U.S. DOJ ATM Hacking Charges Expose Ploutus Malware Cash-Out Attacks
Hoplon InfoSec
22 Dec, 2025
How did one ATM malware operation get so big that the U.S. Department of Justice charged 54 people? What does this case show about the real risks that banks face today?
In December 2024, the U.S. Department of Justice confirmed charges related to a coordinated ATM hacking campaign that used Ploutus malware, which is one of the most dangerous tools ever used to steal money from ATMs. Cybersecurity News has confirmed that this case shows how organized cybercriminals took advantage of weaknesses in ATM systems across borders without making a big deal out of it.
This isn't a story about small-time fraud or card skimmers. It talks about how cybercriminal groups turned ATMs into cash machines that can be controlled from a distance.
What the U.S. DOJ ATM hacking charge really means
The U.S. DOJ's charges of hacking ATMs are one of the biggest coordinated law enforcement actions against people who make ATM malware so far. Prosecutors say that dozens of people were part of a structured criminal network that went after ATM infrastructure directly instead of customers.
This is important because people often don't understand ATM malware attacks. A lot of people still think that ATM fraud means stealing cards or looking over someone's shoulder to get their PIN. This case shows that the threat is much more serious and complicated.
According to court documents and public statements, the people who were charged were linked by logistics, deploying malware, and cashing out. Some took care of the malware itself. Some people acted as mules and took cash out of machines that had been hacked. The DOJ hasn't said publicly what all the technical methods were, but investigators have confirmed that Ploutus ATM malware was involved.
Who Was Involved and How the Network Worked
It wasn't just a bunch of hackers doing their own thing. The way the structure worked was like a business. The Ploutus malware was made or changed by developers. Access brokers found ATMs that were easy to break into. Field operators went to the machines and told them to give out cash. Mule networks took care of withdrawals and money laundering.
The fact that international cooperation was involved in the U.S. DOJ ATM hacking charges makes them stand out. Several of the defendants were involved in activities that crossed borders. This is part of a larger trend in which ATM malware groups work all over the world, taking advantage of weaknesses in local ATMs.
Not all of the suspect's roles have been made public. In situations like this, DOJ disclosures usually focus on actions that can be proven instead of revealing sensitive investigative methods.

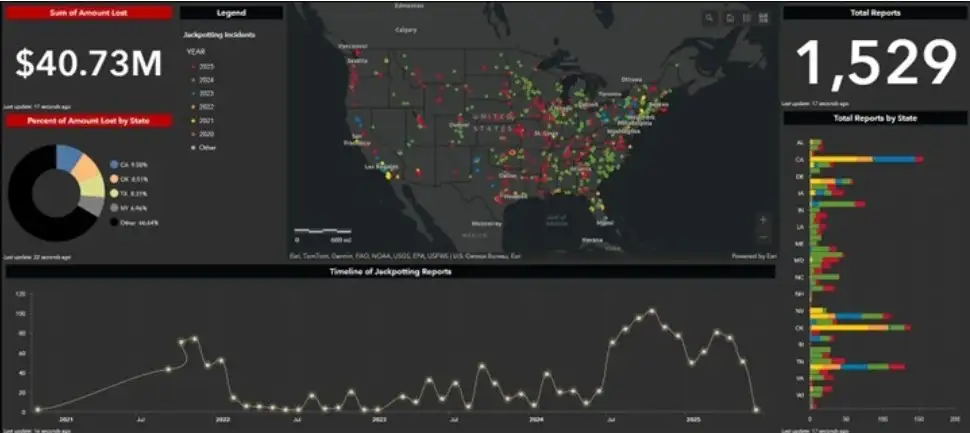
Certain suspected ATM burglaries were still in progress (source: justice.gov)
Why This Case Is More Important Than Other ATM Arrests
In the past, ATM hacking cases usually only had a few suspects. Charging 54 people sends a strong message. This shows that police no longer see ATM jackpotting as a rare type of cybercrime.
It also proves that Ploutus malware is not a threat from the past. It is changing all the time. The DOJ's actions suggest that investigators kept an eye on this network for months, maybe even years, before taking action.
This case clears up any doubts for banks and ATM operators. Malware for ATMs is real. It is organized, works, and makes money.
How Ploutus Malware Makes ATM Jackpotting Possible
The goal of Ploutus malware is to take over the ATM software directly. Ploutus is different from skimming devices because it doesn't steal data; it controls the machine itself.
Based on confirmed research and past investigations, here is a simple explanation of how these attacks usually work.
• Attackers get physical or logical access to an ATM.
• Malware is put on the ATM's operating system.
• The malware stops legitimate transaction processes.
• Cash-out commands are sent out manually or remotely.
• In just a few minutes, money mules can take out a lot of money.
This kind of attack is called an ATM malware cash-out attack. It skips over all customer accounts.
Making Technical Reality Easy
Most ATMs still use old operating systems and security controls that aren't up to date. Once attackers get into the internal system, Ploutus malware can talk directly to the hardware that dispenses money.
In some cases that have been reported, attackers used USB ports that were hidden inside ATM cabinets. In some cases, network problems made it possible for people to access the network from afar. The DOJ hasn't said which methods were used in each case related to the U.S. DOJ ATM hacking charges, but both methods are well known from past Ploutus campaigns.
Why Banks Don't See These Attacks Right Away
It doesn't take long for ATM jackpotting to happen. A machine may give out money for five minutes and then look normal again. If monitoring systems aren't very good, banks might think at first that the loss is due to a mechanical error.
This delay is good for criminals. The mule network has already moved on by the time investigators see a pattern.

The Bigger Risk to Banks and the Financial System
This case reveals unsettling realities regarding the security of banking infrastructure. Many ATM fleets still use old software. The patch cycles are slow. The level of physical security varies greatly from place to place.
The U.S. Department of Justice's charges of ATM hacking show that financial institutions are under more and more regulatory pressure. More and more, prosecutors see weak ATM security as a systemic risk rather than just a technical problem.
From a risk management point of view, ATM malware attacks are a mix of cybercrime and real-world crime. That makes it harder to find and stop them.
How Malware as a Service Changed Everything
Ploutus is no longer just one type of malware. People have been selling it as a service on the black market. This makes it easier to get in. Criminals don't need to be very good at computers anymore. They can rent tools and follow plans.
This way of doing business explains how networks get so big. Developers grow. Operators have their own areas of expertise. It's easy to find new mules.
Example Case: A Realistic Cash-Out Situation
Picture an ATM in a small shopping center late at night. A uniform for a technician looks real. The door to the cabinet opens. Put it in a USB device. No alarms.
The machine starts giving out cash on command ten minutes later. A mule takes out a few thousand dollars. The ATM looks like it hasn't been used by morning.
Do this in many different places. That's how losses quietly grew to millions before the U.S. Department of Justice looked into the ATM hacking charges.
Making a comeback around the world. In 2024, the DOJ will take big action against it.
Most Important Risk Factors Found
ATM operating systems that are out of date
Poor controls on who can access the system inside
Not enough real-time monitoring and not enough cooperation between banks and law enforcement
These trends match what the news and experts say, but the exact numbers are different in different areas.
H2 Questions and Answers
What is the Ploutus virus?
Ploutus malware is a type of ATM malware that lets hackers take direct control of cash machines and make unauthorized withdrawals.
How does jackpotting work on ATMs?
Hackers put malware on an ATM and then send commands that make the machine give out cash without needing cards or accounts.
Who did the DOJ arrest in the case of hacking ATMs?
The U.S. Department of Justice charged 54 people who were involved in different roles in an organized ATM malware operation. Not all of the full names have been made public.
Can banks stop malware attacks on ATMs?
Yes. Strong access controls, up-to-date operating systems, real-time monitoring, and training for employees all lower the risk a lot.
Lesson
The charges against the U.S. DOJ for hacking ATMs are real. They are a sign. Malware that attacks ATMs is no longer a small-time cybercrime. It is well-organized, can grow, and makes money.
This case shows banks how much it costs to wait too long to upgrade. It makes regulators more aware of how important it is to hold people accountable. It makes it clear to the public that ATM security is about the infrastructure, not how people act.
The lesson here is easy to understand. Cybercrime changes slowly. Loudly, enforcement catches up. The best way to protect yourself is not to wait for the knock on the door.
Next step: If you are in charge of ATM infrastructure or financial risk, you should audit the systems now, not after the next indictment.
You can also read these important cybersecurity news articles on our website.
· Apple Update,
· Windows Fix,
For more Please visit our Homepage and follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well.
Share this :