Scattered LAPSUS$ Hunters: Dark Web Leak Site Shutdown

Hoplon InfoSec
27 Oct, 2025
When the world hears about large-scale hacks and black-hat forums, the phrase “scattered LAPSUS$ Hunters” has recently started to surface, and for good reason. This alliance of cybercrime actors, blending the notorious tactics of LAPSUS$ with other groups, triggered a chain reaction: a major onion leak website they used was taken down by law enforcement agencies.
The story matters not just because of the skill of the hackers, but because of how authorities acted and what it says about the future of dark-web leak operations.
Who Are the “Scattered LAPSUS$ Hunters”?
The term “Scattered LAPSUS$ Hunters” refers to a newly identified alliance. According to threat-intelligence firm Picus, this group brings together aspects of three organized threat actors: Scattered Spider, LAPSUS$, and ShinyHunters.
· From Scattered Spider they draw expertise in initial access, especially via help-desk social engineering.
· From LAPSUS$, they inherit notoriety for insider recruitment and source-code theft.
· From ShinyHunters they borrow large-scale data exfiltration and extortion-style leak operations.
In effect, this “supergroup” capitalises on the strengths of each to orchestrate bigger and more ambitious campaigns than any one of them might alone.
What Happened: The Onion Leak Website & Extortion Platform
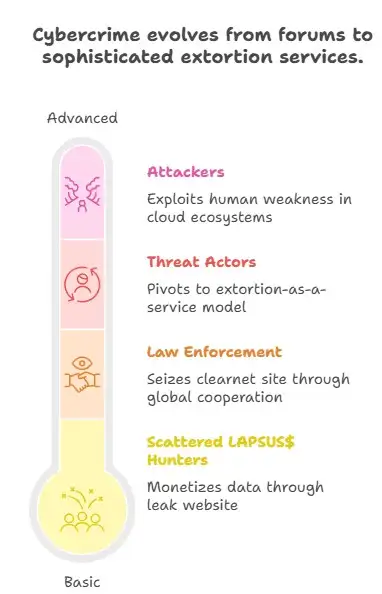
One of the most significant moves by Scattered LAPSUS$ Hunters was the running of a leak portal (sometimes via the onion/Tor network) to publish stolen data and extort victims, commonly firms using cloud-SaaS platforms like Salesforce.
In October 2025, the clearnet domain (for example, breachforums[.]hn, successor of the infamous BreachForums) was seized by the FBI in the United States, in cooperation with France’s cybercrime unit and the Paris Public Prosecutor’s Office.
However, while the forum’s domain was seized, the onion (Tor) version of the leak site remained operational for a time.
It is worth noting that the group threatened to release as many as 1 billion records tied to a Salesforce breach if ransom demands were not met.
Why This Shutdown Matters
This case illustrates several evolving dynamics in cybercrime and law enforcement response:
1. Leak Sites Are No Longer Just Forums. The shift from “discussion board” style forums to active extortion-and-leak portals shows how threat actors are monetizing stolen data. For example, “Scattered LAPSUS$ Hunters” leveraged a leak website as part of its campaign.
2. Law Enforcement Coordination. The joint action by U.S. and French authorities underscores the global nature of cybercrime and the necessity of cross-border cooperation. The seizure of the clearnet site is a real ‘take‐down’ moment.
3. Adaptation by Threat Actors. Even after domain seizure, the group appears to pivot, announcing a temporary dissolution and hinting at new models such as “extortion-as-a-service” (EaaS).
4. Risk to Cloud/SaaS Ecosystems. The targeting of SaaS platforms like Salesforce (via social engineering rather than just software flaws) highlights how attackers are exploiting human and organizational weakness, not just technical vulnerabilities.
How They Operated: Key Techniques
The group’s tactics (sometimes derived from its constituent parts) include:
· Voice-phishing (vishing) / social engineering: Attackers posed as IT help-desk staff and persuaded targets to approve malicious integrations in Salesforce or other SaaS tools.
· MFA fatigue / tricking multi-factor flows: Rather than brute force, they coerced users into approving suspicious login attempts or resetting MFA.
· Use of insider access or vendor third-party access: Recruitment of employees or contractors with privileged access.
· Public leaks & extortion platforms: Once data was obtained, the leak website would publicly list victims, set deadlines, and demand ransom payment to avoid publication.
What’s Next: Implications & Takeaways
For organizations and individuals alike, what does this mean?
· If you are part of a company using SaaS or integrated cloud services, assume that attackers can bypass technology simply by exploiting human or process weaknesses.
· Leak-site takedowns are helpful, but they are not the end of risk. Threat actors adapt, move to onion domains or new platforms, and shift business models (e.g., EaaS).
· For law enforcement, the seizure of domains is a potent tool, but the underground economy remains resilient; proactive detection and preventive controls matter.
· For the public/consumers whose data may have been compromised: data exposure from such super-groups can linger long after the headline incident is over.
Final Thoughts
The story of scattered LAPSUS$ Hunters and the leak website taken down by law enforcement agencies marks a milestone in cyber-threat evolution: an alliance of older threat groups, wielding public leak platforms, targeting SaaS environments, and forcing organizations into extortion negotiations.
The shutdown of their clearnet domain was a victory for the authorities, but the underlying threat remains and may well move into new forms. Organizations must not relax. Awareness, rigorous controls, and incident readiness are vital as attacker alliances continue to evolve.
If you’d like, I can pull together a timeline of the major incidents tied to this group or map out the victims and how they responded. Would you like that?
FAQs
Q1: What is scattered in “Scattered LAPSUS$ Hunters”?
In this context, “scattered” reflects the fusion of disparate cyber-groups and tactics into a scattered / distributed operation rather than one fixed site or method. It doesn’t refer to scattered thunderstorms or weather phenomena.
Q2: What is LAPSUS$?
LAPSUS$ is a previously known cyber-extortion group that gained attention for source-code theft and insider recruitment attacks (for example, the breach of identity-provider Okta in 2022).
Q3: What exactly does “LAPSUS$ leak website taken down” mean?
It refers to the seizure of clearnet domains used by the group for publishing stolen data and extortion demands. Although the onion versions may persist, the visible public leak site was disrupted by law-enforcement.
Q4: Will the shutdown permanently stop the threat from the group?
Not necessarily. The group has publicly announced a temporary dissolution (possibly until 2026), suggesting they may regroup under different structures or platforms.
Q5: What can companies do to protect themselves against groups like these?
Focus on strong processes around help-desk access, MFA approval policies, vendor/third-party access controls, regular auditing of cloud integrations, and training to resist social engineering. Technological controls matter, but so do human and process controls.
Hoplon Infosec protects organizations against threats like Scattered LAPSUS$ Hunters through
also ensures proactive threat detection and strong cybersecurity frameworks.
You can also read these important cyber security news articles on our website.
· Apple Update,
For more Please visit our Homepage and follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well.
Share this :