Urgent Fix: Windows Server Update Services WSUS Flaw

Hoplon InfoSec
26 Oct, 2025
Think about how the update engine you trust to keep your network safe could become the threat vector. That is the scary truth that many IT teams are dealing with right now because they found a serious flaw in Windows Server Update Services (WSUS).
Microsoft put out an emergency patch in October 2025 after finding a flaw in the update-service infrastructure that could let someone run code from a distance. This isn't just another update for Patch Tuesday; it's a call to action. If you don't patch your WSUS server, you could turn your best line of defense into an open door.
What's the Problem?
What the Vulnerability Means
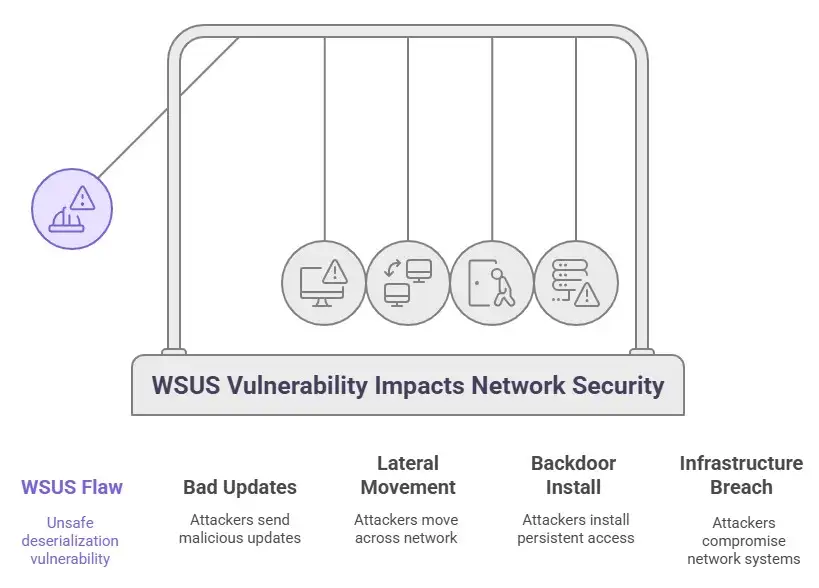
The CVE-2025-59287 vulnerability affects the Windows Server Update Services (WSUS) role. Many businesses use WSUS to send updates and patches to their own computers. An attacker could use this WSUS remote code execution flaw to send bad data to the WSUS service and make it unsafe to deserialize untrusted data. That lets them run any code they want, possibly with SYSTEM rights.
Why It's Important
The risk is very high, especially since WSUS servers usually have higher privileges, trusted roles, and access to a lot of other systems on the network. If an attacker gets control of WSUS, they can send out bad updates, move sideways, install backdoors, and break into a lot of the infrastructure. One analyst said that the flaw might be "wormable" between WSUS instances, which means that it can spread on its own to servers that don't have the patch.
Taking Apart the Technical Details
How it works
This vulnerability is basically an unsafe deserialization flaw. The WSUS service accepts some serialized objects, like cookies or events. The problem happens when an attacker who isn't authenticated sends crafted payloads that the WSUS process deserializes without checking them properly. This makes it possible for any code to run.
The Score for Threats
Microsoft gave the vulnerability a CVSS score of 9.8 (critical) and said it was "Exploitation More Likely." This vulnerability is now one of the most urgent for enterprise networks because it has a high severity, a remote attack vector, and a trusted service role.
How to Use It and What It Covers
At the time of the disclosure, there were no confirmed mass exploitations in the wild that were specifically targeting this vulnerability. However, the risk is very real, and the possible damage is very high. Analysts say that it affects any company that runs WSUS internally, so it needs to be fixed right away.
Why This Affects You
Your WSUS server is like the head chef in a kitchen. It gets all the updates (ingredients) and sends them out across the network as patches (dishes). If the chef gets sick and serves poison, everyone in the kitchen suffers. A compromised WSUS server can also send out harmful "updates" and infect clients that you thought you were protecting.
Also, a lot of companies put off or don't bother to secure their update infrastructure because they think updates are harmless. This flaw changes the story. Attackers don't just go after end-user software anymore; they also go after the update mechanism and the trusted chain it makes. If you run WSUS, you're in the crosshairs.
Microsoft's Emergency Patch: The Fix
What Microsoft Did
Microsoft released a security update to fix the WSUS problem on Patch Tuesday in October 2025. The patch closes the unsafe deserialization vector and takes away the area that can be used for exploitation.
Action Needed Right Away
If you are in charge of WSUS servers, the steps are clear:
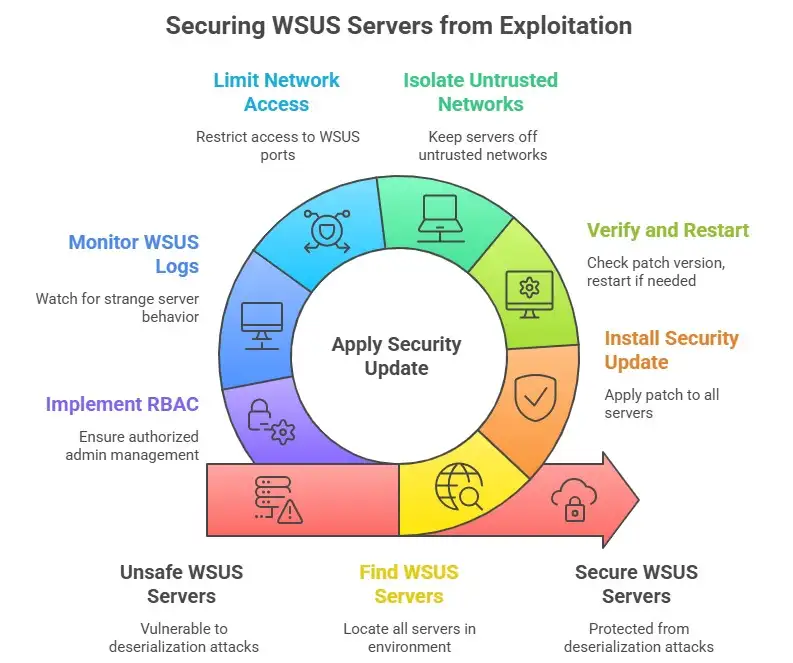
1. Find all of the WSUS servers in your environment, including secondary and replica servers.
2. Right away, install the Microsoft WSUS security update.
3. Check the patch version and restart if you need to.
4. Because of the "wormable" risk, you might want to keep WSUS servers away from networks that aren't trusted until they are patched.
More Hardening
In addition to patching, you should: • Limit network access to WSUS ports (like RPC and HTTP) so that only trusted systems can talk to it.
• Keep an eye on WSUS logs for strange behavior, like replication that wasn't planned, approvals that weren't authorized, or catalogs that got messed up.
• Make sure that only authorized administrators can manage WSUS by using strong RBAC (role-based access control).
• Put WSUS in a separate management VLAN or use a jump-host model to manage it.
Because the vulnerability is so serious, these are the best things to do.
Why You Should Act Like It's Already Exploited
Think about how many letters your local post office sorts every day. That post office not only delivers important mail, but it also has keys to a lot of homes. An attacker could forge letters, slip tampered packages, or send bad things to every home in the city if the sorting system didn't work right.
People trust the post office, and that trust makes a compromise even more dangerous.
Your WSUS server is like that post office in that it is big, reliable, and can reach a lot of people. That's why the Windows Server Update Services are so bad. The risk of a WSUS breach is so high that companies need to act as if one is already happening.
Who Is in Danger?
Any business that uses on-premises WSUS infrastructure is at risk. That includes: • Companies that have their own WSUS servers that take care of patching Windows Server and Windows clients.
• Companies that copy updates from one WSUS instance to others.
• Places where less-trusted network segments can reach WSUS servers, like remote offices, branch networks, or DMZs.
If you run WSUS and put off patching, you might leave a door wide open for attackers who don't need to log in and don't need to do much.
How to Put Your Response First
Because of the high risk, here's a suggested order of importance:
1. Patch all WSUS servers within 0 to 24 hours. If any of them can be reached from the outside or copied over untrusted links, keep them separate.
2. Look through the WSUS logs for strange events for 24 to 72 hours. Make communications and access controls stronger.
3. Check your update infrastructure within a week. Make sure that WSUS servers are separated and only replicate to trusted peers.
4. Beyond: Think about using more modern management methods, like cloud update services, better validation, and constant monitoring.
If you don't act quickly, attackers could take over your update chain, which has been less closely watched than end-user software in the past.
What We Learned and How to Avoid It
• Trust but check: Even services you trust, like WSUS, can be used to attack.
• Update infrastructure for segments: Update servers shouldn't be on the same network as servers that do other things or in areas that aren't trusted.
• Keep an eye on everything: Logging, finding unusual behavior, and keeping track of changes are all important for finding abuse of update infrastructure.
• Patch early and patch often: People find big, serious security holes like this all the time. The longer you wait, the more time you have to be exposed.
• The design is important: Think about whether your update plan still works in today's threat landscape. You may no longer be able to rely on just one on-prem WSUS server.
Final Thoughts
The Windows Server Update Services (WSUS) vulnerability (CVE-2025-59287) is a clear example of how the systems that are supposed to keep us safe can also be our biggest weakness. This flaw needs to be fixed right away because it has a critical severity rating, can run code remotely, and is trusted on networks.
Microsoft's emergency patch is in place, but your infrastructure is still vulnerable until all WSUS servers are updated. Don't wait for something bad to happen. Patch now, look over your architecture, and make your update pipeline stronger. If you are in charge of WSUS servers, act like this is already being used and do what you need to do.
Don't wait any longer. Find your WSUS servers, apply the patch, and make your defenses stronger.
Questions and Answers
Q1: What's the difference between a "WSUS patch" and a "Windows Server Update Services (WSUS) vulnerability"?
A1: A "WSUS patch" is an update you make to the WSUS infrastructure to fix security holes. The "Windows Server Update Services (WSUS) vulnerability" is the name of the specific security flaw (CVE-2025-59287) in WSUS that lets code be run from a remote location.
Q2: Does the "Microsoft WSUS RCE vulnerability" need user action to be used?
A2: No. The "WSUS remote code execution flaw" lets an attacker who is not logged in and has access to the network send specially crafted data to the WSUS server and start code execution. No user interaction is needed.
Q3: Is this flaw "wormable," meaning that it can be used on more than one WSUS server?
A3: Yes. Security experts have said that the flaw could spread between WSUS instances because the update infrastructure often copies itself between servers. That means that patching must be done quickly.
Q4: Which versions of WSUS or Windows are vulnerable?
A4: The advisory talks about the WSUS role on Windows Server versions that are still supported. You should look at Microsoft's Security Update Guide to see the exact list of SKUs that are affected and then apply the patch.
Q5: Are there any temporary fixes I can use if I can't patch right away?
A5: Yes. Before you patch, limit access to WSUS (especially from networks you don't trust), keep WSUS servers separate, watch for strange activity, check replication settings, and make sure RBAC controls are strict. These help lower exposure until the patch is ready to be used.
The Windows Server Update Services WSUS vulnerability shows how important it is to protect endpoints. Hoplon Infosec's Endpoint Security service ,mobile security survice helps businesses protect themselves from these kinds of threats by keeping an eye on things all the time, quickly fixing vulnerabilities, and taking steps to protect themselves before they happen. Before the next exploit hits, make sure your systems are safe with Hoplon Infosec.
You can also read these important news articles on our website.
For more Please visit our Homepage and Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :