Weekly Cybersecurity Recap: Oct 3-9, 2025 Highlights
-20251010125455.webp&w=3840&q=75)
Hoplon InfoSec
16 Feb, 2026
Every weekly recap tells a different story. Some weeks in cybersecurity seem calm, normal, and predictable. But then there are weeks like this one, which are full of wake-up calls, patches, zero-days, and shocking data breaches. The internet seemed a little more fragile than we like to admit because of Oracle's critical flaw, a huge Discord breach, a WordPress flaw, and a Redis RCE exploit.
This weekly summary goes over what happened, why it matters, and how all kinds of businesses, from small blogs to big companies, can learn from it.
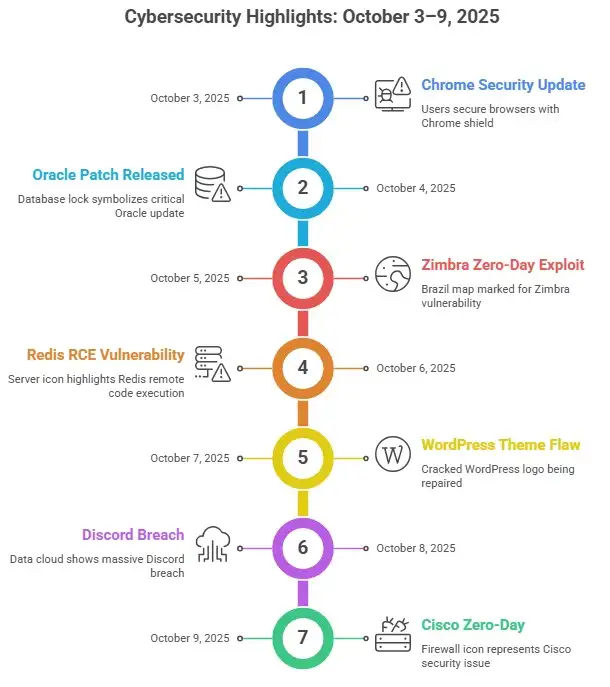
Patch for Oracle CVE-2025-61882: The Flaw That Could Ruin the Suite
The most important update of the week is Oracle's emergency patch for CVE-2025-61882. It went after the E-Business Suite (EBS), which is used by thousands of companies around the world to run their HR and financial systems. The flaw let attackers run remote code without having to log in, which meant they could take over the whole system.
The main point of this weekly recap is clear: even enterprise-grade systems can break down when one small function is missed and allows remote execution. Oracle quickly released a patch for the vulnerability, but timing was everything. A lot of businesses didn't patch in time, and that little delay could have led to a big breach.
Think about an accounting department that uses Oracle EBS to pay its employees. If attackers got in, they wouldn't just steal data; they could also change payment routes, invoices, or even employee records. It shows why cybersecurity trends now stress constant patching over quarterly updates.
This event reminded everyone who read this weekly recap that "patch fatigue" is a real thing, but it's much better than "patch regret."
Read more
The Discord Data Breach: 1.5 TB of User Data Lost in a Day
When it came out that Discord had a data breach that exposed 1.5 terabytes of data, including photos, IDs, and private messages, it scared more than just gamers. It made every business that uses third-party platforms to talk feel uneasy.
This story in our weekly recap shows that even platforms that people trust can become weak links. Hackers didn't need any fancy tools; they just found an endpoint that wasn't being used and stole everything. This was one of the biggest data breach analysis cases of 2025.
It's scary to think about how easily a hacked account could show private messages, pictures, and even sensitive login information. It's even more worrying how long it can take for these sites to let people know. A lot of people only find out when leaked databases start going around on the dark web.
This breach shows us that no system is too big to break. When things go wrong, social media and communication platforms need layered encryption, regular audits, and, most importantly, openness. This weekly summary is a good reminder.
Read more
The WordPress Service Finder Vulnerability: A Warning for Site Owners
Along with the Discord chaos, there was another big threat: the WordPress Service Finder Theme vulnerability. At first, it sounded like just another notice about a patch. But it quickly became one of the most talked-about things on Hoplon InfoSec that week.
WordPress runs almost half of the web, and when a commercial theme is found to be unsafe, thousands of small sites are immediately at risk. The flaw let attackers get admin-level access through requests that weren't verified. This was a dream come true for anyone who wanted to deface or take over a website.
It's hard to ignore the human side of this story in this week's recap. Think of a business in your area that uses the Service Finder theme to make appointments. If you don't notice an update, the whole website could be held hostage. All of a sudden, the wrong people have access to customer information, booking schedules, and payment information.
That's why a simple patch for a security hole isn't just a technical fix; it's also good digital hygiene. It's like brushing your teeth before you get a cavity. This story shows that even the smallest update to a plug-in or theme can make a big difference in terms of safety.
Read more
Cisco ASA FTD Zero-Day: Proof of Concept, Proof of Danger
Hoplon InfoSec also wrote an interesting report about the Cisco ASA FTD zero-day vulnerability. A proof of concept (PoC) was made public, showing exactly how the flaw could be used. It's like leaving the vault door open while thieves are already in town when a PoC goes live before organizations take steps to fix it.
From a technical point of view, the flaw let attackers from far away crash or take over Cisco's firewall systems, which are supposed to keep networks safe. The cybersecurity community didn't miss that irony, and it became one of the most important stories in this week's recap.
To put it another way, the guard was sleeping and the gate was wide open. This is another reminder that "secure today" doesn't mean "secure tomorrow."
Companies that used Cisco ASA had to rush to put in place temporary fixes while they waited for the official patch for the security hole. Once again, security teams all over the world were reminded that even the most important infrastructure can fall apart if a bug is missed.
Read more
Redis RCE Exploit: How the Cache Can Be Used as a Trap
Redis is more than just a cache, so don't think that. The Redis RCE vulnerability that came out this week changed that idea. Attackers figured out how to run any code they wanted on servers running Redis. In other words, they had full control.
This weekly review showed that the problem wasn't with Redis itself, but with how it was set up. A lot of administrators leave default ports open or don't bother with authentication at all because they trust their internal firewalls. But once an attacker gets past that internal layer, it's all over.
Think about an online store that uses Redis to keep track of its inventory and shopping carts. If someone takes over the Redis instance, they could add fake products, change prices, or steal user sessions. It's not just a guess; similar attacks have already been reported in past data breach analysis reports.
This is why defenses don't change as quickly as exploit techniques do. Just one weak port and one lost password are all it takes. And that's exactly what this weekly recap shows: mistakes in configuration can be just as bad as bugs in software.
Read more
The Use-After-Free Flaw in Google Chrome That You Shouldn't Ignore
The Google Chrome Update 2025 was one of the week's biggest stories. It fixed a serious memory problem that sounds small but can lead to big problems. When a program tries to use memory that has already been freed, it can cause use-after-free vulnerabilities. It's like going into a house that has already been torn down.
We should talk about that flaw in this weekly recap because browsers are how we get to everything every day. One click and one page load, and if your Chrome isn't up to date, malware can run before you even know it.
Picture yourself looking at a news site. This flaw could be triggered by just one bad ad, which could install spyware and record every keystroke. These aren't just "hacker movie" scenarios; they're real cases that have been seen in recent cybersecurity trends.
What did you learn? Update early and often. Your browser is the first line of defense and the way you get to the web. If you don't pay attention to it, it's like locking your front door but leaving your windows wide open.
Read more
Brazilian Military Hit by Zimbra Zero-Day
One of the more political stories in this week's recap came from South America. It was about how the Brazilian military was targeted with a Zimbra zero-day hidden in bad calendar files. The attack was quiet, accurate, and meant to get inside communications.
The fact that it is so advanced is what makes this one stand out. To take advantage of the Zimbra flaw, you had to know how military email worked and when to do it. It's a real-world example of how the threat landscape changes over time, from opportunistic to strategic.
This also shows why zero-days are important to everyone, not just the government. When an exploit like this gets out, other people start to use it for schools, businesses, and even nonprofits.
In a way, every story in this weekly recap is related to this one. Each zero-day and breach shows us how fragile digital security really is.
Read more
What This Week Teaches Us About the Big Picture
So, what did this weekly summary show about the state of cybersecurity right now?
Exploits are being turned into weapons within days of being found, and zero-days are getting faster.
The speed of vulnerability patches is very important. The faster a company patches, the less risk it has.
Attackers don't care if you run a corporate suite or a WordPress blog; they'll find a way in. Themes, browsers, and servers all matter.
Attack surfaces are getting bigger. Every service that connects to the internet is a new risk, from cloud tools to chat apps.
Incident response needs to change; just finding a breach isn't enough. Teams must keep an eye on, study, and plan for threats that might happen in the future.
People don't give enough credit to awareness a non-technical worker clicking "remind me later" on an update can sometimes cause a lot of problems.
This weekly summary isn't meant to scare people; it's meant to make them aware. Cyber threats change all the time, and so do defenses.
My Thoughts on This Weekly Summary
It felt different to write this week's recap. Cybersecurity news has a certain beat: exploit, patch, repeat. But this week felt more like a real person. You could almost feel the teams' exhaustion as they worked on late-night patches, the users' frustration as they had to change their passwords again, and the website owners' disbelief when they found out they had been hacked.
This weekly recap makes one thing clear: technology keeps changing, and so do mistakes. We try to make things perfect by using patches, and hackers look for clues in those same patches. It's a race that never ends.
In the end, it doesn't matter who wins each sprint; what matters is how long we stay in the race.
Final Thought
This weekly recap from October 3 to 9, 2025, covers a week in cybersecurity that was both chaotic and eye-opening. The stories about Oracle's urgent fix, Discord's huge leak, Redis, Chrome, and Zimbra may seem unrelated, but they all tell the same story: you can't be too careful anymore.
So, always update your browser, install that security patch, and check your firewall. Don't ever think that your small site won't be attacked. Because this week showed that it's not about "if" anymore; it's about "when."
Explore our main services:
· Deep and Dark Web Monitoring
· ISO Certification and AI Management System
· Web Application Security Testing
Share this :