VolkLocker Ransomware Attack Targets Linux and Windows in 2025!
-20251215065508.webp&w=3840&q=75)
Hoplon InfoSec
15 Dec, 2025
Is the VolkLocker ransomware attack a new type of cross-platform ransomware threat that businesses should be worried about in 2025?
Yes, and as of March 2025, several threat intelligence reports and investigations into incidents show that VolkLocker is actively going after both Linux servers and Windows systems, using the same tools and methods on both types of systems. This evaluation is founded on autonomous malware analysis and public disclosures from reputable cybersecurity researchers, including CyberPress.
CyberPress threat research, 2025
Beginning
Ransomware used to have a safe place to go. For a long time, hackers only went after Windows desktops and file servers. People often thought that Linux systems, especially enterprise servers, were safer by default. That idea is no longer true.
The VolkLocker ransomware attack has opened people's eyes. It shows how modern ransomware groups make malware that can easily move between operating systems, cloud workloads, and on-premises environments. This change is making defenders rethink how they protect, see, and respond.
Encryption is not the only thing that makes VolkLocker different. It spreads in a certain way, hits certain platforms, and puts a lot of pressure on companies that are already having trouble with downtime, compliance, and data leaks.
What is VolkLocker ransomware attack, and how is it different?
The VolkLocker ransomware family is a new type of ransomware that was first made public in early 2025. It was designed from the ground up to be a cross-platform ransomware that could run on both Linux and Windows, unlike other strains.
This design choice is part of a larger trend in the development of ransomware. Threat actors now think of hybrid infrastructure as normal. They expect to see Windows endpoints, Linux servers, virtualization hosts, and cloud workloads all together. VolkLocker fits perfectly into that world.
The Volklocker ransomware attack usually goes after servers instead of home computers. Some of the first victims were hosting companies, SaaS platforms, and businesses that used Linux-based application stacks. This goes along with the fact that server data is becoming more valuable, and attackers can ask for more money in ransom.
At the time of this writing, there is no public decryptor, which is another important difference. Victims have to make the same tough choice that people in other double extortion ransomware campaigns have to make: pay, restore from backups, or risk losing their data forever and having it made public.
How VolkLocker Ransomware Works Behind the Scenes
From a technical point of view, VolkLocker ransomware uses a method that is well-known but works well. After getting in, it sets up persistence, turns off recovery options, and starts encrypting files with strong cryptographic routines. Analysts think that a hybrid encryption model is used, which combines symmetric encryption for speed with asymmetric keys for control.
VolkLocker on Linux systems focuses on important folders that are linked to databases, containers, and application data. It goes after shared drives, backups, and resources that are connected to a domain on Windows. This dual ability is what makes Linux infections of Volklocker ransomware so annoying.
Threat actors can manage keys, keep track of infections, and plan data exfiltration by talking to a command and control server. There are still some details that haven't been confirmed, but many reports say that data theft happens before encryption in a lot of cases.
That kind of behavior puts VolkLocker squarely in the category of ransomware double extortion, where attackers say they will leak stolen data if you don't pay.
Why Linux Servers Are Now a Top Target
For a long time, Linux has been the backbone of business infrastructure. Linux is very important for web servers, databases, virtualization hosts, and container platforms. For attackers, getting into one Linux server can be very valuable.
The Volklocker ransomware Linux variant takes advantage of this fact. A lot of Linux servers don't have tools for endpoint security, centralized logging, or real-time monitoring. Administrators often put uptime ahead of hardening, which means that services are left open and weak credentials are still in place.
VolkLocker can encrypt terabytes of operational data in just a few minutes once it gets inside. The effect is immediate for businesses that offer services around the clock. When your system is down, you lose money, break SLAs, and hurt your reputation.
This is why the Linux ransomware threat landscape is changing so quickly. VolkLocker isn't the only one, but it's one of the best examples of where ransomware is going.
How the VolkLocker Ransomware Attack Moves and Works
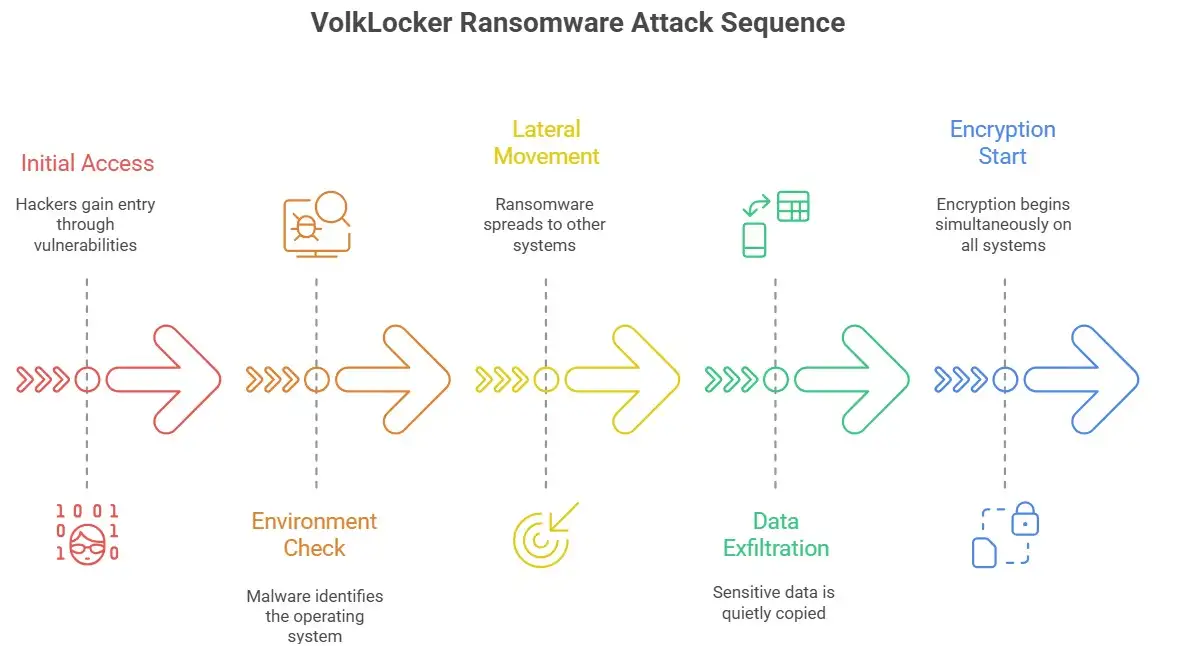
Defenders can break the infection chain if they know how it works. Investigators have found common patterns, even though every incident is different.
People often get in for the first time through open services, weak SSH passwords, or hacked VPN accounts.
Phishing and stolen admin credentials are still common ways for hackers to get into Windows systems.
Once inside, the malware checks the environment to see if it is running on Linux or Windows.
Next comes lateral movement, which lets the ransomware get to file servers, backups, and virtualization hosts.
Before encryption starts, data exfiltration happens quietly.
To have the biggest effect, encryption is started at the same time on all systems that can be reached.
This sequence shows why it's so hard to stop cross-platform ransomware attacks once they start.
A single server that is not noticed can connect Linux and Windows environments.
Signs of Compromise and Gaps in Detection
One of the hardest things about VolkLocker is that it's hard to see. A lot of companies don't keep an eye on Linux systems as closely as they do on Windows endpoints.
Common signs that your computer has been infected with VolkLocker ransomware
Even though indicators can change, some reported Volklocker ransomware indicators of compromise are
Linux servers have unexpected CPU spikes.
Stopping backup or snapshot processes without warning
Unauthorized creation of new scheduled tasks or cron jobs
Files that are encrypted and have strange extensions
Outbound traffic to unknown IP addresses that are connected to command and control servers
Detection tools that only use signature-based antivirus software don't work very well. Monitoring behavior and finding strange behavior are much more useful.
This is when tools that can find Volklocker ransomware on Linux workloads become very important. Sadly, a lot of businesses still don't have them.
Real Steps to Stop VolkLocker Ransomware
There isn't just one solution. To protect against VolkLocker, you need layered controls and realistic assumptions.
Steps to Mitigate That Work
To make Linux servers more secure, turn off services that aren't being used and require strong authentication.
To stop Linux and Windows systems from moving sideways, segment networks.
Check outgoing traffic for strange data transfers.
Make backups that can't be changed by ransomware.
Regularly test restoration procedures in real-world situations.
Teach administrators to spot early warning signs, not just phishing emails.
These steps to stop Volklocker ransomware aren't new, but they do require discipline. Businesses that didn't do these basic things are often the ones that get hit the hardest.

How to Get Rid of VolkLocker Ransomware After It Has Infected Your Computer
A lot of people look for ways to get rid of VolkLocker ransomware after it has already done damage. Sadly, getting rid of something is not the same as getting it back.
Getting rid of the malware may stop more encryption, but it doesn't bring back files. Without a decryptor, recovery depends on having clean backups or starting over with new systems.
Incident response teams say that infected systems should be isolated right away, forensic evidence should be preserved, and professional responders should be called in. Paying the ransom is still a controversial choice, and it doesn't guarantee that your data will be recovered.
Right now, searches for "how to remove Volklocker ransomware" often give incomplete advice. Being open is important. There isn't a magic tool that can undo encryption right now.
A Real-Life Example from the Field
One documented case showed that a mid-sized SaaS provider saw a Linux database server running slowly late at night. By the time morning came, customer portals were down. Logs showed that traffic going out had spiked hours before.
The Volklocker ransomware attack had spread from one vulnerable SSH service to backup servers that ran Windows. Encrypted backups were made along with production data.
After five days, the company was able to restore some services. It took weeks to fully heal. The money loss went beyond the ransom. It didn't take long for lost customers, regulatory scrutiny, and overtime costs to add up.
This story is becoming more common.
Common Questions About VolkLocker Ransomware
What is the ransomware called VolkLocker?
VolkLocker is a new type of ransomware that can attack both Linux and Windows systems, with a focus on enterprise servers and important infrastructure.
Does the VolkLocker ransomware work on Linux servers?
Yes. One of the main reasons VolkLocker ransomware is thought to be dangerous is that it can infect Linux systems.
Is it possible to decrypt VolkLocker ransomware?
There isn't a public decryptor available right now. Victims have to use backups or rebuild their systems.
How to keep Linux safe from ransomware like VolkLocker?
The best defenses are strong access controls, network segmentation, monitoring, and reliable backups that are kept offline.
Final thoughts and what you should do next
VolkLocker's rise is not a one-time thing. It shows a bigger change in the way ransomware groups work. Attacks that work on more than one platform are no longer just ideas. They are here, and they are going after the systems that many businesses thought were safe.
This is the time to look over your defenses again if you have Linux servers, cloud workloads, or a mix of the two. Check the paths of access. Check backups. Make things easier to see. The most expensive way to learn is to wait until a Volklocker ransomware attack forces you to do something.
You can also read these important cybersecurity news articles on our website.
· Apple Update,
For more, please visit our Homepage and follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well.
Share this :