Cloud Mobile Security in 2026: Risks, Solutions, and Best Practices

Hoplon InfoSec
10 Jan, 2026
It's no longer just a niche issue to worry about cloud mobile security. It is now a daily business risk. It's important to say this clearly in the first hundred words. Cloud mobile security keeps smartphones and tablets safe when they connect to cloud apps, cloud storage, and business systems. That sounds easy. In real life, it's messy, broken up, and often not understood.
Most cloud breaches a few years ago started on laptops or servers. Mobile devices are at the center of cloud access these days. Sales teams use phones to sign contracts. Developers can approve deployments from tablets. While traveling, executives look at sensitive dashboards. The cloud didn't get weaker. Access paths did.
I've seen companies spend a lot of money on cloud security tools, only to leave a hole at the mobile layer without even knowing it. Not because they were careless, but because mobile and cloud teams don't often work together on security. That gap is where attackers are now putting their energy.
This article talks about what cloud mobile security really means, where the real risks are, what most of the top articles miss, and how businesses can fix the problem without hurting productivity.

What is Cloud Mobile Security, Really?
Cloud mobile security is the set of technologies, policies, and services that keep mobile devices safe when they connect to cloud environments. It includes protecting data, checking the posture of devices, controlling who has access to them, and keeping an eye on them all the time.
Most articles say that it means "securing mobile devices in the cloud." That definition doesn't cover everything. The main goal is to make sure that mobile devices can access the cloud, no matter where they are or who owns them.
Cloud mobile security solutions protect users from cloud services. They check who you are, how healthy your device is, how you use it, and what data you can see or share. Some controls are built into the device. Some people only live in the cloud.
When it comes to enterprise cloud mobile security, malware isn't the only thing that matters. It's about stolen tokens, APIs that aren't safe, shadow IT, and weak identity enforcement. You don't often see those risks in marketing materials, but they do happen in real life.
Why mobile devices are the weakest link in cloud security
I once looked into a case where a company's cloud account was hacked without using malware, phishing, or brute force. The hacker used a cloud access token that they stole from a mobile app debug log. The security team had made everything else stronger.
There are three reasons why mobile devices are good targets.
To begin with, they are personal. People use their phones for work, social media, banking, and fun. That makes the risks overlap.
Second, mobile sessions last longer. People don't often log out of cloud apps on their phones. Tokens stay good for days or weeks.
Third, you can't see very well. Security tools that were made for desktops and networks. People often don't notice mobile behavior.
There are real risks to mobile security in the cloud. They are real-world situations that come about because of how people use devices.
Cloud mobile security risks and the current state of threats
Mobile Cloud Security Threats You Should Really Be Concerned About. Not all risks are equally important. According to public incident reports and business assessments, the most common mobile cloud security threats are:
• Token hijacking through compromised mobile apps
• OAuth abuse through third-party integrations
• Insecure mobile APIs that expose cloud data
• Shadow IT mobile apps that connect to corporate cloud accounts
• Lost or stolen devices with active cloud sessions
• Weak biometric or PIN enforcement on personal devices.
There is still malware, but it is not the main cause anymore. Attackers like paths that are quieter and harder to find.
Cloud security for mobile devices should assume that hackers already have some access. The goal is to limit the blast radius and find strange behavior early.
Bring Your Own Device (BYOD) programs made people more productive, ve but also made them feel like they could trust each other. Companies trust devices that they don't own. That trust is broken when personal apps leak passwords or store tokens in an unsafe way.
Most of the time, mobile data protection in the cloud fails when you switch apps. A user moves data from a secure cloud app to a note-taking app on their phone. That action gets around a lot of controls unless the cloud mobile security architecture is set up to stop it.

A Simple Explanation of Cloud Mobile Security Architecture
A good cloud mobile security architecture doesn't depend on just one tool. It works in layers.
Main Layers of Architecture
1. Control of Identity and Access
Cloud IAM for mobile devices checks the user's identity and what they can access. This includes session risk scoring, conditional access, and MFA.
2. Trust and posture of the device
The system checks to see if a device is jailbroken, out of date, or missing security controls. This doesn't always mean you have to fully manage the device.
3. Safe access to the mobile cloud
Traffic goes through secure gateways or brokers that check requests without slowing down the user.
4. Controls for Data Protection
This includes policies for cloud-based DLP, encryption, copy and paste restrictions, and watermarking.
5. Constantly Watching
Behavior is watched over several sessions. Alerts or access restrictions are set off by sudden changes.
The best cloud security framework for mobile devices strikes a balance between control and ease of use. Heavy-handed designs don't work because users find ways around them.
Why Traditional MDM Isn't Working in Cloud-First Businesses
There is a big gap in the content of the top-ranking articles.
Mobile Device Management was made for people who own devices. Cloud access doesn't care who owns the device. It cares about who is using it and how.
When MDM is seen as a signal instead of a gatekeeper, MDM and cloud security integration work. Making employees fully enroll their devices to get basic cloud access drives them to use shadow IT.
Instead of locking down the whole device, modern cloud mobile security solutions are more and more using app-level controls, identity context, and cloud-based enforcement.
I have seen companies lower their risk by getting rid of harsh MDM rules and putting in place smarter cloud access rules instead. That doesn't make sense, but it works.

Cloud-based mobile security solutions for businesses
There are many types of cloud mobile security solutions:
• Cloud-based mobile security services that work with IAM
• Mobile threat defense platforms that work with cloud policies
• Secure access service edge models that work with mobile devices
• Managed cloud mobile security services for small teams
The mobile security cloud platform is the control plane. It makes sure that rules are followed on all devices, apps, and locations.
Enterprise cloud mobile security needs to work for contractors, partners, and people who work from home. That means rules that can be changed, not rules that work for everyone.
When does managed cloud mobile security make sense?
A lot of companies don't have people who know how to secure mobile devices. Managed cloud mobile security services fill that gap. They keep an eye on threats, make sure policies are up to date, and deal with incidents.
This model works well in industries that are regulated and need to make sure that cloud mobile security compliance is always up to date. It's not about giving up responsibility. It has to do with adding specialized oversight.
Cloud Mobile Security: Zero Trust and Identity
It sounds easy to hazero-trustust mobile cloud security. Check everything. Don't believe anything. It doesn't work when used strictly in real life.
People who use mobile devices move. Networks are always changing. The context changes all the time.
Dynamic trust levels are a key part of successful zero-trust mobile security. A user who checks email from a known device can do so without any problems. If the same user tries to export data from a new location, they will need to go through extra verification.
Cloud identity protection is the most important thing here. Without strong identity signals, zero trust means zero productivity.
Regulatory protection, privacy, and compliance
Mobile Security in the Cloud: Following the Rules in Real Life
GDPR mobile cloud security and HIPAA mobile cloud protection are two examples of compliance requirements that go beyond encryption.
They want proof that access control, audit trails, and breach containment are all in place.
Enterprise mobile cloud compliance often doesn't work during mobile incident response. Logs are broken up. Forensics isn't finished. The rules are not clear.
A strong architecture that is ready for compliance keeps logs and access decisions in one place. That makes audits easier and lowers the risk during investigations.
Cloud mobile security vs. security on the device
The phone is safe because of on-device security. Cloud mobile security keeps safe what the phone can access
You can't choose between cloud mobile security and on-device security. It's a partnership. Device security lowers the risk of exposure. When devices fail, cloud controls help limit the damage.
Companies that only use device controls will eventually run into problems. People who only use cloud controls run the risk of data leaks when they do things on their own.
Factors that affect price, cost, and choice
Getting to know the Cloud Mobile Security price
Prices for cloud mobile security are very different. Costs depend on the number of users, the type of enforcement, and whether the service is managed or self-service.
Requirements for compliance
The license fee is not the real cost of cloud mobile security. When controls aren't put in place correctly, it costs a lot to fix the problems.
Not always does the best cloud mobile security provider have the most features. It is the one that works with the way things are already done and the level of risk you are willing to take.
Trends in Cloud Mobile Risk
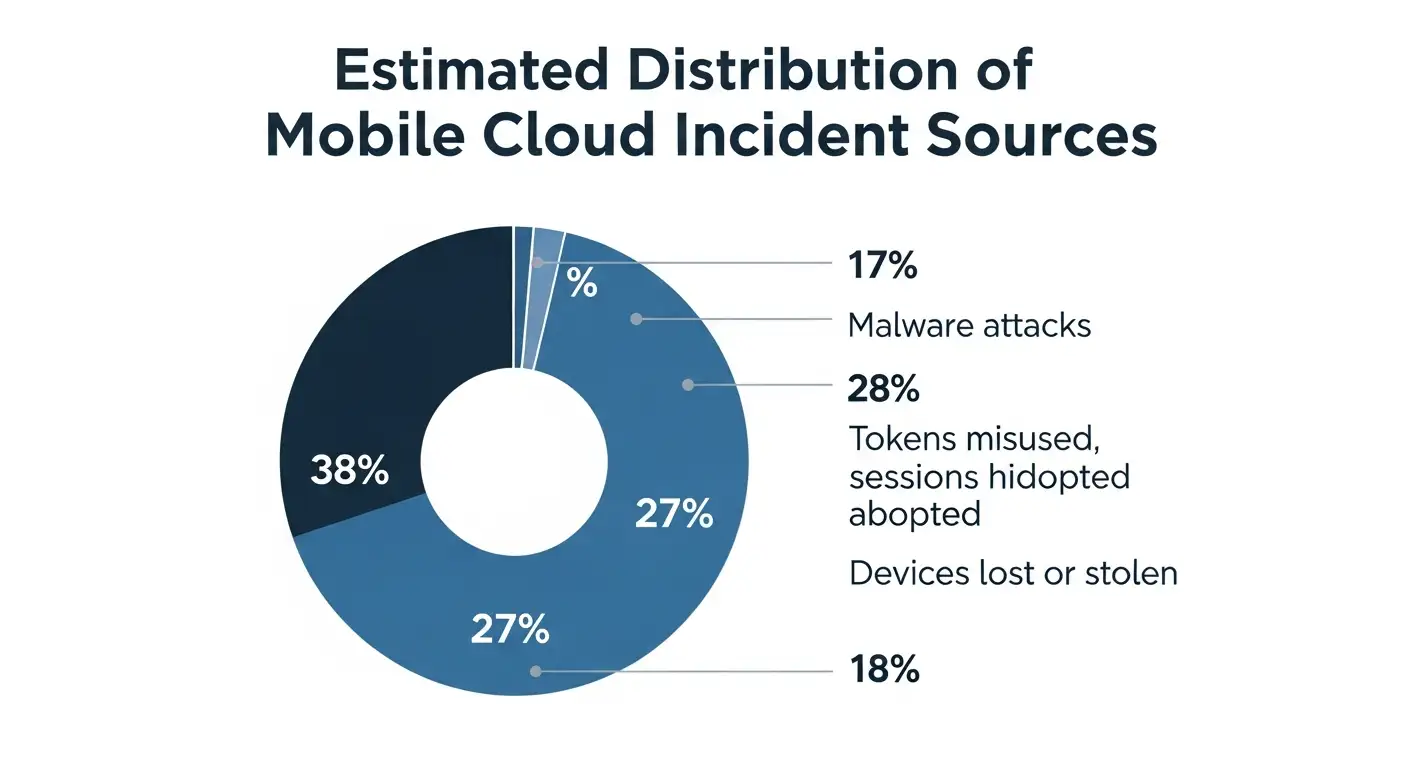
Different industries and sources of information report different percentages. Public datasets have different exact numbers.
What is a risk heatmap?
When mobile access and privileged cloud roles meet, there is a high risk. There is a medium risk with standard SaaS access. Read-only use cases seem to have less risk.
How to Protect Mobile Devices That Use Cloud Services Step by Step
1. Map out the ways that mobile devices can access cloud apps.
2. Sort data by how sensitive it is based on how it will be used on a mobile device.
3. Make cloud IAM for mobile devices stronger.
4. Add checks for device posture without full enrollment.
5. Use rules for protecting data at the app level.
6. Keep an eye on behavior all the time.
7. Use mobile scenarios to test how well you respond to incidents.
Every step builds on the one before it. Not following the steps makes you feel like you can do anything.
People Also Ask: FAQs
What does "cloud mobile security" mean?
Cloud mobile security keeps mobile access to cloud services safe by using identity, device context, and cloud-based controls instead of just device management.
What makes mobile security so important for cloud environments?
This is because mobile devices are now the main way to get to cloud apps, and attackers take advantage of the fact that they are less visible and have longer session times.
How do you protect mobile access to cloud apps?
By using cloud IAM, device posture signals, app-level protection, and constant monitoring together.
Is mobile security in the cloud safe?
Yes, if they are made the right way. Poor implementations can make things riskier by making users act in ways that are not safe.
What This Article Adds That Top Google Results Don't
Most of the top results are about tools, not behavior. They talk about features but not how people really use mobile devices.
They downplay the risk of token misuse, exaggerate the risk of malware, and rarely talk about why MDM doesn't work in cloud-first environments.
This article fills in those gaps by talking about access paths, identity theft, and real-world business experience.
Final Thoughts
Locking down phones is not what cloud mobile security is all about. It's about respecting how people work while lowering risk without making a big deal out of it.
By default, mobile devices are not the weakest link. When cloud security strategies don't pay attention to them, they get weak.
You can also read these important cybersecurity news articles on our website.
· Apple Update,
For more Please visit our Homepage and follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :