React2Shell vulnerability explained with risks fixes and detection

Hoplon InfoSec
09 Dec, 2025
You may be wondering what React2Shell CVE 2025 55182 means for your React or Next.js project and if you can find it before hackers do. On December 3, 2025, security researchers found a serious remote code execution flaw in the core of React Server Components. Developers who rely on React or Next.js for production workloads had questions right away after the discovery.
In this guide, I explain the vulnerability in simple terms, talk about how it affects real apps, and show you how to use Burp Suite and some simple methods to find out if you might be exposed. The point is to help you understand what's going on and what you can do to keep your project safe.
What is React2Shell CVE 2025 55182, and why should developers pay attention to it?
What the React2Shell vulnerability is all about
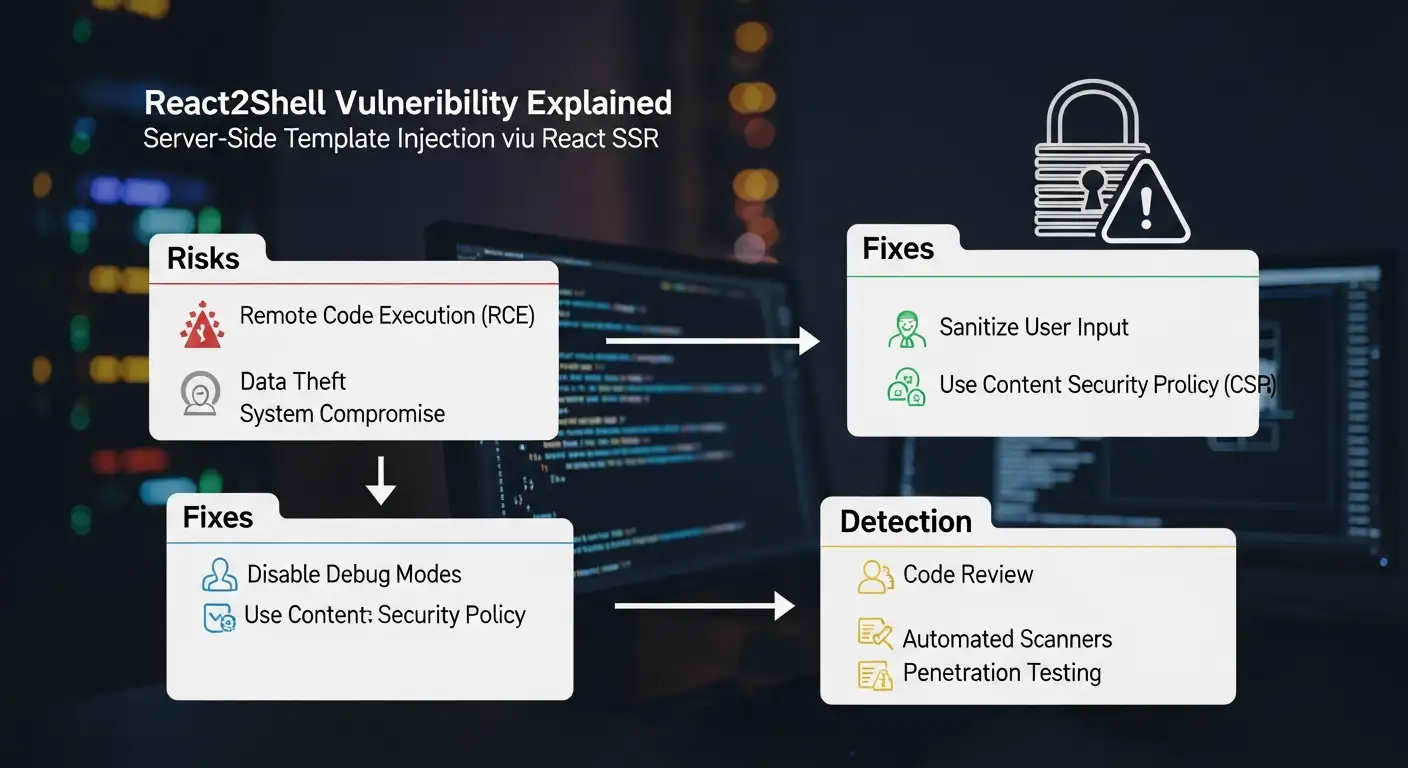
There is a serious remote code execution problem with React2Shell CVE 2025 55182 that is part of the Flight protocol used by React Server Components. The server reads and processes a serialized data stream that comes from the client. Because some versions of the protocol have unsafe deserialization logic, a crafted payload can trick the server into running any code it wants. This is the kind of problem that lets an attacker send one request and run any code on a remote machine without having to log in.
What makes it even more worrying is that the vulnerability doesn't need a component to be set up wrong or a mistake by the developer. It is buried deep inside the protocol layer. That means that even a new Next.js project made with the default template could be at risk if it uses the affected versions of the RSC packages.
Versions that are affected and the real scope
React Server DOM Webpack, React Server DOM Parcel, and React Server DOM Turbopack are the packages that are involved. Versions 19.0.0 to 19.2.0 were affected. Any framework that uses these packages, especially Next.js, could be a target.
Versions 15, 16, and a few canary builds of version 14 of Next.js were confirmed to be affected. A lot of developers use these versions in projects that are currently in production. This gives React2Shell a very wide reach, which is why security teams acted quickly when the reports came out.
How unsafe deserialization in the Flight protocol causes server-side Running React code
What goes wrong behind the scenes?
The Flight protocol takes care of a steady stream of server-side rendering data. React Server Components or the Next.js App Router turn this data back into JavaScript structures when they get it. The issue arises because the deserialization process relies on certain segments of the incoming data stream without rigorous validation.
A hacker can put a bad value into the serialized data. When the server sees this value, it starts a chain of internal logic that lets code run on a remote machine. There is no bug in the code that the user wrote. There is a problem with the system that turns serialized RSC data back into usable objects.
Why some experts think it's the most serious JavaScript flaw of 2025
A lot of the modern web runs on React and Next.js. A lot of businesses run them in the cloud on a large scale. Attackers don't have to get around login systems or take advantage of business logic errors because React2Shell can be triggered without authentication.
Some cloud security teams said that almost four out of ten of the applications they scanned used RSC packages that were known to be vulnerable. When the problem was first reported, people thought the attack surface would be much smaller than it is now.

Can Burp Suite find React2Shell?
A useful way to do things with easy steps
Security teams often wonder if tools like Burp Suite or custom DAST scanners can find a site that is open to CVE 2025 55182. Yes, the short answer is yes. Even though the vulnerability is in the serialization layer, there are a few signs that can help you find it.
Things to look for while scanning
Send controlled requests to endpoints that use React Server Components with your scanner. This could include routes that start server actions or app router handlers. When a vulnerable server gets malformed RSC payloads, it may show server-side errors or strange messages.
Numerous researchers observed that a susceptible system frequently generates a five-hundred error or an unforeseen deserialization error upon the activation of the insecure deserialization path. If you set up the right checks, Burp Suite can catch these answers.
Using Burp Suite with checks that are either custom-made or improved by ActiveScan
You can make your own scan checks and request templates with Burp Suite. This lets you copy parts of an RSC payload without actually taking advantage of the system. The scanner can find unusual server responses by sending a modified serialized structure to likely RSC endpoints.
This method works best in a staging environment, not in production. If the server tries to read the payload while testing in production, it might not work as expected. You can safely watch the response and check to see if the application is vulnerable in a controlled sandbox environment.
What you need to do now
Actions that are easy and quick
• First, look at the project's dependencies. Find any version of the React server DOM package that is in the range of the affected ones.
• Check the version of Next.js if your app uses it. Install the security updates that came out for versions 15 and 16.
• If you use Vercel, Cloud Armor, or a WAF provider, check out any temporary rules they made for React2Shell payloads.
• Look through server logs for strange POST requests or RSC-related error messages that have been happening recently. • Fix the problem and redeploy as soon as you can. Temporary WAF filters can't promise safety.
Why CVE 2025 55182 needs detection tools
Many modern applications have a lot of hidden layers of dependencies. React2Shell showed how simple it is for a security hole to be hidden in a package that many people trust, even when code reviews are done.
Burp Suite and other tools help teams confirm real exposure instead of just guessing based on dependency lists. You can see which routes are dangerous and which parts of your application need immediate attention by watching how a real server behaves during a controlled scan.
Since proof-of-concept code was posted online soon after the disclosure, detection tools give you a clear advantage by helping you find the most vulnerable endpoints before attackers try the same thing.
In real life
Think about a small SaaS startup that has a Next.js 16 app running on Vercel. The team thinks everything is safe because they used standard tools to build the project. After the React2Shell leak, a developer checks the project's dependencies and finds react-server-dom-turbopack version 19.2.0.
When they run a quick Burp Suite scan in their staging environment, they get a five hundred error with strange serialization traces. This is a sign that unsafe deserialization might be going on. The team quickly updates to the patched version of Next.js and redeploys.
The strange behavior of the server doesn't happen after a second scan. This makes the team sure that the patch fixed the security hole. They later add an automated scan step to their deployment pipeline so that problems like this don't go unnoticed in the future.
Important things to know about using Burp Suite to find React2Shell
Pros:
• You can make your own checks that look like RSC payloads.
• Dynamic analysis shows how the server really works.
• When you put dependency audits and runtime testing together, you get a full picture.
Limitations:
• Generic scanners don't automatically understand the flight protocol.
• Active scanning against production is dangerous.
• WAF filters might catch known payloads, but attackers can change their patterns.
Questions that are often asked
What is React2Shell, and which versions are affected?
React2Shell is a serious security flaw in the React Server Components Flight protocol that lets hackers run code on your computer from a distance. It affects a lot of different versions of React Server DOM packages and a few big releases of Next.js.
How can I find React2Shell in my Next.js app?
Check your dependencies first. After that, use dynamic scanning tools like Burp Suite to send controlled requests to RSC endpoints that you think are suspicious. Keep an eye out for server errors that have to do with serialization.
Has anyone used React2Shell in real life?
Yes. Researchers saw attempts to scan RSC endpoints shortly after the information was made public. You can also get proof-of-concept code.
How can I test safely without hurting production?
Always use a clone of your environment for staging. First, run checks on dependencies. Then, only run your Burp Suite scans in a sandbox.
Final Thoughts
React2Shell CVE 2025 55182 is one of the worst security holes in the JavaScript ecosystem that we've seen in a long time. It changes the core function of React Server Components and makes many React and Next.js apps vulnerable to remote code execution.
The only way to be sure you're safe is to update to the patched versions. Burp Suite and other scanning tools can show you which parts of your app are open to attack, but that's only the first step. You should patch your infrastructure right away and then carefully check it.
You can also read these important cybersecurity news articles on our website.
· Apple Update,
For more, please visit our Homepage and follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well.
Share this :