Zyxel Router Bug Lets Hackers Steal Device Settings

Hoplon InfoSec
26 Oct, 2025
You lock the front door, latch the rear gate, and padlock the windows, yet someone still gets in since the door's mechanism only examines the first few seconds of the knock. That is a bad comparison for a big issue in Zyxel routers that enables hackers to see and download all of the system's settings, even though there are two-factor authentication and other security safeguards in place.
This is a wake-up message for everyone who runs or owns a corporate network that includes Zyxel routers or firewalls: the key administration interface you trusted may not be as secure as you thought.
What is this weakness, really?
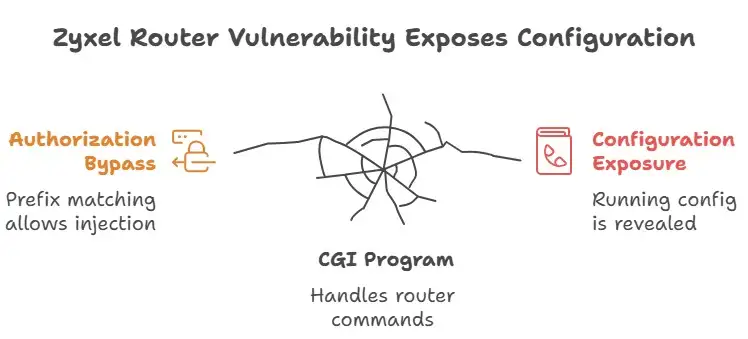
In summary, the problem is that some Zyxel firewall/router firmware lets a semi-authenticated user (someone who has passed the first level of login or 2FA) read and export full system configurations. CVE 2025 9133 is the official name for the vulnerability.
The term "Zyxel router vulnerability" captures this situation well: it enables attackers to acquire sensitive settings and credentials on Zyxel routers through the administrative interface without permission.
A little more information
• The Zyxel ATP and USG series devices were affected, such as the ATP series firmware going from V4.32 to V5.40 and the USG FLEX going from V4.50 to V5.40.
• The problem is that the web interface uses a CGI program named zysh-cgi that can handle commands like "show version" and "show running-config." The problem is that the system only analyzes the commands partially, utilizing prefix matching instead of full command validation. If an attacker sends show version; show running-config, the system lets it through since show version is allowed. Then it performs the extra command show running-config. The end effect was that the configuration was completely open.
• Timing: The advice was issued on October 21, 2025, but the problem was reported before that.
• Risk score: High. The CVSS v3.1 score for CVE–2025–9133 is around 8.1.
• Some of the most significant phrases we'll use are "Zyxel router vulnerability," "authorization bypass," "configuration exposure," "command injection," and "missing authorization."
A "Zyxel router vulnerability" isn't simply a vague term; it means that Zyxel's management interface instructions are broken, which makes even devices with two-factor authentication vulnerable.
Why this is important: it has genuine effects on the globe.
Let's put the pieces together to illustrate why this is crucial in simple terms. If you own a small business or are in charge of network hardware for a school, hospital, or corporation, your firewall is the gatekeeper. This kind of weakness in a Zyxel router implies that someone might get in, see the plans for your network, and even download them. What does that mean?
Data being shown
A lot of the time, those configuration files have admin passwords or hashed passwords, VPN settings, routing tables, firewall rules, and even TLS keys or certificates. Then, an attacker can figure out how your network works and plan future attacks. The firewall protects not just itself but also everything else.
Moving to the side and keeping still
Once they have the settings, an attacker can pretend to be the firewall, alter rules without anyone knowing, or build permanent back doors. You don't need full admin rights to initiate the vulnerability. A "semi-authenticated" user with lower rights can start the procedure because the check for authorization isn't finished.
There is no more trust.
We commonly believe that two-factor authentication (2FA) keeps "someone from logging in without permission." You can't be confident you're completely safe here, even with 2FA, because the problem happens before full verification. That makes consumers less convinced about how safe the equipment is and highlights how a "Zyxel router vulnerability" could be concealed behind a secure login.
Many people are affected.
A lot of small and medium-sized enterprises and big businesses utilize Zyxel gear as a firewall and UTM solution because it is a "good value." This kind of security breach can hurt a lot of organizations, not just a handful that are really important. The danger footprint is higher since so many people want the device.
You can lock your front door and set the alarm, but if the latch is wired wrong, an invader could get in through a service hatch that you didn't know was there.
How the attack works
Let's look at how a threat actor might leverage this "Zyxel router vulnerability" from both the attacker's and defender's points of view.
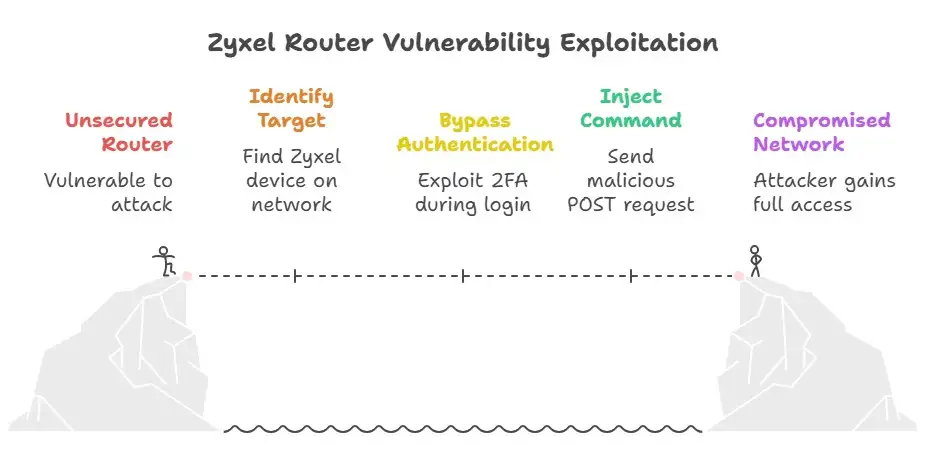
From the attacker's side
1. The attacker sees a Zyxel ATP/USG device that is connected to the network, either because it has an internet-facing management port or because it can be contacted from the internal network.
2. They create a new user account or use an existing one that has already completed the "first stage" of logging in (username/password) or a lower-privilege account with 2FA set on but not yet confirmed.
3. While they are still on the OTP/2FA stage (before the second factor is validated), they submit a specific POST request to /cgi-bin/zysh-cgi with arguments like filter=js2&cmd=show version;show running-config&write=0. The request goes through since "show version" is allowed when the state is semi-authenticated. The semicolon injection enables the whole display running-config work.
4. The device sends back configuration data in JavaScript serialized form (zyshdata* arrays), which provides everything the attacker needs.
5. The attacker downloads the data, uses it to map the network, seeks for passwords or keys, and then goes after another target.
The defender's point of view
• The check for authorization is erroneous since it only checks the prefix of the command text, not each subcommand that is separated by semicolons.
• The system doesn't stop semicolon chaining or command separators; thus, the attacker can add commands that aren't allowed to a prefix that is.
• The system believes the attacker is still "in progress" because they are at the stage before full 2FA completion and trusts the short allow list.
• The backup endpoints (export-cgi or file_upload-cgi) do have tougher checks (they send you to log in), but the zysh-cgi endpoint does not.
• The software path branch for semi-authenticated user type (usr_type = 0x14) only lets a few items through. But chaining breaks it because it only matches the beginning of the command string.
Think of a hotel door guard who lets you in if you show them the stub of your room key. But as soon as you present it to him, you slide through a sliding panel that he can't see. The security at the door just checks you once, when you show them the stub.
After that, you can go in without any more checks. This is how the "Zyxel router vulnerability" works: the guard checks the first portion of your command and then lets you do the rest without inspecting it.
Who is in danger, and how bad is the danger?
It's really important to find out if you could be affected. In a general sense, a "Zyxel router vulnerability" isn't really hazardous. It all depends on what devices you use and how you set them up.
Models and firmware that are broken
As per public warnings:
• ATP series: firmware versions go from V4.32 to V5.40.
• USG FLEX series: Firmware versions go from V4.50 to V5.40. The USG FLEX 50(W) series has firmware versions from V4.16 to V5.40USG20(W). -VPN series: firmware versions V4.16 to V5.40. If your devices in this series are running older versions or even 5.40, you're in the zone.
The advice is also on Zyxel's official security list as "CVE-2025-9133."
Which groups are most likely to get hurt?
• Small and medium-sized enterprises (SMBs) that use Zyxel firewalls to keep their networks safe.
• Companies that can control their systems from afar, where the management interface is available online.
• Service providers or branch offices that employ Zyxel gear, where supervision may not be as strong.
• It's safe enough to surf the web from a distance or utilize two-factor authentication.
In summary, anyone who owns a Zyxel firewall or router with an easy-to-use control interface and doesn't have the most up-to-date software might think they might be at risk.
Why the amount of the risk matters
The weakness doesn't need complete authentication or admin credentials, which makes it easier for an attacker to get in. The "Zyxel router vulnerability" is more than "just another patch" when you consider that Zyxel is utilized by a lot of small and medium-sized enterprises as well as large ones.
If a hacker gets the setup, they can acquire anything, including keys, usernames, firewall rules, VPN information, and more. That's not simple.
If you manage or depend on Zyxel devices, you need a clear plan of action. You should wish to repair the problem immediately soon when you hear the words "Zyxel router vulnerability." Do the following:
What to do immediately now
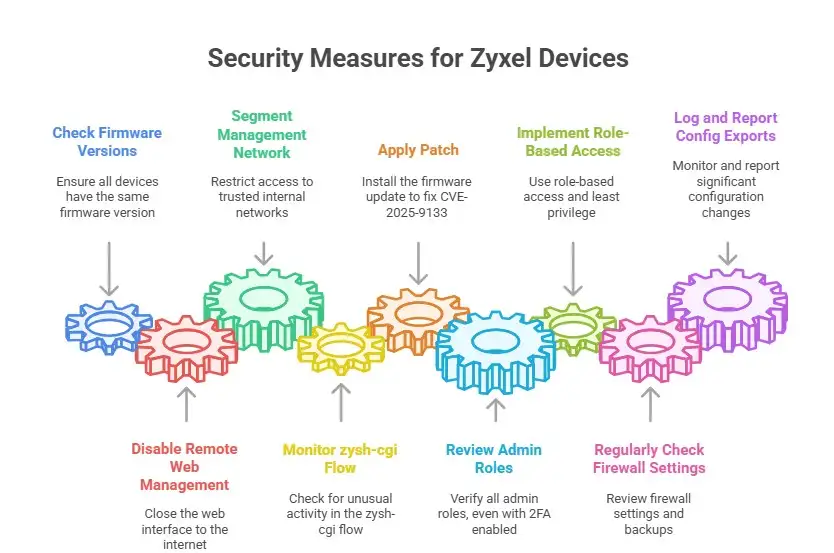
1. Check the firmware versions: make sure that the firmware version is the same for all of your Zyxel devices (ATP, USG FLEX, USG20(W)-VPN, etc.). You should presume you're at risk if it falls inside the vulnerable range, like V4.32 to V5.40 for ATP.
2. Disable remote web (WAN) management. Close the firewall's web interface right away if it's open to the internet. You can either let only certain IP addresses connect or only let VPN access.
3. Segmentation of the management network: Make sure that only trusted internal networks may access management, not networks from all over the place.
4. Watch the zysh-cgi flow. Check for odd downloads or POSTs to /cgi-bin/zysh-cgi, especially from accounts with less access or during the 2FA process.
5. Add the patch: Do this as soon as Zyxel makes the firmware update that fixes CVE-2025-9133. This isn't "optional."
For a longer time, stop.
• Check all admin roles, even if 2FA is turned on. Don't believe that logging in halfway is safe.
• Fix on the vendor side: Zyxel and other firms like it need to tokenize each sub-command, split it on semicolons or newlines, and verify each command independently instead of matching the complete string. The fault analysis explains it.
• Use role-based access and least privilege for management user accounts.
• Regularly check your firewall settings and backups, and replace your passwords and keys if a configuration has been made public.
• Make sure to log and report big config exports or downloads, even if they look real. You should check out volumes or times that aren't normal.
Things to consider for your company
If you work for a big organization that employs a lot of these kinds of devices, approach this like a network-wide issue and presume that your setup may have been observed unless you can show otherwise. Check any gadgets that someone else is in charge of or that are far away. There can be a "Zyxel router vulnerability" lying in the deployment that is least used.
What does this mean for network equipment and built-in systems?
This problem with network appliances and firmware offers us some greater lessons that go beyond just fixing it.
• 2FA is nice, but not enough: In this example, two-factor authentication was set up, but the bypass happened before it was done. Authentication is simply one component; permission, or what you can do, is just as crucial.
• It's important to check the input: The problem was that the device simply looked at the start of the command string ("prefix") and then sent the remainder of it without inspecting it. There is a little error in the code, but it might kill someone.
• People don't pay as much attention to embedded systems: Firewalls and routers don't often get the same number of upgrades and reviews as servers, but they are incredibly vital for getting to the internet. "Zyxel router vulnerability" means a device, not a general server. This means that organizations need to pay just as much attention to appliance firmware.
• Management interfaces are particularly important targets: Attackers will try to get into places like /cgi-bin/zysh-cgi, config export endpoints, and web admin portals that are on the internet. These are ways to get into networks that are not public.
• It's still important to patch things up and keep track of your inventory: You can't answer if you don't know what devices you have and what software they are running. This is fundamental cleanliness, but many firms don't do it.
What I learned and what I believe about it
When I originally heard about this "zyxel router vulnerability," I thought, "Oh great, another bug in the firewall," and then I forgot about it. But the more I read, the more I noticed how clever it is not just because of smart technical methods, but also because it alters the way people think in the actual world. Many network teams believe that setting up 2FA makes them safe. This mistake shows that a locked door isn't adequate if the hinge is broken.
I remember a coworker stating, "We protect our network, but we forget that we're protecting the people who protect it." In other words, our firewalls should keep us secure, but if they have hidden problems, we're fighting with one hand behind our back.
If your company uses Zyxel gear, don't wait for an exploit to occur. Do something now. Use this time to not only address one hole but"Zyxel also to check how you safeguard your network devices. The next "Zyxel router vulnerability" might not only disclose configs; it might also allow hackers to run commands, add malware, or get into systems you didn't expect.
Final thoughts
The phrase "Zyxel router vulnerability" might not make much sense, but the truth behind it CVE-2025-9133 is quite serious and needs to be acted on. If there is no authorization check and command chaining, attackers can get to the center of your network more quickly.
Next, you should locate devices that are easy to hack, limit access to them, keep a watch on traffic, apply firmware upgrades, and make appliance management a key priority for security.
If you accomplish that, you'll be ahead of the game. Instead of just reacting to the next story, you'll be safeguarding your network from one of the most insidious threats this year.
The Zyxel router flaw shows why regular security checks matter. Hoplon Infosec’s Penetration Testing helps find and fix hidden weaknesses before attackers do, keeping your network safe and resilient.
You can also read these important cyber security news articles on our website.
· Apple Update,
For more Please visit our Homepage and follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :