Salesforce Flags Unauthorized Data Access: Ultimate Alert

Hoplon InfoSec
21 Nov, 2025
Imagine waking up one morning, logging into Salesforce, and finding out that someone else has been quietly reading your customer data with an app you already trusted. Salesforce just brought up the worst-case scenario: someone getting access to data without permission through an OAuth integration linked to Gainsight.
This isn't just another hole in security. It is a very serious warning about how dangerous SaaS integrations can be. Gainsight and other SaaS platforms are great, but they can also let data leak if something goes wrong.
What happened? What took place
Salesforce recently sent out a security warning saying it had found "unusual activity" involving Gainsight apps that were connected to Salesforce.
• Their investigation shows that those OAuth-linked apps could have "allowed unauthorized access to certain customers' Salesforce data." Salesforce made it clear that this problem doesn't seem to be caused by a flaw in its own CRM core. Instead, it seems to be caused by the "external connection" that Gainsight makes.
• Salesforce took away all active and refresh tokens linked to the Gainsight apps in question and put them on hold in its AppExchange.
• On the other hand, Gainsight said it is "working closely" with Salesforce on the investigation.

Why It Matters: The Big Picture
This isn't just a one-time breach; it shows a bigger problem with OAuth integrations in all SaaS:
1. OAuth as a new way to hack
Instead of trying to get into core systems, attackers are going after the connections between SaaS tools more and more.
2. Stealing tokens is a very bad crime.
If someone steals a long-lived OAuth or refresh token, they can act like a real app and get to data without raising any red flags.
3. Risk in the supply chain
People have used third-party integrations to get into things before. For instance, hackers used OAuth tokens from Salesloft's Drift to get into Salesforce.
4. Believe, but check.
Organizations often trust their third-party apps without checking them all the time. This event shows that integrations need to be watched just as closely as internal systems.
Take it one step at a time: What Most Likely Happened.
This is how the unauthorized access probably happened, according to reports and expert analysis:
1. Token Breach: People who may be part of the ShinyHunters group (also known as UNC6240) got a Gainsight OAuth token. Obsidian Security says this happened because tokens and "secrets" were stolen from a previous breach of Salesloft/Drift.
2. Token Abuse: The attackers are said to have used that token to give themselves permanent access to many Salesforce instances that were connected through Gainsight.
They probably used that access to run queries or copy data, which could have included private information like business contacts, license information, support case details, and more.
3. Anomaly Detection: Salesforce found "unusual activity," which could mean strange API usage, bulk reads, or query patterns, and started an investigation.
4. Containment: They removed all the OAuth tokens that were relevant and temporarily took down the Gainsight apps that were involved from AppExchange as a safety measure.
o People who might have been affected were told directly.
How This Could Happen in Real Life
"Acme SaaS," a medium-sized business, uses Salesforce to keep track of its customers and Gainsight to help them do well. OAuth lets Gainsight read and write data like customer contacts, support tickets, usage metrics, and renewal status.
A hacker could get the OAuth token for Gainsight by phishing, stealing a secret, or another way. Then they could issue a refresh token and have access for a long time. With that, they could get:
• The names and business emails of customers
• A history of support cases
• Metadata about internal licenses or contracts
• Sensitive usage metrics
After that, they could steal information, sell it, or even use it for more complex attacks like blackmail or social engineering.
That's what security experts think could have happened in the Gainsight-Salesforce case.

Risks and Effects
Here are some of the biggest risks that come with the Salesforce unauthorized data access incident and why businesses should pay attention to it:
• Loss and exposure of data: Sensitive customer information could be made public and used in a bad way.
• Damage to Reputation: Customers and partners may not trust you as much if they find out that your company was involved in a breach.
• Regulatory Risk: If the leaked data is private, you could have legal or compliance problems (like GDPR or CCPA).
• Persistent Threat: If someone gets hold of your OAuth tokens, they can use them for a long time because they can be refreshed.
• Weakness in the supply chain: This shows that attackers don't always have to break into the main infrastructure; breaking into a third-party app can be just as bad.
• Financial Impact: It costs money and takes time to fix things like taking away tokens, auditing, and doing a forensic investigation.
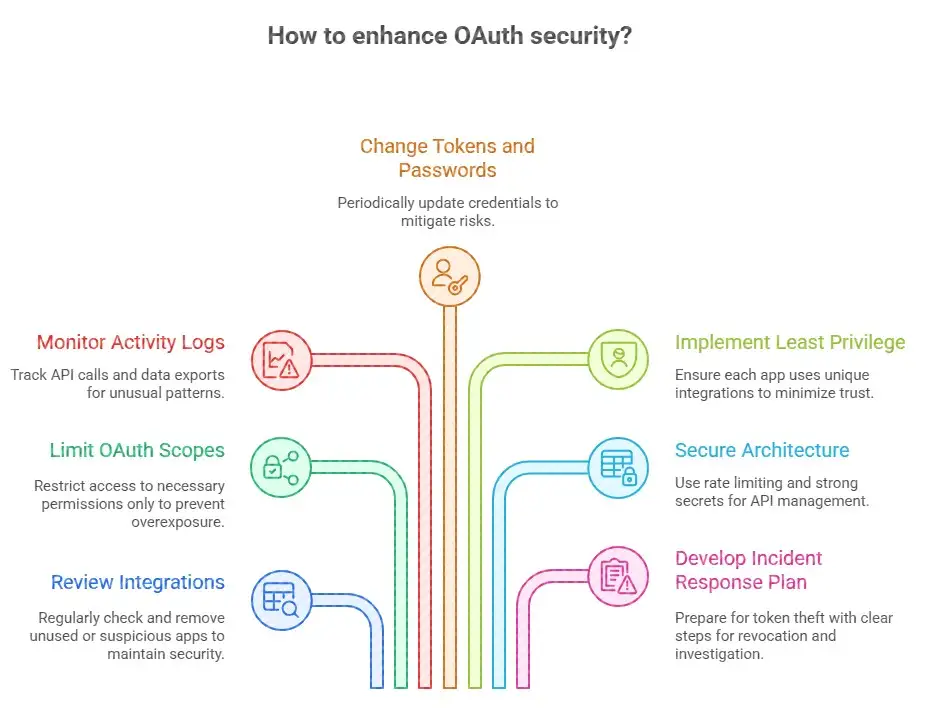
How to Keep Your OAuth-Linked Accounts Safe from Breaches
Here are some things you can do after this event, based on what security experts and the best practices in the industry say:
1. Look over your integrations.
Make a complete list of all the third-party apps that are connected to your Salesforce account through OAuth.
Check apps often and take away tokens from those that aren't being used or look suspicious.
2. Limit OAuth Scopes: Only give full access if you really need to.
Don't use wide scopes like bulk read/write or admin-level unless you have to.
3. Watch the activity logs.
Set up log monitoring to look for unusual API calls, large data exports, or unusual query patterns.
Use SIEM or alerting tools to mark any strange behavior that is linked to traffic from apps that aren't yours.
4. Change Your Tokens and Passwords
Every so often, change your OAuth tokens, secrets, and login information.
If you notice any strange behavior, take the tokens away right away. That's what Salesforce did with Gainsight.
5. Least Privilege and Zero-Trust: Don't trust any integrations at all.
Don't let more than one app use the same integration users.
6. Security in Architecture First
Use safe ways to manage APIs, such as rate limiting, token expiration, and named credentials.
Make sure that OAuth flows are set up in a safe way. Use PKCE or strong client secrets whenever you can.
7. Making plans for how to deal with problems
Make a plan just for when third-party integration goes wrong. What will you do if someone steals a token?
Include revoking tokens, letting customers know, doing a forensic investigation, and doing an audit as part of that plan.
• Nudge Security, a security company, has looked into the Gainsight-linked token abuse and made suggestions.
• Obsidian Security gave IOCs (Indicators of Compromise) and a full breakdown of the threat.• Threat actors may be linked to ShinyHunters (UNC6240), which has been linked to SaaS attacks through OAuth in the past. The Low Code Security Alliance says that OAuth integrations should be checked on all the time and that OAuth scope should be used as little as possible.
The End: What You Should Remember
The Salesforce flag for unauthorized data access via Gainsight-linked OAuth activity incident is a powerful reminder: third-party integrations, while useful, can become your weakest link. Even if you use a trusted tool like Gainsight, stolen tokens or scopes that aren't set up right can still put your data at risk.
Salesforce users and admins need to check their OAuth-connected apps, remove any permissions that aren't needed, and make sure security is better. Don't just think of integrations as tools that help you get more done; think of them as a place where things could go wrong. People who attack are already doing this.
It's better to lock things up now than to find out the hard way later.
FAQs
1. How did Gainsight tell Salesforce that someone had used it without permission?
Salesforce's security advisory said there was "unusual activity." This could mean that a lot of people were using the API, making strange queries, or accessing data in ways that weren't expected through the OAuth-linked Gainsight apps. That made them look into it, take away tokens, and take those apps off the AppExchange for a short time.
2. Does this mean that the Salesforce platform itself wasn't safe?
No. Salesforce says there is no proof that the main Salesforce platform was hacked or had any problems. It seems that the problem is with the connection that Gainsight makes from the outside.
3. Who might have done this?
Security experts believe that the ShinyHunters threat actor group, which goes by the name UNC6240, could be involved. They have been linked to other campaigns that use OAuth tokens in the same way.
4. What can businesses do now to stay safe?
• Look over all the third-party apps that are linked to your Salesforce account through OAuth.
• Get rid of tokens from apps that you don't use or that look suspicious.
• Give OAuth scopes only what they need.
• Look at the logs for strange activity and change your passwords often.
• Don't trust anyone, and only give integrations the access they need.
You can also read these important cybersecurity news articles on our website.
· Apple Update,
Share this :