Cisco Vulnerabilities Exploited in AsyncOS Email Security Zero-Day

Hoplon InfoSec
18 Dec, 2025
As of December 18, 2025, how serious is the Cisco AsyncOS Email Security 0-day exploit that attackers are using? What should businesses do about it?
CVE-2025-20393 is a serious Cisco zero-day vulnerability that is being used in real-world attacks against Cisco AsyncOS Email Security Appliances, such as the Cisco Secure Email Gateway and the Cisco Secure Email and Web Manager. This flaw is very dangerous because it lets attackers get full root access to devices that are vulnerable. There isn't an official patch yet, which puts organizations that have made the Spam Quarantine feature available on the internet at immediate risk.
This article makes the problem very clear. You will learn what is going on, how attackers are taking advantage of these Cisco flaws, which products are affected, what you can do to assess and limit risk, and what to do right now, even though there is no patch.

What This Cisco vulnerabilities Hole Is All About
In the middle of December 2025, security experts and IT teams woke up to bad news. Researchers looking into Cisco vulnerabilities found that a flaw in the Cisco AsyncOS software is being used in real attacks by a threat actor known as UAT-9686, which is connected to groups that are linked to Chinese advanced persistent threat operations.
There is a zero-day vulnerability at the heart of the problem. That means Cisco hasn't put out a patch or a full fix yet. Weak input validation makes this vulnerability possible, allowing attackers to send unauthorized commands to the appliance's operating system. Attackers can run commands at the highest level of the system if they use it incorrectly.
This is not a risk that is only in theory. Cisco says that the threat of active exploitation is real and happening in the wild. The attacks started at least in late November 2025, and administrators may not know yet if their devices were affected.
This situation shows not only a flaw in the software but also the real cost to people of not fixing systems. These appliances are important for businesses because they help keep email threats out. If hackers get in, they can put in backdoors, delete logs, and take over the system for more attacks.
Why This Cisco Security Hole Is So Bad
Two Problems: Max Severity and No Patch
The highest level of risk for this Cisco zero-day vulnerability is a severity score of 10. If attackers are successful, they don't need a real account or permission to run harmful software on the appliance.
Organizations are in a bad spot because they have a high risk and no official way to lower it yet. Cisco hasn't released any patches yet, so defenders can only use indirect methods like reconfiguration and network restrictions.
This kind of risk doesn't happen very often, but it does happen. It reminds a lot of security teams of old high-impact vulnerabilities where patches didn't come out in time for attacks, so they had to come up with emergency fixes. The need is real.

Who Is Targeted and Why
The bad behavior is not random. Cisco Talos and several other independent reports say that this Active exploitation threat is happening on a large scale in businesses. Attackers are targeting businesses that have opened up administrative or quarantine interfaces to public networks without enough firewall protection.
A threat actor called UAT-9686 APT assaults Cisco equipment,s specifically listed as taking advantage of this flaw and leaving behind tools like backdoors, tunneling frameworks, and log purgers to keep access.
This is more than just scanning for opportunities. The pattern indicates focused activity. Attackers first look for configuration exposure and then set up persistent mechanisms. People who are affected might not notice until things like unexpected outgoing connections show up.
Products that are affected: Which Cisco Appliances Are in Danger
At this time, only a small number of Cisco AsyncOS products are known to be affected. More specifically:
• Cisco Secure Email Gateway (SEG) with AsyncOS running on it
• Cisco Secure Email and Web Manager (SEWM) with AsyncOS running on it
The flaw can only be used in certain situations. It needs the Spam Quarantine feature to be turned on and the interface that controls it to be accessible from outside the trusted internal network. This is something that happens a lot in large businesses and sometimes in environments that aren't set up right.
Not all installations are vulnerable right now because of this conditional exploit path. But even a few boxes that aren't set up right can give attackers a lot of access.
How the Cisco AsyncOS Exploit Works
The Technical Root
Attackers are taking advantage of the Spam Quarantine part of the vulnerable software's bad input validation. When input validation is done incorrectly, the system trusts some data without checking it properly. This lets attackers send messages that are made to make the system act in a way that is not intended.
This flaw lets code run from a distance, which is the kind of weakness that defenders are most afraid of. Attackers can effectively own the system if they reach the flaw because it can be accessed without authentication and can lead to root-level access.
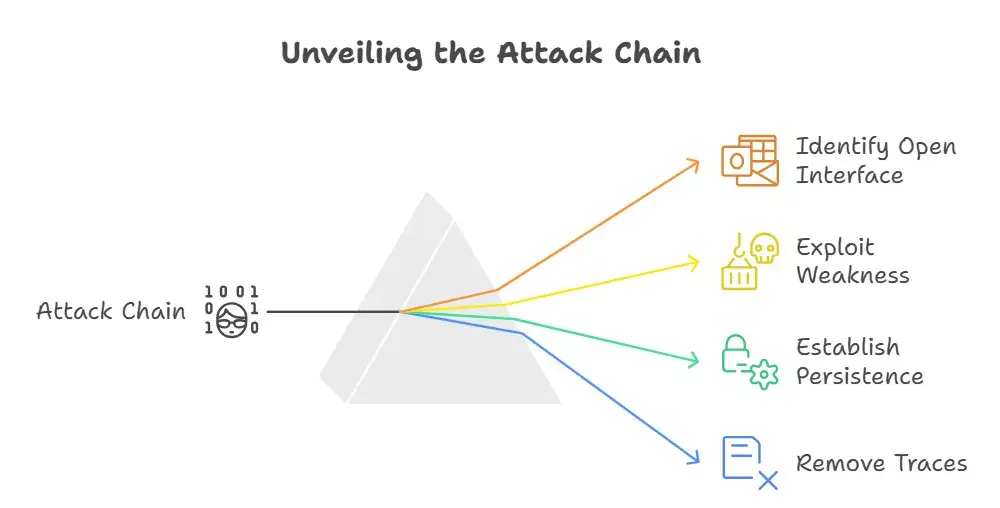
Steps of the Attack Seen
According to Cisco and security researchers, real attacks often follow this pattern:
1. Find the Spam Quarantine interface that is open.
Attackers look for asynchronous services that are open to the internet. They continue if the interface is open.
2. Send carefully crafted input to exploit the weakness.
The flaw lets them send commands to the system through requests that are set up in a certain way.
3. Get rid of the backdoor and tools.
Once they get in, attackers set up long-lasting software modules like reverse SSH tunnels and log purgers. These let them keep getting in, even if the admins change the passwords.
4. Exit traces have been removed.
Log purge utilities and other tools can help get rid of evidence of an attack, which makes it much harder to find.
This kind of chain makes it hard for defenders to see what's going on and gives them few proactive alerts. That makes it hard to see the whole picture.
What Happens in the Real World When Cisco SystemsIse Hacked
Most businesses use email gateways to check for malware, phishing, and attachments that look suspicious. When attackers take over that system, they can read or change business communications. Security teams have seen: • Email flows coming in and going out being intercepted.
This could make private company information or plans available to the public.
• Access from afar that lasts for future use.
Systems are like beachheads that let networks go deeper.
• Using hacked systems in bigger attacks.
Once inside, attackers can move to internal servers or cloud environments.
One confirmed pattern is that backdoor tools can listen for commands from a distance and talk to the system shell. That means that attackers can get into a trusted endpoint without any problems.
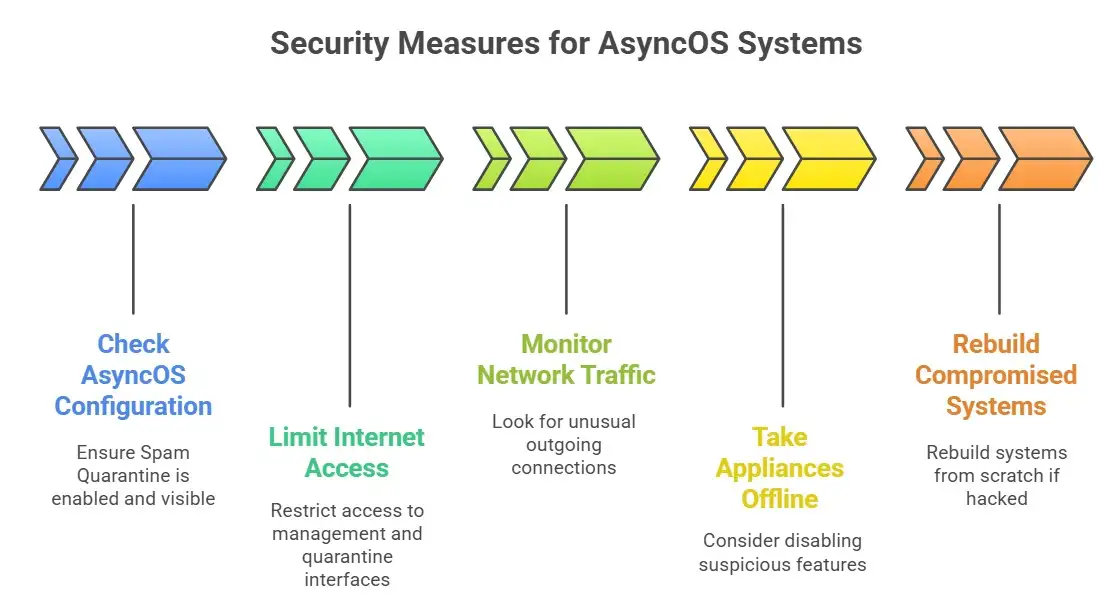
What You Should Do Now (In Steps)
This part gives security teams things they can do to lower risk while they wait for a patch to come out.
1. Check the configuration of your AsyncOS systems right away.
Make sure that Spam Quarantine is turned on and visible. If you're not sure how to check, ask your vendor support or look in your administrative guide.
2. Limit internet access to management and quarantine interfaces.
Put these behind firewalls or VPNs so that people with public IP addresses can't get to them.
3. Keep an eye on strange network traffic.
Look for outgoing connections that you didn't permit, especially to IPs you didn't expect.
4. If you're not sure, you might want to take the affected appliances offline.
It might be safer to turn off the suspicious feature completely until a patch comes out.
5. Rebuild systems that might have been hacked.
If attackers get into your system, the safest thing to do is to rebuild appliances from scratch instead of trusting an image that may have been changed.
These steps aren't perfect. They lower the risk of exposure and attack, but they don't take the place of a proper patch when it comes out.
A Wake-Up Call for a Medium-Sized Business
Think about a medium-sized company that works in finance. They used Cisco Secure Email Gateway to sort through the emails of their workers. Their security team turned on Spam Quarantine on a public interface to make it easier for people inside to review. They thought that their firewall rules would keep it safe.
They didn't know that this setup made it easy for attackers to find and take advantage of the Cisco flaws. Within days, the attackers got root access and set up tools to clean up logs. The team only found out when analysts saw strange outgoing connections in their logs.
Cisco Talos warned about this kind of situation. The company had to isolate its appliance and rebuild it from scratch because there was no patch available at the time.
Questions that are often asked
What does CVE-2025-20393 mean for Cisco AsyncOS?
For some setups, it is a serious Cisco zero-day flaw that affects Cisco Secure Email Gateway and Cisco Secure Email and Web Manager.
How can hackers take advantage of Cisco AsyncOS email appliances?
Attackers make special input for the Spam Quarantine feature that lets them run remote code and get root access on devices that haven't been patched.
What Cisco products are at risk from this zero-day?
Only certain versions of Cisco Secure Email Gateway and Cisco Secure Email and Web Manager running AsyncOS with certain settings that are open to the public are at risk so far.
What can admins do to lower the risk?
Admins should limit access to interfaces, keep an eye on traffic, turn off services that aren't needed, and rebuild systems that have been hacked.
What's Next
The AsyncOS zero-day and Cisco vulnerabilities show how quickly attackers can move and how vulnerable systems can be when they aren't patched. This Cisco AsyncOS Email Security 0-day flaw is one of the most serious threats to an organization right now because it lets attackers run code at the root level.
If your company uses Cisco email appliances and has even a hint of exposure, you should check your settings, limit internet access, and make plans for how to respond to an incident right away. There isn't an official patch yet, but that could change very quickly. It's very important to keep an eye on Cisco's security feeds and advisories.
This is an urgent matter that you should take care of right away. Talk to security experts to make sure your defenses are in line and check your systems for any signs of compromise.
You can also read these important cybersecurity news articles on our website.
· Apple Update,
For more Please visit our Homepage and follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :