Apple WebKit Security Update Exploited in the Wild 2025

Hoplon InfoSec
15 Dec, 2025
What is the Apple WebKit security update exploited in the wild, and why does it matter to you as an Apple user on December 13, 202? Apple confirmed that two serious WebKit vulnerabilities were being actively targeted before patches were released, and the company issued a new set of security fixes across iPhone, Mac, iPad, and other devices as a result. This article explains what went wrong, how Apple responded with an Apple WebKit zero-day patch, and why every device owner should act quickly to stay safe.
Apple confirms WebKit flaws exploited in the wild 2025 explained.
To understand the Apple WebKit security update exploited in the wild, you first need to know what WebKit is and why its flaws matter. WebKit is the core web browsing engine used in Apple Safari and all third-party browsers on iOS and iPadOS. Because of this central role, any flaw in WebKit can affect a wide range of apps and services.
In early December 2025, Apple disclosed that two WebKit vulnerabilities were being used in real attacks before they were publicly known or patched. That means attackers were taking advantage of the flaws before anyone had a chance to fix them, a situation known in security circles as a zero day. One of these flaws had already been patched by Google in its Chromium browser, yet remained a risk on Apple platforms until this update.
These vulnerabilities were serious. They could let an attacker take control of a device or damage its memory simply by getting the user to view malicious web content. This type of activity is usually part of sophisticated spyware campaigns aimed at specific individuals rather than broad mass attacks.

CVE-2025-43529 Apple WebKit flaw details
CVE-2025-43529 was one of the two issues addressed in the Apple WebKit zero-day patch. It is a use-after-free vulnerability. In simple terms, a use-after-free flaw happens when a program tries to use memory that has already been released. If that memory has been reallocated by an attacker, it can be manipulated to run harmful code.
Apple’s advisory notes that processing maliciously crafted web content could have led to arbitrary code execution, meaning an attacker could run their own instructions on a user’s device without permission. This is a core risk in any remote code execution scenario and one of the main reasons it was exploited in real attacks before the patch was issued.
What makes this particularly concerning is that attackers don’t need local access to the device hardware. They only need to trick a user into loading a web page or content designed to exploit this weakness. That ease of exploitation puts every unpatched device at real risk.
CVE-2025-14174 WebKit memory corruption issue
The second critical problem, tracked as CVE-2025-14174, involved memory corruption. This happens when a program writes or reads memory in a way that was not intended, and it often leads to unstable behavior, crashes, or the opportunity for an attacker to manipulate the system.
Memory corruption issues are a favorite tool for sophisticated attackers because they can provide a stepping stone toward bigger breaches. In this case, Apple said it had reason to believe this flaw had already been used in highly targeted attacks, particularly on older versions before iOS 26 was released.
What makes CVE-2025-14174 worse is that it was the same vulnerability that Google had just patched in Chrome on December 10, 2025. It highlights how cyber threats can cross platforms when common open source components like WebKit are shared across different products.

What Apple patched and how to fix WebKit vulnerabilities on iPhone and Mac
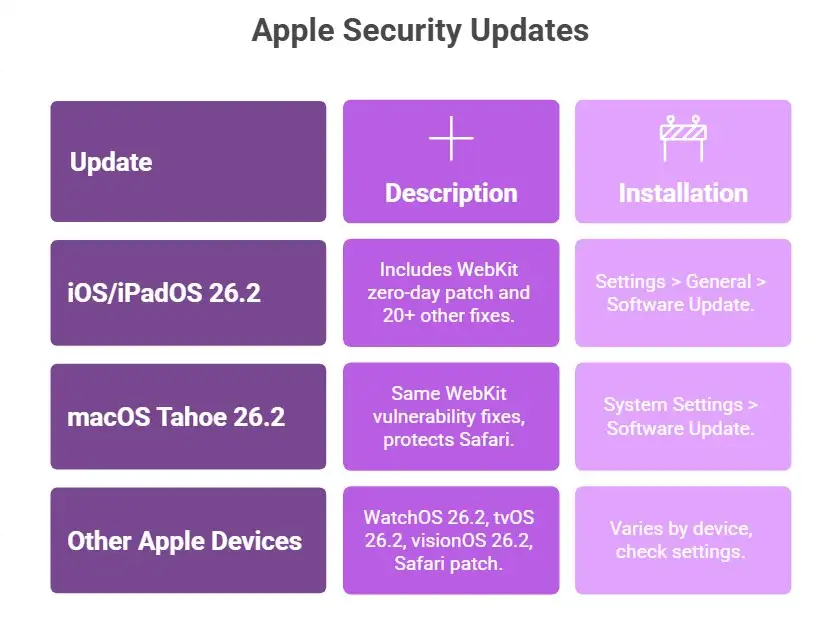
Here is a clear breakdown of what Apple fixed and how you can address these issues on your devices. The Apple WebKit security update exploited in the wild has now been included in several platform updates that were released on December 12 and 13, 2025
Step 1: Update to iOS 26.2 and iPadOS 26.2
• Go to Settings on your iPhone or iPad.
• Tap General, then Software Update.
• Install the iOS 26.2 security update as soon as it appears.
This update includes the Apple WebKit zero-day patch as well as fixes for over 20 other security issues, making it one of the more significant patches of the year.
Step 2: Update macOS Tahoe 26.2
• Open System Settings on your Mac.
• Select Software Update.
• Install the macOS Tahoe 26.2 security patch.
macOS Tahoe’s update includes the same WebKit vulnerability fixes, which also protect Safari and any other WebKit-based browser.
Step :3 Update other Apple devices
• WatchOS 26.2 (Apple Watch models)
• tvOS 26.2 (Apple TV models)
• visionOS 26.2 (Apple Vision Pro)
• Safari security patch 26.2 on supported Macs
Updating all devices ensures that the Apple WebKit security update exploited in the wild is applied across your ecosystem.
Each step is simple yet critical. If you delay, attackers may still find ways to exploit unpatched systems. Because these vulnerabilities were already used in real attacks, sitting on older versions of software poses a real risk.
Why the Apple WebKit security update exploited in the wild matters
This situation reminds us of something important about modern digital life. Most people think of software updates as optional annoyances, especially when they interrupt work or downloads fail at inconvenient moments. But when the Apple WebKit security update exploited in the wild becomes part of a targeted attack, every delay matters.
When vulnerabilities are exploited in the wild, it means attackers did not wait for public disclosure. They found a way in before defenders could catch up. That is the essence of a zero-day threat and why security teams take these flaws so seriously.
The fact that these WebKit vulnerabilities could allow arbitrary code execution or memory corruption means attackers could take over devices without user knowledge. These kinds of compromises are often used to install spyware that can exfiltrate messages, recordings, or personal data.
Because WebKit is used not only by Safari but also by third-party browsers and apps on Apple platforms, the scope of the risk was broader than most users would assume. It was not just a Safari problem; it was an ecosystem problem.
Case
In a real scenario earlier this year, another WebKit zero-day flaw led to sophisticated attacks on specific individuals. Apple discovered and patched that flaw after it had already been used in the wild on devices that had not yet been updated. Security specialists believe that in cases like this, attackers could chain weaknesses together to gain deeper access into target devices' data and communications.
Although specific details of how these attacks were carried out are not public, the pattern fits known spyware campaigns where carefully crafted malicious web content triggers hidden exploits. This underscores how critical the Apple WebKit security update exploited in the wild was to protect users before damage spread.

FAQs with short answers
What is the WebKit vulnerability Apple's patch refers to?
A WebKit vulnerability refers to a flaw in the browser engine that processes web content. Apple patched two such flaws that could be triggered by malicious web content.
How do I update my Apple device for security?y
Go to Settings on your iPhone or iPad, or System Settings on your Mac, open Software Update, and install the latest version. iOS 26.2 and macOS Tahoe 26.2 include the Apple WebKit zero-day attack.
Is my iPhone at risk without iOS 26.2?
If you stay on older versions, you remain exposed to the same WebKit vulnerabilities that have been actively exploited in the wild.
Which devices are affected by these WebKit flaws?
Nearly all Apple platforms that support recent software versions are impacted, including iPhone, iPad, Mac, Apple Watch, Apple TV, and Vision Pro devices.
Final Thoughts
If you have read this far and still have not updated your Apple devices, now is the moment to act. The Apple WebKit security update exploited in the wild shows how quickly attackers can take advantage of unpatched flaws. Whether you are on an iPhone, iPad, or Mac, checking for the latest updates and applying them right away can mean the difference between staying secure and facing a silent compromise. Make updating part of your daily routine. Your privacy and data depend on it.
You can also read these important cybersecurity articles on our website.
· Apple Update,
For more, please visit our Homepage and follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well.
Share this :