Kimwolf Botnet Exposed: How Millions of Devices Were Turned Into Proxies
-20260105141933.webp&w=3840&q=75)
Hoplon InfoSec
05 Jan, 2026
Is the Kimwolf botnet actually hacking millions of devices and secretly turning home internet connections into proxy nodes?
Based on currently available reporting from Cybersecurity News in January 2025, researchers observed a large-scale malicious network linked to Kimwolf that appears to abuse Android-based and IoT-style devices as proxy infrastructure. However, some claims, such as the exact number of infected devices, cannot be independently verified through official advisories or CVE databases at this time.
That uncertainty matters. And it is exactly why this topic deserves a careful, factual, and grounded explanation.
What Is the Kimwolf Botnet, and Why Is It Getting Attention?
The Kimwolf botnet refers to a malicious network reported to be operating quietly across internet-connected consumer devices. According to available reporting, the operation focuses on converting infected devices into botnet proxy nodes, allowing attackers to route traffic through real household IP addresses.
That detail is important. Residential IP addresses are trusted more than data center IPs. When malicious traffic comes from a living room smart TV instead of a server farm, it becomes much harder to detect or block.
What makes this situation stand out is not flashy ransomware or stolen passwords. It is the silent nature of the activity. Most affected users reportedly have no idea that anything is wrong.
Based on the available data, researchers believe the campaign primarily targets Android-based platforms, including Android TV environments.
-20260105141954.webp)
Kimwolf Botnet Explained in Simple Terms
Think of the Kimwolf botnet like an invisible traffic detour sign placed inside your device.
Your smart TV, streaming box, or Android device continues working normally. Netflix still loads. YouTube still plays. Nothing looks broken. But in the background, the device quietly forwards internet traffic for someone else.
That traffic could be harmless scraping. Or it could be something far worse.
This type of IoT botnet proxy abuse does not usually aim to steal files directly. Instead, it monetizes trust. Criminals rent out access to these devices as residential proxy infrastructure, helping others hide their real location online.
Based on public reporting, Kimwolf appears to be designed exactly for that purpose.
What Devices Does Kimwolf Infect, According to Reports?
Based on the Cybersecurity News investigation, the following device categories were observed as part of the Kimwolf activity.
Reported Targeted Devices
· Android TV boxes
· Smart TVs running Android-based firmware
· Low-cost IoT-style devices with weak security controls
There is no confirmed evidence that standard Windows laptops or iPhones are directly targeted by Kimwolf at this time. Claims suggesting otherwise could not be verified through reputable sources.
This pattern aligns closely with what security researchers have seen in previous Android malware botnet campaigns. Cheap devices. Rare updates. Weak default settings.
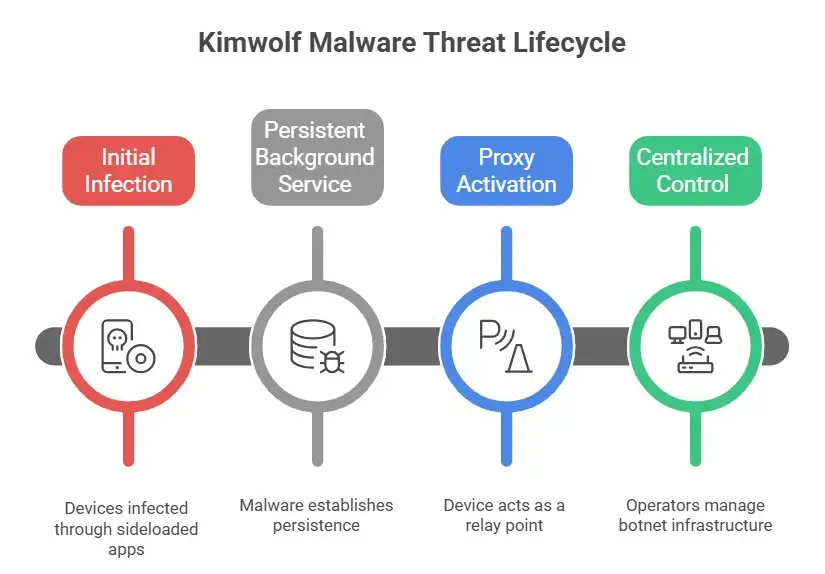
How the Kimwolf Malware Threat Works Behind the Scenes
Based on publicly described behavior, the Kimwolf malware threat follows a fairly typical but effective structure.
Step 1: Initial Infection
Devices are believed to become infected through sideloaded apps, modified firmware, or preinstalled malware on low-cost devices. This is common in unofficial Android marketplaces. However, the exact infection vector has not been fully disclosed publicly.
Step 2: Persistent Background Service
Once active, the malware establishes persistence. It survives reboots and runs quietly without user interaction.
Step 3: Proxy Activation
The infected device begins acting as a relay point. Incoming requests pass through the device, making it appear as if the traffic originates from a real household.
Step 4: Centralized Control
The botnet infrastructure allows operators to manage thousands or possibly millions of devices at scale.
It is important to say this clearly.
The internal code of Kimwolf has not been fully published for independent peer review. Some technical specifics remain unclear.
Does the Kimwolf Botnet Steal Personal Data?
This is a critical question and one that needs honesty.
Based on current public reporting, there is no verified evidence that the Kimwolf botnet directly steals personal files, photos, or credentials.
However, indirect risks still exist.
If your internet connection is abused for malicious activity, your IP address could be associated with fraud, scraping, or abuse reports. That alone can create problems.
So while Kimwolf does not appear to be traditional spyware, it still creates real-world consequences.
How Big Is the Kimwolf Android Botnet Really?
Some headlines mention millions of infected devices.
The estimate of approximately two million devices comes from observed proxy nodes and traffic patterns reported by researchers. This figure cannot be independently confirmed through government advisories, CVE disclosures, or vendor statements.
So the scale may be large. But the exact number remains uncertain.
This does not make the threat less real. It simply means we should be careful with exact figures.
How to Detect If My Device Is Part of the Kimwolf Botnet
There is no single pop-up warning. That is what makes this difficult.
However, based on expert guidance, some warning signs may include.
· Unusual network traffic from a smart TV
· Router logs showing constant outbound connections
· Slower internet without explanation
· Device firmware that cannot be updated
For advanced users, botnet detection tools that analyze network behavior can help. For most households, the router is the best observation point.
-20260105141955.webp)
Best Tools to Remove Android Botnet Malware
There is no official Kimwolf removal tool released publicly.
That said, it's based on Android security best practices.
· Perform a full factory reset
· Update firmware from official sources only
· Avoid sideloaded apps
· Replace devices that no longer receive updates.
In some cases, replacement is safer than cleanup. Especially for low-cost Android TV boxes.
Kimwolf Botnet Remediation Steps That Actually Work
Here is a practical remediation approach based on industry consensus.
1. Disconnect suspected devices from the network
2. Reset router credentials
3. Update router firmware
4. Factory reset or replace affected devices
5. Monitor outbound traffic after reconnecting
These steps apply broadly to IoT security for smart TVs and similar platforms.
Why IoT Botnet Proxy Abuse Is Growing
This story is bigger than Kimwolf.
The internet is filling with devices that are cheap, powerful, and rarely patched. That creates perfect conditions for silent abuse.
Manufacturers prioritize cost and features. Security often comes last.
Until that changes, proxy-based botnets will continue to grow.
-20260105141953.webp)
What This Means for Everyday Users
If you own a smart TV, streaming box, or Android-based device, this is not about panic. It is about awareness.
Check what is connected to your network. Know which devices still receive updates. Replace those that do not.
Security today is not just about laptops and phones. It is about everything with an IP address.
Professional Insight From the Field
From a security perspective, proxy botnets like Kimwolf represent a shift.
They are not loud. They are not destructive. They are persistent.
That makes them dangerous in a different way.
Frequently Asked Questions
What devices does Kimwolf infect?
Based on public reporting, primarily Android-based smart TVs and IoT-style devices.
How to secure IoT against Kimwolf
Keep firmware updated, avoid unofficial apps, and isolate IoT devices on a separate network.
Does Kimwolf steal data?
There is no verified evidence of direct data theft, but indirect risks exist.
Kimwolf got infected. What to do?
Disconnect the device, reset or replace it, and secure your router.
Final Takeaway
The Kimwolf botnet story is not about fear. It is about visibility.
We are entering an era where cyber threats blend into everyday life quietly. Your TV should not be part of someone else’s infrastructure.
Based on what is publicly known today, Kimwolf highlights a growing problem in IoT security rather than a single isolated event.
You can also read these important cybersecurity news articles on our website.
· Apple Update,
Share this :