Pen Testers Explained: How Professional Pen Testers Protect Businesses

Hoplon InfoSec
26 Dec, 2025
Are pen testers really the only way to be sure that your business can be hacked today?
Businesses will face constant cyber threats by 2025 that seem invisible until they cause real damage. According to widely accepted advice from OWASP and NIST cybersecurity frameworks, organizations can't just use tools or scanners to figure out what the real risks of an attack are. This is where pen testers come in. They legally act out attacks to show how systems fail in real life, not just in theory.
Most businesses think they are safe until something goes wrong. Firewalls look good. Antivirus dashboards are green. Then one email, one weak password, or one server that you forgot lets you in.
Pen testers work in the space between what people think is safe and what is really risky. They think like criminals, stay within the law, and find weaknesses before criminals do.
In this article, I will explain pen testers from the ground up, not as a buzzword, but as a real service that businesses use when security is important.
What do pen testers do, and why do businesses hire them?
Pen testers, which stands for penetration testers, are cybersecurity experts who are paid to try to break into systems, networks, and apps in a safe way. Their job is not to break anything but to show what could happen if an attacker did the same thing.
Pen testers use their own judgment, unlike automated vulnerability scanners. They turn small technical holes into real attack paths. Most people don't know how important that difference is.
Based on what I've seen in real breach reports and public incident reports, a lot of companies had scans set up, but no one tried to connect the weaknesses. That's where attackers get what they want.
Pen testers do that job legally and morally.

What Do Pen Testers Do Every Day?
A lot of people think that pen testers only run tools and write reports. That's not right.
Pen testers really spend a lot of time learning how a business works. They look at things like login flows, how employees act, cloud architecture, APIs, and even old systems that have been forgotten.
Then they try to take advantage of these areas the same way a real attacker would. Slow, careful, and planned. Sometimes the biggest problems aren't technical at all. They are either mistakes in the process or assumptions made by people.
OWASP Top 10 risk categories put more emphasis on real-world exploitation scenarios than on theoretical vulnerabilities. This approach fits well with that.
Is it legal and safe for businesses to hire pen testers?
Yes, if you do it right.
Pen testers work under a signed legal document called a scope of work or authorization letter. This document says what can be tested, how far attacks can go, and which systems are off-limits.
Testing would be against the law without this permission. With it, pen testers can work safely, openly, and with responsibility.
A provider who can't clearly explain their legal process is a sign of trouble.
Different kinds of pen testers and penetration testing services
Not every pen tester does the same thing. Companies often make mistakes by hiring the wrong type of person for the risks they face.
Here are the most common types, explained in simple terms.

Testing for external penetration
This is about systems that are open to the internet. Cloud services, VPNs, email servers, and websites.
Many breaches start with attacks from outside. Verizon DBIR cites public breach investigations that show external access is still a major entry point, but the exact percentages change every year.
Pen testers try to get into these systems as if they were attackers from the outside who couldn't get in from the inside.
Testing for Internal Penetration
Here, pen testers think that an attacker has already gotten some access. This could mean that an employee account has been hacked or that someone inside is trying to do something bad.
Internal tests often show how quickly an attacker could get around once they get in. In a lot of places, it's easier to move around than you might think.
Pen Testing for Web Apps
Web apps are hard to understand. Login logic, APIs, payment systems, and integrations often make things weaker in ways that weren't planned.
Pen testers look for problems like broken authentication, access control failures, and handling data in an unsafe way. These are very similar to the risks that the OWASP Web Application Security lists.
Testing for network penetration
This looks at how servers, devices, and internal systems talk to each other. Common issues include weak segmentation, old protocols, and bad handling of credentials.
Network tests often find risks that tools miss because they don't know what the user wants.
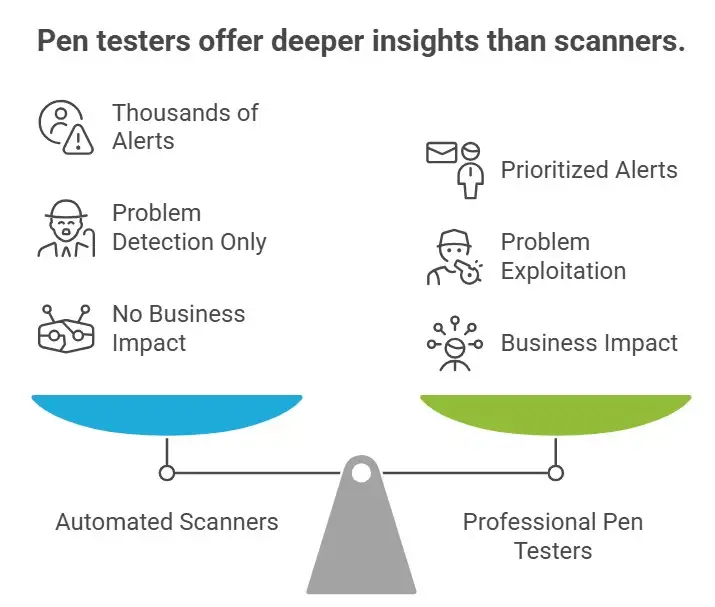
Why Companies Prefer Professional Pen Testers to Automated Tools
A lot of businesses ask the same thing. Why pay people when there are scanners?
Tools find specific problems. Pen testers find real attacks.
Step by step, here are the main differences:
• Scanners send out thousands of alerts.
• Pen testers check which ones are important.
• Scanners only look for problems.
• Pen testers try to exploit them.
• Scanners don't know how they affect the business.
• Pen testers explain risk in business terms.
This is why compliance frameworks like ISO 27001 and SOC 2 strongly suggest penetration testing, even when there are automated tools available.
What Certified Pen Testers Are and Why They Matter
There are differences between pen testers. Certification doesn't mean someone is good at something, but it does show that they have been trained in a structured way and follow ethical standards.
Some well-known certifications are the OSCP, CEH, and GPEN. People all over the world know about these programs, but people's skill levels still vary.
Businesses should still ask about real-world experience when hiring certified pen testers. Just having a certification isn't enough.
Companies are starting to value communication skills as much as technical ones, as shown by hiring trends talked about openly on LinkedIn and cybersecurity forums.
How Much Do Pen Testers Cost, and Are They Worth It?
The truth is that the cost of pen testing can be very different. Prices depend on how big, complicated, and deep the project is. No one rate works for all businesses.
Based on what public service providers have said, I can say that professional pen testers cost more than automated scans but a lot less than breach recovery.
People often talk about IBM breach cost studies, but the numbers change every year and are different in different parts of the world. What stays the same is that it costs less to prevent than to respond.
Pen testers are worth it if their findings lead to real fixes. Reports that aren't used are useless.
An example of a pen tester in the real world: Stopping a Breach
A mid-sized SaaS company thought its cloud setup was safe. They had MFA turned on and scans running all the time.
It was a security requirement for the customer to hire pen testers.
Within days, testers found a cloud storage bucket that wasn't set up correctly and was connected to an internal API. That API accepted requests without checking them first.
No tool marked it. No alarm went off.
Fixing that one problem probably kept customer data from getting out. That is what pen testers are worth in a quiet way. No news, no panic, just prevention.

Things People Get Wrong About Pen Testers
A lot of companies think that pen testers will break things. Professional testing doesn't cause problems.
Some people think that pen testers take the place of security teams. No, they don't. They go well with them.
Some people think that pen testers are only for big businesses. That is not the case anymore. Attackers often go after startups and small businesses because they think their defenses are weaker.
Frequently Asked Questions About Pen Testers
What do people who test pens do?
Pen testers pretend to be hackers to find weaknesses that attackers could use.
How often should you test your pen?
Most security frameworks say you should do it at least once a year or after big changes to the system.
Are pen testers only for compliance?
No. One reason is to follow the rules, but the main value is to really lower risk.
Can pen testers check out cloud systems?
Yes. A lot of pen testers work only in cloud and SaaS environments.
Should Your Business Hire Pen Testers Right Now?
Pen testers are no longer optional if your business stores customer data, processes payments, or uses digital systems.
They make things clear in a place where people make assumptions. They show how attacks really happen, not how tools think they do.
It's not about being afraid to hire professional pen testers. It's about knowing what's real and fixing problems before they become public issues.
You can also read these important cybersecurity news articles on our website.
· Apple Update,
For more Please visit our Homepage and follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :