Fortinet FortiWeb Vulnerability Actively Exploited in Live Attacks

Hoplon InfoSec
17 Dec, 2025
Are hackers really using the Fortinet FortiWeb flaw to break into live networks right now?
Yes, and that's the uncomfortable truth that security teams will have to deal with in December 2025, according to reliable reports from CISA.
It's not just the vulnerability itself that makes this situation scary; it's also how quietly and effectively attackers are using it. Many companies still think their perimeter defenses are doing their job, but those same defenses may already be working against them.
What's Really Happening with the Fortinet FortiWeb Vulnerability
CVE-2025-64446 is the name of the Fortinet FortiWeb vulnerability that is getting a lot of attention around the world. FortiWeb, Fortinet's web application firewall, has a problem with authentication bypass at its core. In simple terms, this flaw lets an attacker go right past the login screen and get full administrative access without a password.
That's bad enough on its own. But the situation is serious. FortiWeb usually sits in front of important business apps, customer portals, APIs, and tools that are used inside the company. It is trusted to look at traffic and stop bad behavior. When attackers get control of it, they don't just sneak in. They change the rules about what is okay.
A few security researchers noticed something strange not long after Fortinet released patches. People started trying to take advantage of the situation right away. That timing strongly suggests that the attackers were ready. Either they already knew about the flaw, or they had access to ways to take advantage of it before the public advisory.
There is more than one Fortinet FortiWeb vulnerability. Fortinet is actively exploiting FortiGate firewalls and identity components as part of a larger pattern. The security community is worried about that pattern.

A Simple Explanation of How the Fortinet FortiWeb Authentication Bypass Works
This weakness has to do with how FortiWeb handles some internal web requests. Researchers call it a path traversal authentication bypass, but it's easier to understand when you think of it in terms of a real-world example.
Picture a building with locked hallways that only staff can use. Because of the weakness, attackers can make a request that makes the system open those doors without checking who is asking.
In a technical sense, malformed HTTP requests change how routing works inside FortiWeb, which makes administrative endpoints accessible without authentication. When attackers get to these endpoints, they can do things that only real administrators can do.
You can't guess the password. No clear error messages. Logs often show normal admin activity. This Fortinet FortiWeb vulnerability is especially dangerous because normal alerts might never go off.
Once attackers get in, they can make new admin users, change the passwords of existing users, change security rules, or even upload harmful configurations. Several incident responders said they found admin accounts that looked like real ones, which made it even harder to find.
Weak Versions and How Patch Confusion Made Things Worse
Fortinet confirmed that several versions of FortiWeb were affected before emergency fixes were made available. Some patches came out without making it clear that they were being used to exploit.
That made people think twice. Most administrators thought that updates were normal. Some people put off patching because they were afraid of breaking production traffic or because they had to do maintenance first. In the meantime, the attackers kept scanning.
There was even more talk about the Fortinet FortiWeb vulnerability when people started talking about Metasploit modules and proof-of-concept exploits in secret online forums. At that point, attacks often change from being aimed at specific targets to scanning a lot of computers.
For defenders, the time between the release of a patch and its widespread use was too short.
The FortiGate SSO Authentication Bypass Made Things Worse
FortiGate firewalls were also under pressure, even though most people were paying attention to FortiWeb. CVE-2025-59718 and CVE-2025-59719 are two security holes that affect FortiGate's single sign-on feature.
These FortiGate authentication bypass flaws let attackers take advantage of how identity is checked. When FortiGate works with Active Directory or cloud identity providers, this makes it possible for someone to impersonate someone else or gain more access.
It's especially worrying that FortiGate and FortiWeb are often used together. A broken WAF and a broken firewall can start a dangerous chain reaction. The Fortinet FortiWeb vulnerability is the way in, and the FortiGate weaknesses let attackers get deeper into the system.
Shortly after the firewall was hacked, security teams started to see signs of lateral movement, such as strange VPN activity and policy changes that weren't allowed.

How These Attacks Look in Real Life
Most of the time, things that happen in the real world don't seem dramatic at first. There is no clear outage or ransomware note. Things don't feel quite right, though.
Security teams have told similar stories. First, there are scans against management interfaces that don't make sense. Then there was a quiet pause. A new admin account shows up days later. Logs are either clean or missing.
Some companies saw FortiWeb appliances connecting to IP addresses that they didn't know about. Some people noticed that security rules had changed in small ways that let bad traffic through without being noticed.
One security engineer said it was like finding out that the lock on their front door still worked, but someone had quietly taken the alarm system down weeks before.
That is what makes the Fortinet FortiWeb vulnerability so dangerous. It makes a protective control into a quiet partner in crime.
How CISA and the KEV List Changed the Talk
When CISA added these Fortinet vulnerabilities to its Known Exploited Vulnerabilities list, it proved what many people thought. These were not examples from the edge or the lab. Attackers were using them on purpose.
For government agencies, including KEV, it means they have to meet deadlines. It should be a clear warning to everyone else that waiting is not an option.
Telemetry from security companies showed that hackers were trying to take advantage of people in many fields, such as healthcare, finance, and technology. The wide range of locations suggests that automated scanning was used instead of separate campaigns.
At this point, it's not a question of whether someone will try to take advantage of a vulnerability. It's about whether your device is already on their list.
How to Know If Someone Has Touched Your FortiWeb Device
Many administrators are worried and ask the same thing. Is my Fortinet device hacked?
There isn't one answer, but patterns can help. Look over the admin accounts carefully first. Look for accounts you don't know about or that were made without a clear request for a change.
Look over any changes you've made to your settings in the last few weeks. Keep a close eye on security rules that have been turned off or alert thresholds that have been changed. See if logging has been turned off or sent somewhere else.
You should also look at the traffic that goes out of the FortiWeb appliance itself. WAFs usually don't make a lot of connections to the outside world. Things that happen here that aren't expected should be looked into.
Below is a simple text table that shows common warning signs.
Sign
Admin accounts that aren't allowed
Changes to the configuration that you didn't expect
FortiWeb's outbound connections
Logs that are missing or have been changed
There may be a reason for each of these on its own. They all point strongly to exploitation.
Useful Steps for Fixing Problems That Go Beyond Patching
The first step is patching, but it's not the last. Get updates straight from Fortinet and check that they are correct. Don't make any assumptions about automatic updates.
Next, change all of the administrative passwords. Think about the fact that they might have been exposed. This includes FortiWeb-linked API tokens and service accounts.
Check configurations by hand. Automated scans are useful, but people often find small changes that tools miss.
Limit access for management very strictly. Close any FortiWeb management interfaces that are open to the internet. Instead, use VPNs or separate management networks.
Finally, keep an eye on things more closely for a while. Turn on verbose logging and send the logs to a different system. For a few weeks, keep a close eye on administrative actions.
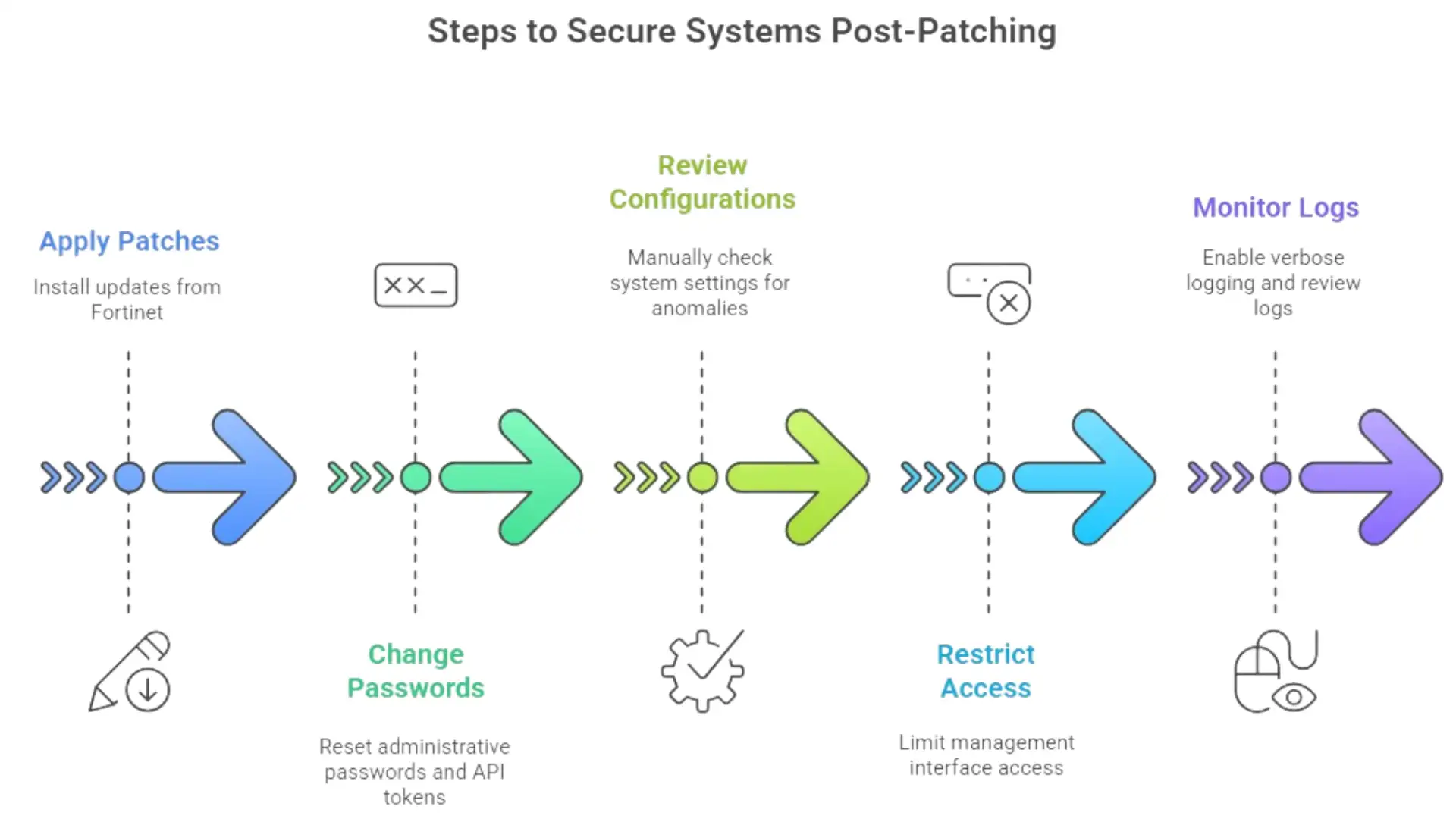
These steps won't fix the damage that has already been done, but they will stop attackers from keeping control.
What This Event Teaches Us About Trust in WAF
Many teams have treated WAFs like appliances that you set up once and forget about for years. This wave of Fortinet active exploitation shows that the old way of thinking is no longer useful.
Attackers now go after security infrastructure because it gives them an edge. Exploiting a single Fortinet FortiWeb vulnerability can give you access to many apps at once.
This has also brought up old discussions about how vendors talk to each other. Defenders are left guessing when there are quiet patches and vague warnings. Organizations would be able to respond more quickly if they had clearer timelines and more openness.
Some businesses are now rethinking how much they depend on single-vendor stacks. Some people are looking into managed security services to fill in the gaps in their operations.
A Short Story That Explains the Risk
Imagine that your WAF is like a security guard at the door of a busy office. The Fortinet FortiWeb vulnerability is like giving an attacker a uniform that the guard never questions.
The attacker doesn't have to break down doors once they're inside. They just let other people go by. That's exactly what happens when a WAF that has been hacked lets bad traffic through on purpose.
There is no noise. It's not obvious. And it works very well.
Questions and Answers
What is the Fortinet FortiWeb security hole that lets people get around authentication?
CVE-2025-64446 is the name of the flaw that lets attackers get administrative access without valid credentials.
How do hackers take advantage of FortiGate SSO bugs?
They take advantage of flaws in identity verification to get around authentication and gain more power.
Which versions of FortiWeb are at risk?
Several versions before emergency patches. Always check the most recent Fortinet advisories.
Are there signs that FortiWeb exploits have been successful?
Yes. Common signs include unauthorized admin accounts, changes to settings, outbound traffic, and missing logs.

Final Thoughts
The Fortinet FortiWeb vulnerability is more than just a security story. It reminds us that we should always check the tools we trust the most.
Do something right away if you use FortiWeb or FortiGate. Patch, check, and confirm. Don't think that being quiet means you're safe.
Attackers are no longer banging on the door. They are sneaking in, changing the rules, and waiting. It's time to look before they decide to move again.
You can also read these important cybersecurity news articles on our website.
· Apple Update,
For more, please visit our Homepage and follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well.
Share this :