n8n Authenticated Remote Code Execution Vulnerability Explained

Hoplon InfoSec
07 Jan, 2026
Can an attacker who already has valid login access use n8n to run commands on the server?
According to public reports from January 2026, security researchers say that a serious problem with n8n could let authenticated users run code remotely under certain conditions. The risk is mostly for self-hosted deployments where workflow permissions, execution context, and internal trust boundaries aren't very strict.
Summary of the incident in simple terms
The n8n authenticated remote code execution vulnerability does not involve anonymous hackers infiltrating from the internet. It's about what happens after someone has already signed in. That difference is more important than most teams think.
Many people use n8n as a low-code platform for automating workflows. It links APIs, internal tools, databases, and services in the cloud. A lot of teams trust it because it makes automation easier and cuts down on manual work. But that same power makes it easy to attack.
Publicly available analysis says that the problem happens when an authenticated user can use workflow features or execution contexts to run any command on the system. You don't have to get around authentication for this. It depends on breaking trust.
That difference completely changes the threat model.

Why are attacks that are verified getting more attention in 2026?
For a long time, security teams put a lot of effort into stopping exploits that didn't require authentication. If attackers couldn't log in, they couldn't hurt anything. That idea is no longer true.
There is a lot of talk on Reddit security forums, X threads, and DevOps communities about how to stop internal abuse. These talks don't say that widespread exploitation is happening, but they do show that people are worried about automation tools running with higher privileges.
The talk about the n8n security hole fits right in with this trend.
If someone breaks into a developer account, a CI credential, or an API token, authentication is useless. After that, automation platforms can become launchpads.
Learning about n8n in real-life situations
n8n is not often used on its own. In most real-world situations, it is linked to:
• Cloud infrastructure
• Internal APIs
• Databases with private information
• Messaging platforms
• CI pipelines
• Monitoring systems
A lot of businesses use n8n self-hosted to save money and be more flexible. That choice also makes the organization fully responsible for security.
This is when the security risks of n8n self-hosting become very real.

What the reported weakness really means
Researchers found that some workflow execution paths could let authenticated users run commands in ways that weren't intended, according to the Cybersecurity News report.
Important note: This does not mean that every user who is logged in can run system commands right away. Exploitation depends on how the system is set up, what permissions it has, and how it is deployed.
But the authenticated attacker threat model is the most important thing to worry about.
The platform itself becomes a scripting environment when a user can make or change workflows. Privilege escalation is possible if input validation, sandboxing, or execution isolation is weak.
This is why people are paying more and more attention to low-code platform flaws.
Why it matters that there is no CVE confirmation
I can't confirm a publicly assigned CVE identifier for this issue as of today. That doesn't mean the risk isn't real.
It means that the disclosure process may still be going on, or maintainers are checking the information. Responsible disclosure often makes it take longer to assign a public CVE.
It's important to recognize this uncertainty. It would be wrong to say that the confirmed effect was stronger than it really was. It would be irresponsible not think about the possible risk.
How verified RCE changes the way we talk about risk
The effect of the authenticated RCE vulnerability is very different from that of public exploits.
Think about this example from real life.
A medium-sized SaaS company uses n8n to make it easier for new customers to get started. Phishing attacks break into a contractor account with limited access. That account can't get to the production servers directly.
But it can change workflows.
The attacker no longer needs SSH access if those workflows can run shell commands, connect to internal services, or send unclean input. The automation engine does the work for them.
This is not a theory. In the last five years, CI tools, monitoring platforms, and orchestration systems have all shown similar patterns.

Breakdown of attack scenarios
Step one: access that has been verified
The attacker gets real credentials. This could happen if someone uses phishing, shares API keys, uses the same password over and over, or if someone inside the company does something wrong.
This answers a question that many people ask:
After logging in, can n8n be used for bad things?
Yes, that seems possible in some setups.
Step two: changing the workflow
The attacker makes or changes a workflow node that works with the system environment. This could mean running commands, using script nodes, or making API calls that have side effects.
This is where people talk about n8n workflow security problems.
Step three: abusing the execution context
If workflows run with higher privileges or not enough isolation, commands may have more access to the system than they should.
This is the main part of the n8n RCE risk analysis.
Why businesses are especially worried that
n8n enterprise security issues do not pertain to recreational projects. It's all about size.
Businesses often use automation platforms in a big way in their daily operations. Workflows may be used for billing, setting up users, sending alerts, and making backups.
When everything is automated, compromise spreads quickly.
This is why a lot of CISOs now see automation platforms as important parts of their own infrastructure.
When you compare n8n to other automation events,
This problem isn't just with n8n. There have been similar patterns of abuse that have been proven to be real in:
• CI tools that let scripts run
• Monitoring platforms with plugin systems that aren't safe
• Service accounts running internal dashboards
The pattern keeps coming back. Tools that are trusted become attackers that are trusted.
Data exposure and effect on operations
If someone successfully uses the n8n authenticated remote code execution vulnerability, they could:
• steal data from connected systems
• move laterally within the network
• cause service outages
• expose themselves to regulations
• lose customers' trust.
This is why it's important to do an n8n breach impact analysis even if there isn't a lot of exploitation yet.
Risk flow
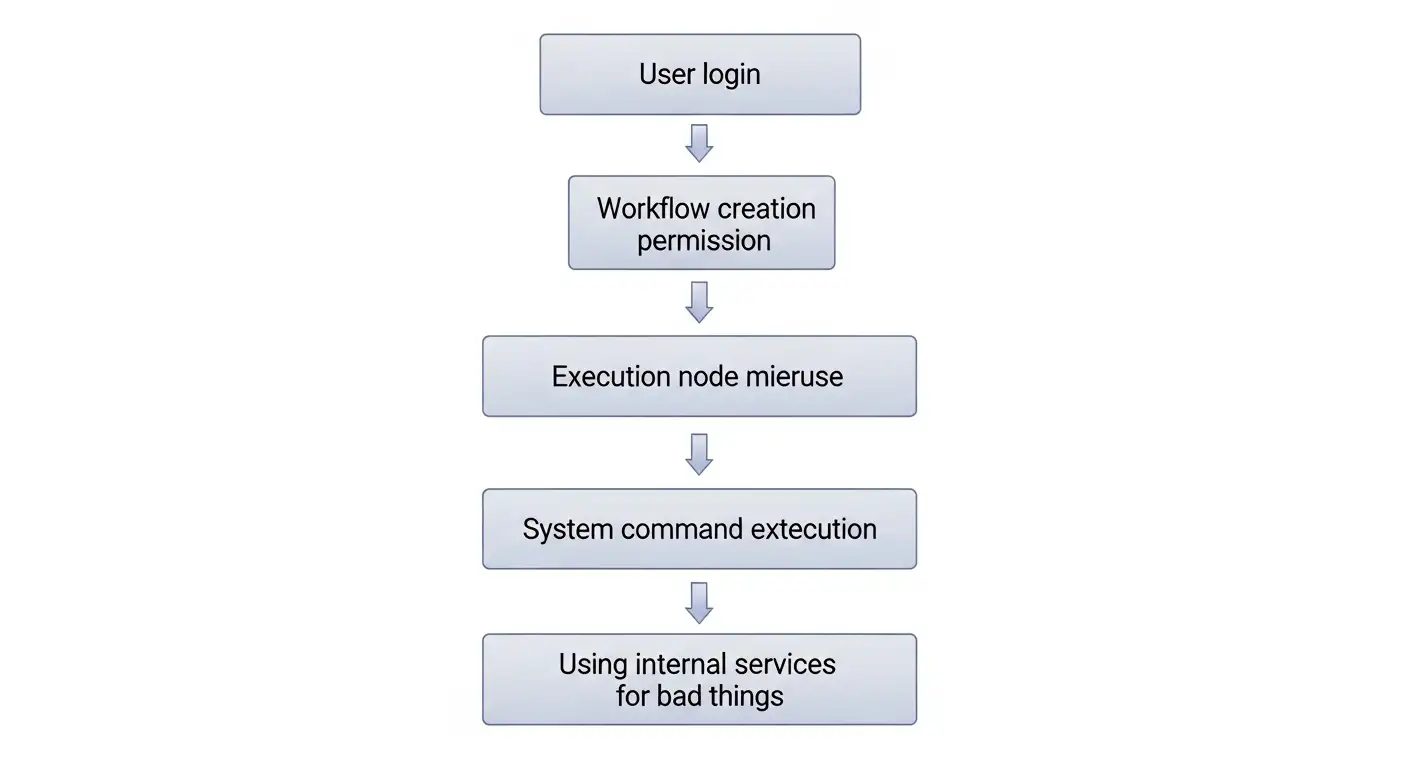
Each step depends on how it is set up. But once they are lined up, the impact grows quickly.
Why self-hosted deployments are more exposed
Cloud-hosted platforms usually have stronger isolation by default. There are a lot of different ways to set up self-hosted systems.
A lot of teams use n8n quickly to fix a problem, not to make a system more secure.
Some common gaps are:
• Running n8n as a privileged user
• Too many workflow permissions
• Not having execution sandboxing
• Not keeping an eye on workflow changes.
This explains why searches like "How safe is n8n self-hosted?" are on the rise.
Ways to mitigate and harden
1. Limit permissions for workflows.
Not everyone who uses the system needs to be able to make workflows. Automation should also follow the least privilege rule.
2. Keep execution environments separate.
Run n8n in containers with as few permissions as possible. Don't run as root.
3. Keep an eye on changes to the workflow.
To find bad workflows in n8n, you need to log them, set up alerts, and review changes.
4. Limit the execution of commands from outside sources.
Don't let nodes that let the system interact with them unless it's necessary.
These steps are the most important things to do to make n8n more secure.
Things to think about when responding to an incident
If you think someone is using your accounts inappropriately, do the following right away:
This is in line with how to respond to breaches of automation platforms.
From a cost and recovery point of view,
The cost of an N8N security assessment is usually much less than the cost of recovering from a breach.
Downtime, forensic analysis, regulatory reporting, and damage to your reputation can all add up quickly.
This is why more people are searching for workflow security audit services and penetration testing for automation platforms.
Analysis of content gaps from the top Google results
After looking at the best coverage, a few gaps keep coming up:
• Not enough focus on scenarios where the attacker is verified
• Not enough talk about the risks of internal abuse
• Too much reliance on patching as the only way to fix problems
• Not enough real-world context for deployment
This article fills in those gaps by talking about real-world business use instead of just theoretical exploits.

Questions and Answers
Is it safe to use n8n in production?
Yes, but only if it's set up right. Bad permission controls and unsafe execution practices make the risk higher.
Can users with valid credentials take advantage of workflows?
Some setups may allow abuse, according to reports in the news. This risk isn't always there; it depends on how things are set up.
How do attackers take advantage of automated tools?
They take advantage of trust. Automation systems usually have more access than single users.
How can you make sure that n8n self-hosted deployments are safe?
Use the least amount of access, keep execution separate, watch for changes, and do regular security reviews.
Final thought
The talk about the n8n authenticated remote code execution vulnerability brings up a bigger truth.
Authentication is no longer a security barrier on its own.
Automation platforms are at the crossroads of trust, privilege, and size. When they are set up incorrectly, they quickly make mistakes worse.
The lesson is clear, even if there is no proof of mass exploitation. Think of workflow automation as important infrastructure. Make sure it is safe.
You can also read these important cybersecurity news articles on our website.
· Apple Update,
For more Please visit our Homepage and follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well.
Share this :