Tsundere Botnet abuse: Ultimate 2025 Threat Guide
Hoplon InfoSec
21 Nov, 2025
Think of yourself as a software developer who uses npm to install Node.js libraries regularly. One day, a bad version of a popular package sneaks into your workflow. It's not obvious or loud, but it's deadly.
This isn't science fiction: the Tsundere Botnet abuse is becoming a serious threat that mixes Web3 infrastructure with supply-chain compromise. In the middle of 2025, Kaspersky researchers found a botnet that uses Node.js packages and Ethereum smart contracts to attack people who use Windows, Linux, and macOS.
What is the Tsundere Botnet?
The Tsundere Botnet abuse is a campaign in which a hacker builds a network of infected computers (a botnet) by putting harmful code into Node.js ecosystems. Instead of using traditional methods to spread malware, this person made typosquatting npm packages, which are packages that look like real ones, to fool developers.
Kaspersky's Global Research & Analysis Team says that the botnet came back to life around July 2025, but it started with a supply-chain attack in October 2024 when 287 bad npm packages were found.
Why the Tsundere Botnet Abuse Is Important
This isn't just another virus. The Tsundere Botnet abuse is important because it takes advantage of two big trends:
Supply-Chain Risk: Attackers can get to developers on Windows, Linux, and macOS by adding malicious code to npm packages. They don't have to phish each victim individually.
2. Resilience Based on Web3: The botnet keeps its command-and-control (C2) addresses on the Ethereum blockchain instead of using fixed domain names. That means the attacker can easily change or update servers by calling a smart contract.
This mix makes the Tsundere Botnet abuse very adaptable, long-lasting, and hard to stop.
A step-by-step guide to how the Tsundere Botnet works
This is a step-by-step guide to how this botnet works, from getting infected to taking over:
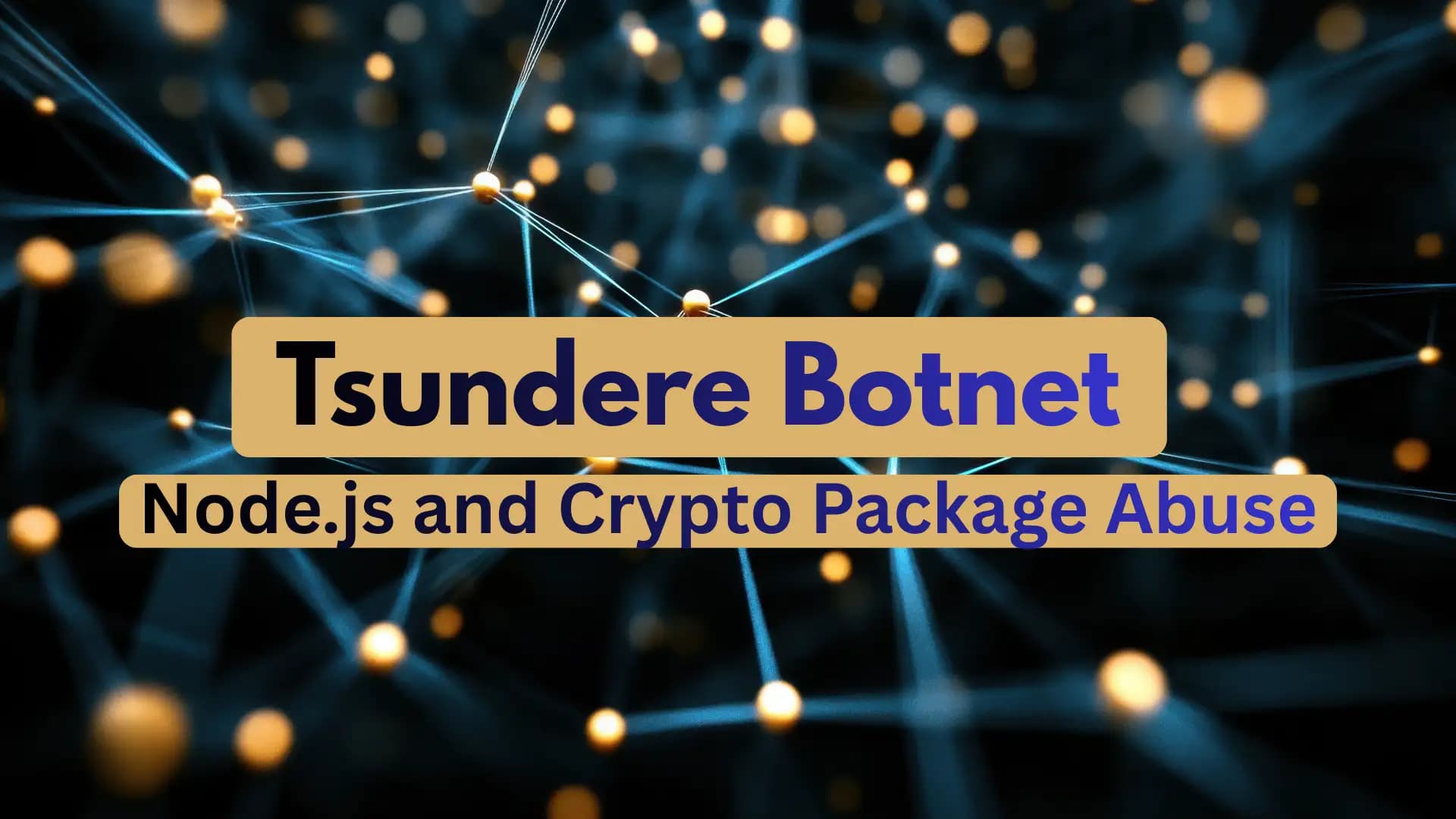
The first way to get infected is by tricking victims into running an MSI installer that looks like a setup file for popular games like Valorant, CS2, or R6X.
In some cases, a PowerShell script is used. This script gets Node.js from the official Node.js website, installs it in AppData\Local, and then sets up the bad bot.
2. Setting Up the Runtime After being deployed, the bot installer makes a Node.js environment on the user's computer, complete with node.exe and other tool files.
Then it runs a loader script that uses AES-256-CBC to decrypt encrypted artifacts, rebuilds the malware, and gets node_modules ready.
3. Installing Dependencies with npm: The bot uses real Node.js packages to stay connected to the network and stay alive. Using npm install, it installs ws (a library for WebSockets), ethers (for interacting with Ethereum), and pm2 (a process manager).
o pm2 lets the bot restart on its own and keep running even after a reboot.
4. Ethereum-based command and control
The bot always asks an Ethereum smart contract (on-chain) for the current WebSocket C2 address. o This design lets the attackers change control servers by just writing a new address into the smart contract.
When it connects, the bot listens to encrypted messages. When it gets JavaScript code, it runs it right away, giving operators the freedom to change things on the fly.
5. The Control Panel and Marketplace
The Tsundere infrastructure has a web-based control panel (version 2.4.4) that anyone can sign up for.
You can turn infected computers into proxies, SOCKS bots, or custom versions that you can sell.
The panel is also connected to a marketplace where hackers can make and share new versions or sell access.
Example from real life
Kaspersky researchers saw one infection that started with a Remote Monitoring and Management (RMM) tool. The tool connected to a hacked server and downloaded a file called pdf.msi. This file was a loader for the Tsundere bot.
In another case, fake MSI installers tricked gamers into installing pirated or cracked versions of games like Valorant or CS2. The installer included a Node.js runtime and the Tsundere payload, and it ran in the background without anyone noticing.
Risks and Results
The Tsundere Botnet abuse poses numerous significant threats:
• Persistent Access: The bot uses pm2, which means that once it is installed, it stays alive and restarts on its own, making it hard to get rid of.
• Dynamic Control: Using Ethereum smart contracts for C2 makes it hard to shut down or take down.
• Supply-Chain Reach: Developers who install npm packages might accidentally add the bot to their own infrastructure or supply chain.
• Cross-Platform Infection: This botnet is not limited to Windows, like many other types of malware. Evidence shows that past malicious packages also targeted Linux and macOS.
• Abuse of the Marketplace: Because the botnet has its own service marketplace, other bad actors can build on it and make it bigger.
How to Protect Yourself from Tsundere Botnet Abuse
To keep systems safe from this kind of attack:
1 . Check npm Dependencies
Always use official package registries that have been curated.
Don't install packages that you don't trust or that have typos in their names. Watch out for libraries with names that are similar.
Use tools like npm audit or supply-chain scanners that find bad or suspicious packages.
2. Keep an eye out for strange installs.
Be careful of MSI installers that come from unknown sources, especially if they look like game installers.
Check that PowerShell scripts that install Node.js are correct. Make sure the signatures are from people you can trust.
3. Use security solutions for endpoints.
Install trusted antivirus or anti-malware software that can find Node.js exploits or hidden scripts.
Monitor how applications behave. If you see persistent processes that create hidden Node.js, it could be a sign of trouble.
4. Use threat intelligence that knows about blockchain.
Because Tsundere uses Ethereum smart contracts, security teams can keep an eye on the right contract addresses and see when they change.
Adding blockchain threat intelligence to your detection system could help you find threats sooner.
5. Use the Principle of Least Privilege.
Only run Node.js or npm commands as an administrator when you really need to.
Make sure that only certain people can install software or run scripts on your systems.
References and tools for the industry
• Kaspersky GReAT: Their in-depth report revealed a lot about the structure of the Tsundere botnet.
• Ethereum Explorer / RPC Services: These can help defenders keep an eye on changes to smart contracts.
• Tools for Supply Chain Security: Tools like npm audit, Snyk, OSS-Fuzz, or Phylum (or something like them) can help you find bad packages or packages with typos.
• Endpoint Monitoring and Process Managers: These tools can find strange pm2 usage or Node.js runtime behavior that isn't expected.
Wrap up
The Tsundere Botnet abuse is an example of how modern hackers are combining supply-chain attacks with Web3 infrastructure.
This botnet shows a new level of sophistication by hiding bad code in npm packages, using Ethereum smart contracts for resilience, and using common lures like game installers.
It is a strong reminder that software developers and security teams need to be extra careful, especially in open systems like Node.js. Strong dependency hygiene, careful monitoring, and threat intelligence integration are the best ways to protect both traditional systems and blockchain. Our security plans need to change as Tsundere does.
FAQs
Q1: What kinds of computers does the Tsundere botnet attack?
People who use Windows, Linux, and macOS have been affected by the Tsundere botnet abuse.
Q2: How does the botnet find its command-and-control (C2) addresses?
It keeps its C2 WebSocket addresses on an Ethereum smart contract. Bots that are infected use RPC providers to ask this contract for the current C2 URL.
Q3: What does the name "Tsundere" botnet mean?
The name comes from the control panel, "Tsundere Netto," and it may show that the botnet has two sides: it looks nice at first, but is dangerous underneath.
Q4: What can developers do to protect themselves from this kind of botnet abuse?
To avoid typosquatting, developers should double-check package names, use dependency auditing tools, trust registries, and keep npm package installations very secure.
You can also read these important cybersecurity news articles on our website.
· Apple Update,
Author: Hoplon Infosec
Bio: Security enthusiast with over 10 years in mobile cybersecurity. Connect with me on LinkedIn.
Address: 1415 W 22nd St Tower Floor, Oak Brook, IL 60523, United States
Phone: +1 773-904-313 , Contact: [email protected]
About/Privacy: At Hoplon Infosec, we provide expert insights into cybersecurity. Our editorial policy: all articles are written by in-house specialists or thoroughly reviewed by them to ensure accuracy, credibility, and up-to-date information.
Share this :