Windows 11 New Security Feature Denies Unauthorized Access to System File Access

Hoplon InfoSec
02 Feb, 2026
What exactly is the new Windows 11 security feature that denies unauthorized access to system file access, and why should you care today?
On February 2, 2026, Microsoft quietly introduced a new Windows 11 security feature aimed at stopping unauthorized access to sensitive system file areas of the operating system. This update, included in the January 2026 preview release KB5074105, requires administrative approval before users can view or interact with high-risk system file areas, especially through the Storage settings interface.
This matters right now because it limits local or remote non-admin users from analyzing or altering system data structures without elevated permissions, a common vector for misuse in shared or enterprise environments.
What Happened and What the Update Does
Earlier in February 2026, Microsoft shipped the KB5074105 Windows 11 preview cumulative update for versions 24H2 and 25H2 that includes a stealth security enhancement. When trying to open certain system-related interfaces, like detailed storage settings, it triggers an administrative prompt via User Account Control (UAC) before entering.
If the account lacks admin rights, users are blocked entirely. This is a form of access hardening that goes beyond basic file permissions and enforces consent before even viewing structured system data that could otherwise be exploited by someone with physical or remote access to the PC.
This feature is rolling out in the “C-release” optional preview phase ahead of broader deployment in the mandatory Patch Tuesday updates. Businesses and power users should test the feature before it is made available to everyone else so that workflows that rely on seeing system files are not interrupted.
This change is part of a bigger security philosophy for Windows 11 that focuses on giving users the least amount of access and making it harder for attackers to get in. Windows 11 already has security features like Microsoft Defender, controlled folder access, and virtualization-based protections to keep devices safe.
Why Microsoft Is Tightening System File Access
System files and low-level settings in any operating system carry a lot of risk. In the past, users and malware could use built-in tools and scripts to get to the internals of a system, which could have exposed sensitive data structures or allowed unwanted changes.
Windows has had User Account Control for a while, but Microsoft has been working on how and when it works to make sure that administrative consent is given.
UAC limitations were historically circumvented by determined threats using token manipulation or abusing elevated sessions.
The latest Windows 11 security feature builds on this by enforcing administrative obstacles even for standard file browsing beyond classic user permission models. The goal is to make unauthorized access to critical system information much harder and to ensure that users with legitimate administrator rights explicitly confirm actions that touch protected system resources.
How This Affects Everyday Users
For typical home users, the impact will be subtle. Most people never navigate deep into system folders or storage breakdowns in the first place. If you are a standard user account without admin rights, you will now see a UAC prompt or be blocked when trying to access these areas.
This means for people who share spaces like libraries, schools, or even homes with more than one person:
• Windows 11 will stop accounts with fewer privileges from accidentally or purposefully getting into the system's inner workings.
• IT professionals will have a better idea of who can control access to core system files.
• Malware that runs under standard accounts without elevation will find it harder to collect system information or alter system structures.
In other words, security boundaries are being raised to align with modern threat tactics without requiring additional third-party security tools.
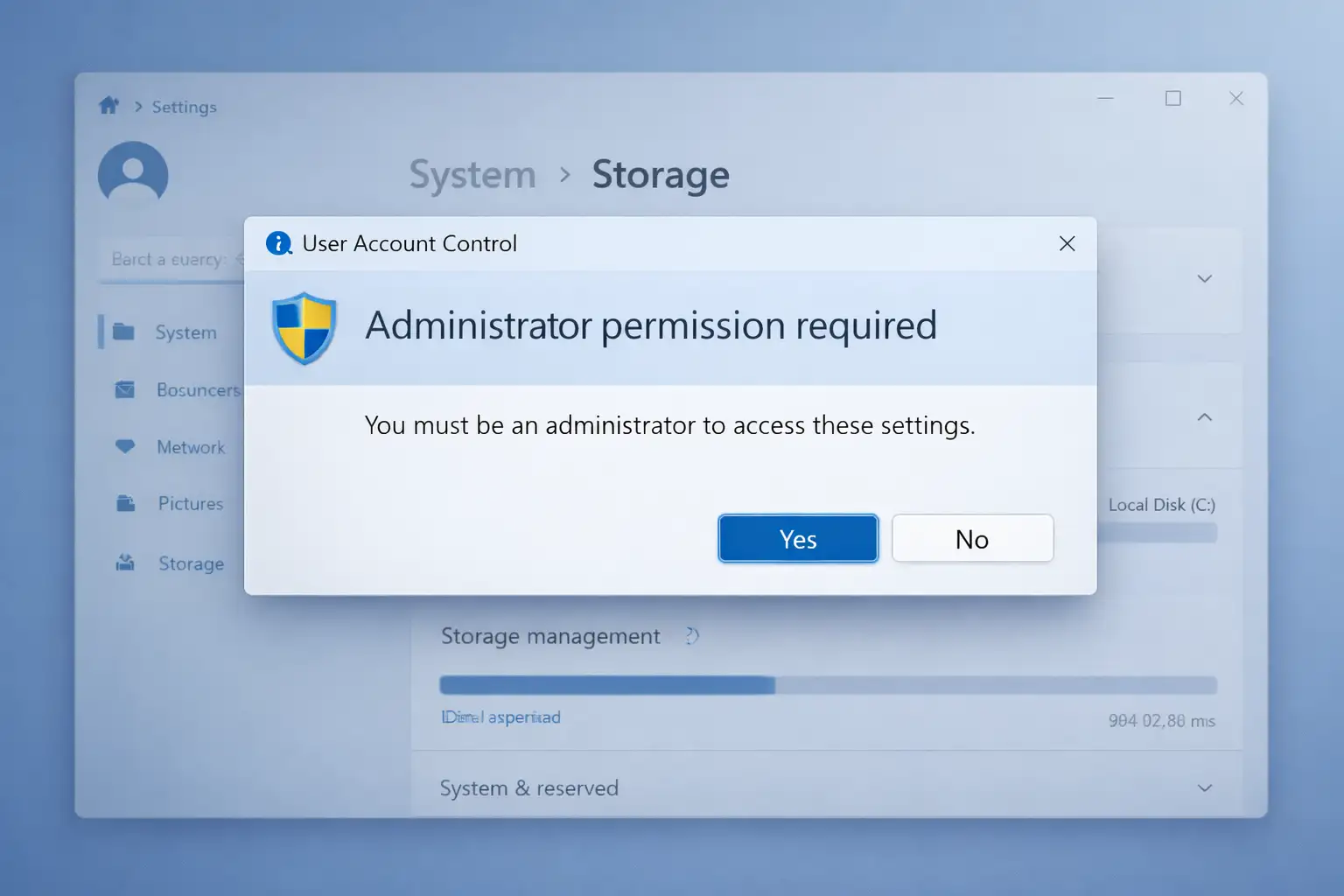
Example: Storage Settings Prompt
Before the update, anyone who could log into a Windows 11 session could open the Settings app, navigate to System → Storage, and see detailed file breakdowns, including system-reserved or temporary files. After the update, attempting the same action brings up an administrator approval dialog if the account is not elevated. Without admin credentials, Windows will refuse to continue.
This is not just a permission check on a file system level but a security checkpoint, like what IT administrators have long asked for to curb unauthorized system exploration in business or sensitive environments.
How This Fits Into Windows 11’s Larger Security Ecosystem
This Windows 11 new security feature is one of many steps Microsoft has taken to harden the operating system. Windows 11 already has built-in protections like these:
Controlled Folder Access protects user folders from malware and writes that aren't allowed.
Microsoft Defender Antivirus and Smart App Control check apps before they run.
Hardware-assisted security through TPM, secure boot, and virtualization-based security to isolate kernel and boot processes.
This latest block on unauthorized system file access is part of the same direction: protect the OS at every layer from unauthorized exploration or manipulation while preserving legitimate administrative workflows.
-20260202125954.webp)
What Windows Users and Administrators Should Do
Because this feature is currently in preview, administrators should:
Test the impact on enterprise images before wide deployment.
Look at automated scripts or tools that might need unrestricted access to settings or storage.
Teach regular users about the new UAC prompts they might see.
Home users don't need to do anything else but keep Windows up to date to get the latest security updates.
The Future of Windows System Security
This trend shows that Microsoft will keep making the line between standard and elevated privileges clearer. Future updates may require prompts in other sensitive configuration areas besides storage, or they may change how people can access common system tools.
Security in 2026 and beyond is not only about blocking known malware. It is also about reducing the ability of any unauthorized process or unauthorized account to glean deep system details or alter the OS without explicit user consent.
Frequently Asked Questions
Why does Windows 11 block access to system files now?
Because Microsoft has added a protective check in the latest preview update to enforce consent before allowing access to sensitive system file areas, reducing unauthorized interaction.
Will I still be able to access Storage settings if I am an admin
Yes. Admin accounts will be asked to approve access before they can continue.
No, this does not change file permissions in Windows. This security feature adds another layer of UAC checks before checking permissions.
Can this feature be disabled?
Since it is part of a preview update, it may be optional until it is included in a mandatory Patch Tuesday release.
Conclusion
This new feature in Windows 11 is another step in the right direction for security. It stops people who shouldn't be able to access system file areas of the operating system. Users get better protection against abuse, and administrators get clearer limits on what privileged operations can and can't do.
It is a sign that Windows security is increasingly proactive and that visibility into system internals is being intentionally guarded to match modern threats.
Read more related blogs:
Share this :