CISA Warns About New WinRAR Zero Day RCE Vulnerability

Hoplon InfoSec
10 Dec, 2025
Could a simple RAR file, like a resume or job application, let hackers get into your Windows PC? That scary picture came true in 2025. In August 2025, security researchers found a big problem with WinRAR that let attackers run bad code just by having a user extract a specially made archive. Quickly, agencies and companies told users to update WinRAR before more attacks work.
You could be in danger if you use WinRAR on Windows and haven't updated to version 7.13. This article talks about how the exploit works, why it got so bad, and what you can do to protect yourself.
Knowing the Weaknesses in WinRAR
What are CVE-2025-8088 and CVE-2025-6218?
The main issue is a flaw in Windows builds of WinRAR that lets you go through paths and alternate data streams. CVE-2025-8088 and CVE-2025-6218 are the two identifiers that are keeping an eye on this problem.
With these bugs, a bad archive can make WinRAR use file paths that the attacker controls instead of the path that the user chose. That means that when the program unpacks a RAR archive, it might put the files in the system or startup folders instead of the clean folder that the user chose.
This means that when someone extracts the archive, harmful files like executable code, hidden DLLs, or launcher shortcuts can end up in places where they will run on their own. That means that code can be run from a distance, and the system can be hacked.
When and how the flaw was discovered
Researchers at a big cybersecurity company found the flaw for the first time on July 18, 2025. They saw strange file paths in a RAR archive, which turned out to have a dangerous DLL called msedge.dll inside.
On July 24, the developers of WinRAR were told about the find. The patched version 7.13 came out less than a week later, on July 30, 2025.
The earlier vulnerability known as CVE-2025-6218 was also reported, along with the main flaw. That earlier bug also had to do with directory traversal and added to the overall risk.
This quickly became a big problem because a lot of people and businesses depend on WinRAR on Windows.
How Attackers Use the WinRAR Exploit, Step by Step
This is how a typical attack using this WinRAR zero-day works:
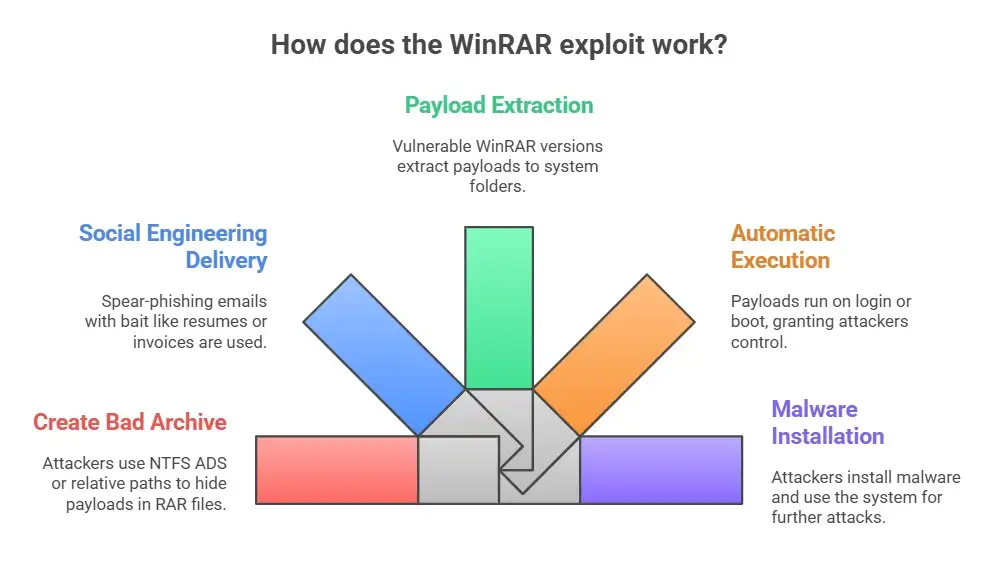
Step 1: Making a bad archive
At first glance, an attacker makes a RAR file that looks safe. It might be named something like a resume or application document. They use NTFS alternate data streams (ADSes) to hide payloads inside that archive, or they use relative paths (like "...") to get to places outside of the folder where they want to extract.
Step 2: Using social engineering to deliver
A spear-phishing email sends the bad archive. A job application, CV, invoice, or business document is often the bait that makes people lower their guard.
Step 3: Taking out and dropping the payload
If the person who gets the archive uses a vulnerable version of WinRAR (7.12 or earlier), the hidden files will be put in system folders like the Windows Startup folder or other places where programs automatically run. That goes against what the user wants, and security tools might not see the alternate data stream payload.
Step 4: Run automatically and stay in place
The payload runs automatically when the user logs in again or the system boots up, giving attackers the right to run any code they want. That lets them install backdoors, spyware, or other harmful tools without the user having to do anything else.
Step 5: Installing malware and making the situation worse
Once inside, attackers can run more commands, install remote-access tools that stay on the system, steal data, or use the hacked system for more attacks, like lateral movement.
This exploit method turns a useful tool that people all over the world use into a sneaky way to spread malware. That makes the weakness even more dangerous.
Why This Vulnerability Matters: It's a Real Risk That Affects the Whole World
This problem is not just a theoretical bug. It has been seen in attacks that have happened in the real world. Security reports say that two groups of threat actors connected to the exploit are RomCom and Paper Werewolf. Both are said to have used the flaw in targeted campaigns.
The campaigns used social engineering and phishing emails that looked like job applications or real business documents. That makes it more likely that people who don't know what they're doing will open the files, especially in places with a lot of email traffic.
The possible effects are huge because WinRAR is still widely used. Many businesses and personal computers around the world may still be using versions that are vulnerable versions, putting a lot of machines at risk of this zero-day.
The exploit also takes advantage of creative ways to misuse NTFS alternate data streams and path traversal. This makes it harder to find the bad files because they may stay hidden and not set off normal alarm heuristics.
Because it is so widely used, needs to be updated by hand, and is delivered in a phishing-style way, this vulnerability is a nightmare for businesses, especially in fields that deal with sensitive data or where employees often open attachments.
How a Simple Resume Could Crash a Computer
Think about an HR officer at a medium-sized business getting an email with the subject line "Candidate Application - Jane Smith." "JaneSmith_Resume.rar" is the name of the file that is attached. She double-clicks the archive and uses WinRAR to open it. She doesn't see that there is a hidden, malicious DLL and a shortcut file in this archive that will run when the computer starts up.
The bad files get into the Windows Startup folder without anyone noticing because WinRAR is out of date (for example, version 7.12). The next day, when the system starts up, the payload runs by itself. The attacker can now access the system from afar, install a backdoor, and start quietly stealing company data. It all started with a "normal resume" and a tool that people have trusted for years. That is what attackers connected to RomCom are said to have tried to do in 2025.
When vulnerabilities and social engineering come together, this story shows how everyday tools can become dangerous.

Why is this wweakness sorisky
It turns a regular archive program into a way to send malware without any obvious signs.
The exploit can ignore what the user wants: the attacker can change the extraction paths.
Hidden payloads in NTFS alternate data streams are hard to find.
What this event shows about the risks of software
Even tools that are simple and have been around for a long time need to be actively maintained and patched when needed.
The window of exposure is bigger because of manual update processes and the absence of auto-update.
Attackers are using social engineering and small technical flaws together more and more to get the most out of their attacks.
What defenders should do now
Update WinRAR to version 7.13 or later right away.
Teach users to be careful with RAR or ZIP attachments that they didn't expect, especially if they came from someone they don't know or trust.
Use antivirus or endpoint detection to keep an eye on strange file writes, changes to the startup folder, or hidden ADS files.
For businesses, block RAR attachments at mail gateways whenever you can, or at least make sure they are looked at more closely.
Questions and Answers
What is the zero-day flaw in WinRAR?
It is a flaw in WinRAR for Windows (versions up to 7.12) that lets people move through paths and streams of data. It lets hackers put harmful payloads inside a RAR archive and pull them out into system or startup folders, which lets them run code from a distance. CVE-2025-8088 and CVE-2025-6218 are the two tracked identifiers.
Has there been an official notice?
Yes. Security companies and news organisations said that hacking groups were actively taking advantage of the situation. On July 30, 2025, WinRAR 7.13 sent out a patch.
How do hackers use it to run code?
They send a bad RAR file, often through a phishing email. When you open it with a vulnerable version of WinRAR, it puts hidden executable or shortcut files into auto-run directories. These files run automatically the next time you log in.
How can I keep myself or my business safe?
You need to get WinRAR version 7.13 or higher. Do not open RAR files that come from people you don't know. Use antivirus or endpoint tools that look for strange file writes or changes to the startup folder. And teach your staff to be careful with unsolicited archives.
Final Thoughts
You can't ignore this if you use WinRAR, especially on Windows. CVE-2025-8088 and CVE-2025-6218 are two zero-day vulnerabilities in WinRAR that made it possible for a simple archive extractor to become a powerful tool for spreading malware. Attackers all over the world, connected to groups like RomCom and Paper Werewolf, used fake RAR files to attack businesses and people.
The best and easiest thing you can do is update WinRAR to version 7.13. But that's not the end of security. Be careful with any RAR or ZIP attachments that you didn't ask for. Use security tools that can find strange extraction behaviour, and teach users to be suspicious of archives that are not what they seem.
Do it now. Stay alert, patch, and protect.
You can also read these important cybersecurity news articles on our website.
· Apple Update,
For more, please visit our Homepage and follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well.
Share this :