and remediation steps.
So when you think of penetration testing's meaning, you must also see it as a structured lifecycle, not a one‑off scan. And this process helps shift the meaning from “we looked for vulnerabilities” to “we attacked your system as a real adversary.”
Real‑world example: how it might play out
Let’s bring this to life. Imagine a mid-sized e-commerce company where the CTO says, “We need a penetration test.” Great. Then:
· In the planning phase, they define “we want to test our web application, our APIs, and our internal network,” thus clarifying the meaning and scope.
· During reconnaissance, the tester finds that their product API exposes detailed error messages and the web app uses outdated plugins.
· In the scanning phase, they discover a misconfigured database access from the web server and some weak authentication.
· Exploitation: the tester uses SQL injection to dump user records, then uses stolen credentials to move further into the network and access internal tools.
· Reporting: The testers show how a real attacker could have done this, estimate the cost of the breach, and recommend fixes: update plugins, enforce multi‑factor authentication, andauthentication, and restrict internal access.
This kind of scenario shows the value embedded in “penetration testing meaning”: it gives you not just “you have holes” but “here’s how someone would walk through them.”
Benefits: what you gain by doing it
When you invest in a test that captures the full meaning of penetration testing, you get several benefits:
· You discover hidden weaknesses before adversaries do, reducing the risk of breach and damage.
· You gain evidence and metrics to justify security budgeting and decisions.
· You satisfy regulatory or compliance requirements: many standards require regular penetration tests.
· You improve your overall security posture by shifting from reactive to proactive.
· You often gain staff awareness: when the test includes social engineering, people learn how vulnerable they can be.
In my personal experience, I saw a charity organization undergo a penetration test, and it dramatically changed their mindset: they went from “we have antivirus, so we’re fine” to “we need processes, we need testing, and we need to know how we would fall.” That shift is the deeper meaning of the exercise.
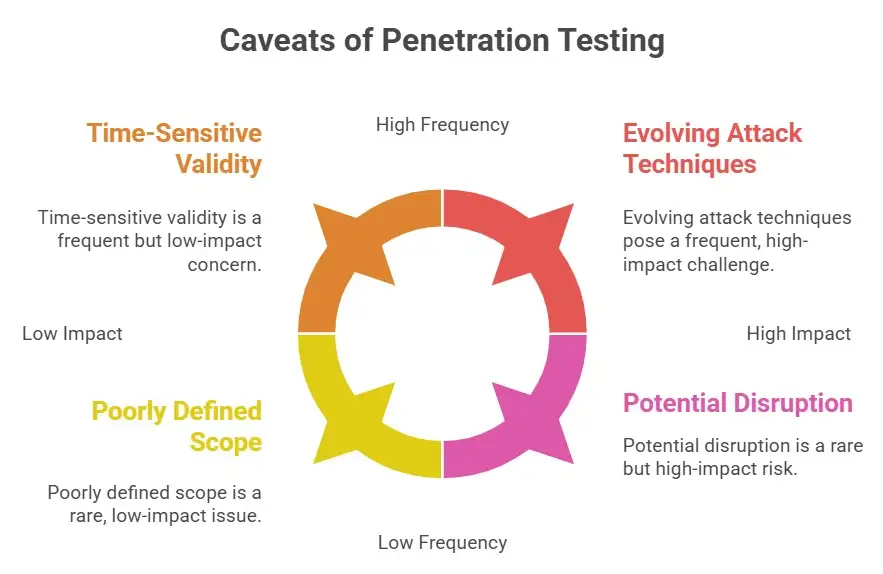
Challenges & limitations: the caveats of penetration testing, meaning
Of course, penetration testing is not a silver bullet. Understanding penetration testing's meaning also means appreciating the caveats:
· A penetration test is only valid for the point in time you conduct it. Tomorrow, you may have new vulnerabilities.
· It can be expensive and time‑consuming depending on the scope. Many companies cite cost as a barrier.
· If poorly defined, the scope may miss key areas (e.g., cloud or IoT).
· It may disrupt if not carefully managed. You are simulating attacks after all.
· It does not guarantee you are future‑proof. Attack tools and techniques evolve. The meaning of penetration testing must evolve, too.
So part of the meaning is also risk awareness: you are doing this to improve, not to say, “We are now 100% safe.”
Trends & emerging themes: how the meaning is evolving
Exploring “penetration testing meaning” today must include how it is changing. A few key trends:
· Continuous and automated testing: It’s no longer “once a year” for many orgs. Software‑based and automated platforms allow a higher cadence.
· Cloud, hybrid, and IoT surfaces: As more organizations shift away from traditional on‑premises, penetration testing must cover cloud, third‑party, mobile, and IoT.
· Social engineering & human‑centric attacks are becoming more important than just technical scans.
· Integration with DevSecOps / secure development lifecycles: Meaning it now includes testing early in build cycles, not just at the end.
· Rise of Penetration Testing as a Service (PTaaS): On‑demand platforms, flexible models.
These trends show that the meaning is broadening. A pen test used to be a “snapshot scan.” Today, it’s becoming a continuous, integrated security practice.
How to choose and plan for a penetration testing exercise
If you’re asking, “What does penetration testing mean for my organization?” Here are some practical considerations:
· Define clear objectives: Which systems, what outcomes, what risk level? This clarifies the meaning beyond generic.
· Choose the right type: Do you want a web app only? Or network plus social engineering? Pick accordingly.
· Scope and rules of engagement: Decide what is in and out. Without this, the meaning can get lost.
· Ensure the testers are qualified and follow recognized methodologies (e.g., standards from NIST, NCSC, etc.).
· Budget and timeline: The more extensive the system, the more resources.
· Plan remediation: The value of the test lies in fixing what was found. Penetration testing's meaning includes the “what happens next.”
· Communicate the findings to both technical and business audiences: Executives need to know risk, and teams need to know details.
If you do all this, you ensure your understanding of penetration testing's meaning turns into real action, not just a checkbox.
Actionable insight: making the most of your testing
Here’s some advice I’ve picked up through working with teams:
· Don’t treat the penetration test as “we’ll tick it off and forget.” Make it part of your security culture.
· After the test, map the findings into your project backlog, assign owners, and track fixes. That follow‑through gives meaning.
· For smaller organizations, risk‑based testing is key: you don’t need to test everything every time. Focus on critical assets.
· Use the results to educate your people: the human factor often is the weak link.
· Re‑test once remedial work is done. The meaning of the test includes proving you fixed the issue.
· Keep pace with evolving environments: If you move to the cloud, update the scope. Meaning shifts with your infrastructure.
When you think of “penetration testing meaning,” it should be inclusive of planning, execution, remediation, and continuous improvement.

Final thoughts and takeaways
We started with the idea of inviting a burglar to your shop to test your locks. That metaphor sticks because it shows the human element. The phrase “penetration testing meaning” goes beyond a technical definition; it stands for a mindset shift in cybersecurity. It means facing your vulnerabilities deliberately, simulating real attacks, and making your defenses stronger because of what you learn.
More than one company I’ve seen treated it as a compliance chore: “We did our pentest for the year.” But that misses the richness behind the meaning. Done well, it becomes a powerful tool for insight, for culture change, and for aligning business risk with technical reality.
So if you’re thinking about that next penetration test, ask yourself: what do I want it to mean for us? Do I merely want “we checked boxes” or do I want “we found how an attacker would break in, and we fixed it”? The second is where real value lies.
In short, penetration testing's meaning is not just about running tests; it is about learning how you would be attacked, accepting the findings, and improving because of them. Get that right, and you’ll get far more than a report; you’ll get resilience.
Let’s wrap with one final takeaway: make your next test count. Define your objective, treat it as a story (you against the attacker), bring in the fix, and then elevate your security posture. That is the full meaning of penetration testing.
FAQ: Penetration Testing
1. What is penetration testing with an example?
Penetration testing is like inviting a professional to test your security as if they were a hacker. They try to break into your systems, websites, or networks to show where you are vulnerable. For example, a tester might examine an online store’s login page and discover that weak passwords could let someone access customer accounts. This gives the business a chance to fix the issue before a real attacker finds it.
2. What are the 5 stages of penetration testing?
A penetration test usually follows five stages. First is planning and reconnaissance, where testers gather information and define the scope. Second is scanning, which involves identifying open ports, services, and potential weak spots. Third is gaining access, where the tester exploits vulnerabilities to enter the system. Fourth is maintaining access, which explores how far an intruder could move within the network. Finally, analysis and reporting summarize the findings and suggest steps to fix the issues.
3. How is a penetration test performed?
Performing a penetration test starts with planning. Testers define objectives and establish rules so nothing critical is damaged. Then comes information gathering and scanning, followed by controlled exploitation of weaknesses. The final step is reporting, where results are presented clearly along with practical solutions. The process is careful, systematic, and realistic.
4. How do you do a standard penetration test?
A standard penetration test begins by defining the scope and rules. Next comes reconnaissance to collect information, then scanning to identify weaknesses. Testers then try to exploit these vulnerabilities in a controlled environment. The final stage is a detailed report that helps the organization strengthen its security. Each step is designed to mimic a real-world attack scenario safely.
5. What is the first step in a penetration test?
The first step is planning and reconnaissance. Testers need to know exactly what they are testing and gather as much information as possible. This is similar to mapping a building before attempting to test its security. Without this step, the rest of the test would lack focus and effectiveness.
6. What are the phases in the penetration testing lifecycle?
The lifecycle consists of planning, reconnaissance, scanning, exploitation, and reporting. Each phase is important. Planning sets the rules. Reconnaissance finds the weak spots. Scanning identifies details that can be exploited. Exploitation tests the actual risk, and reporting ensures the organization knows exactly what to fix.
7. Penetration testing tools
Various tools help testers perform penetration testing. Nmap is used to scan networks. Metasploit allows controlled exploitation of vulnerabilities. Burp Suite tests web applications, and Wireshark analyzes network traffic. Choosing the right tool depends on what is being tested and the goal of the penetration test.
8. Penetration testing example
Imagine a company has a web application for customers. A penetration tester discovers that the checkout page is vulnerable to SQL injection. By exploiting this flaw, they show that sensitive customer information could be accessed. The company then patches the weakness and improves overall security. This example shows how penetration testing directly prevents possible attacks.
9. Penetration testing in cybersecurity
In cybersecurity, penetration testing is a proactive approach. Instead of waiting for hackers, companies simulate attacks to uncover weaknesses in networks, systems, and applications. It is not just a technical exercise. It also educates teams and prepares them for real-life attacks.
10. Types of penetration testing
There are several types of penetration testing. Network testing examines internal and external networks. Web application testing focuses on websites and APIs. Wireless and IoT testing checks smart devices and Wi-Fi systems. Social engineering targets the human element, and cloud testing evaluates cloud infrastructure. Each type addresses different risks.
11. What is the purpose of penetration testing?
The purpose is to identify and exploit vulnerabilities to understand the real risks. It allows organizations to fix issues before attackers exploit them. Additionally, it supports regulatory compliance and builds confidence in the company’s security practices.
12. Penetration testing vs. vulnerability assessment
A vulnerability assessment identifies potential weaknesses. Penetration testing goes further by attempting to exploit those weaknesses. Think of it as the difference between being told a door is unlocked and actually seeing someone open it and enter. Penetration testing provides a practical view of risk.
Penetration testing helps you find security gaps before hackers do. By simulating real attacks, it uncovers vulnerabilities and provides clear steps to fix them, keeping your systems and data safe.
You can also read these important cybersecurity news articles on our website.
· Apple Update,
· Windows Fix,
For more, please visit our homepage and follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates.
Share this :