Weekly Recap: Major Cybersecurity Threats and Attacks Explained

Hoplon InfoSec
19 Dec, 2025
Weekly Recap: What Did This Week’s Cybersecurity Incidents Really Tell Us?
What were the most important cybersecurity threats and industry shifts this week, and why should businesses care right now?
Based on verified disclosures and trusted security reporting up to December 2025, this weekly recap shows a clear pattern of attackers moving faster than patch cycles, privacy risks expanding beyond malware, and security decisions increasingly tied to business strategy rather than just IT.
Reference: Public advisories from CISA, Apple Security Updates, Cisco Security Advisories, Fortinet PSIRT, and multiple independent cybersecurity news outlets published in December 2025.
Every week in cybersecurity feels intense, but some weeks quietly reshape how we think about digital risk. This one did exactly that.
From stealthy data stealers and ransomware that refuse to stay in one operating system, to billion-dollar enterprise deals and privacy concerns around AI chats, the signals are clear. Attackers are not slowing down, and neither are the consequences.
This weekly recap is not just a list of incidents. It connects the dots, explains what actually matters, and highlights the lessons many articles miss.
Attackers Are Exploiting Trust Faster Than Defenders Expect

Phantom Stealer Shows Why Credential Theft Still Works
The Phantom Stealer attack reinforces a hard truth. Stealing credentials remains one of the most effective attack methods, even in 2025.
Based on multiple security analyses, Phantom Stealer targets saved browser data, crypto wallets, messaging apps, and authentication tokens. What makes it dangerous is not complexity, but familiarity. It blends in with normal user behavior, often delivered through cracked software or fake updates.
Many top Google articles explain what Phantom Stealer does. Few explain why it keeps succeeding. The answer is trust fatigue. Users see update prompts every day and stop questioning them.
This weekly recap highlights that endpoint protection alone is not enough. Without strict application controls and user education, information stealers will continue to win quietly.
VolkLocker Ransomware Expands Across Linux and Windows
Ransomware used to pick sides. That line is gone.
VolkLocker targets both Linux and Windows systems, which suggests attackers are actively pursuing mixed enterprise environments like cloud servers, virtual machines, and hybrid networks.
Public reporting confirms that Linux-based ransomware is rising, especially against ESXi, Docker hosts, and database servers. VolkLocker fits this trend, though attribution details remain limited and should be treated cautiously.
What matters is the shift. Ransomware groups now assume organizations rely on Linux somewhere critical. This weekly recap emphasizes that ignoring Linux security is no longer an option.
Vulnerabilities Are Becoming Business Risks, Not Just IT Issues
Cisco vulnerabilities exposed weaknesses in email security appliances that many enterprises trust blindly.
Fortinet FortiWeb vulnerability exploitation shows how web application firewalls can become an entry point.s
Apple WebKizero-dayay exploitation proves mobile users remain high-value targets
Delayed patching continues to be the most common failure point
Cisco Vulnerabilities and the Email Security Blind Spot
Email remains the number one attack vector. Cisco security advisories confirm that unpatched vulnerabilities in email gateways were actively exploited.
The real issue is confidence. Many organizations assume email security appliances protect them by default. When those tools themselves become vulnerable, attackers gain privileged access quietly.
This weekly recap goes beyond listing CVEs. It stresses the operational gap. Security teams often do not monitor appliances with the same urgency as endpoints or servers.

Fortinet FortiWeb Exploitation Shows WAFs Are Not Invincible
Fortinet publicly acknowledged active exploitation of a FortiWeb vulnerability. While Fortinet released patches, confirmed exploitation means attackers were already inside some environments.
Web application firewalls are often seen as shields. When compromised, they sit directly in front of sensitive data.
The missing insight from most articles is governance. Who owns WAF patching? In many companies, no one clearly does. This weekly recap calls that out as a structural weakness.
Privacy and Strategy Are Colliding With Security
AI Chat Privacy Breaches Are a New Kind of Risk
Reports of AI chat privacy exposure highlight a new category of incident. Not classic hacking, but unintended data retention, access, or leakage.
Based on available disclosures, some AI platforms temporarily exposed user conversations or used them for model improvement without clear consent. Details vary by platform, and not every claim can be verified independently.
Still, the pattern is clear. Employees treat AI chats like private notebooks. They are not.
This weekly recap stresses policy failure over technical failure. Without clear AI usage rules, sensitive data will leak slowly and legally.
Read more
ServiceNow’s 7 Billion Dollar Deal Signals a Shift
The reported ServiceNow 7 billion dollar deal, while widely covered, lacks full public detail at the time of writing. Exact financial terms should be treated cautiously until confirmed by official filings.
What is clear is intent. Enterprise platforms are racing to own security workflows, automation, and risk visibility.
This weekly recap connects the dots. Security is no longer just protection. It is now a board-level efficiency and resilience play.
A Real World Pattern Many Miss
Imagine a mid-sized company.
They trust their email gateway. It runs Cisco software.
They deploy FortiWeb to protect customer portals.
Developers use AI chat tools to speed up work.
Their cloud backend runs on Linux.
None of these choices is wrong.
But one missed patch, one copied prompt, one exposed token, and suddenly, a ttackers chain everything together. That is not a theory. That is exactly how modern breaches happen.
This weekly recap exists to show those connections, not just incidents.
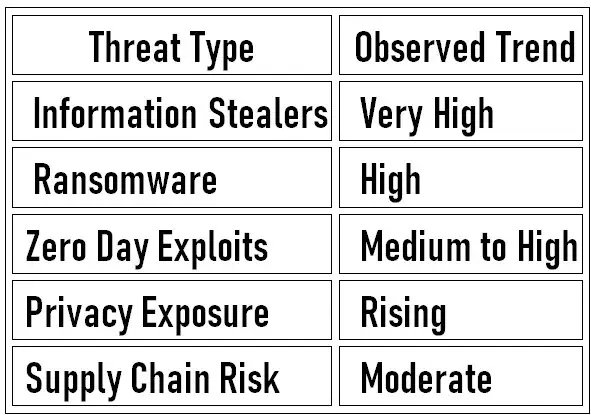
Threat Focus This Week
Attack Type Frequency Table:
FAQs
What is the main takeaway from this weekly recap?
Attackers are exploiting trust, not just vulnerabilities. Tools meant to protect are becoming targets themselves.
Are Linux systems now a major ransomware target?
Yes. Based on confirmed incidents, Linux servers and virtualized environments are increasingly targeted.
Should companies restrict AI chat usage?
They should govern it, not ban it. Clear rules on data sharing are essential.
Are these threats only affecting large enterprises?
No. Mid-sized organizations are often more exposed due to limited monitoring and delayed patching.
Why This Weekly Recap Matters
This was not just another noisy week in cybersecurity. It revealed a pattern of quiet failures, misplaced trust, and growing complexity.
A strong weekly recap is not about fear. It is about clarity. The organizations that learn from these signals will adapt faster. The ones that do not will keep reacting after damage is done.
If there is one lesson to carry forward, it is this. Security is no longer about tools. It is about decisions, timing, and awareness across the entire business.
You can also read these important cybersecurity news articles on our website.
· Apple Update,
· Windows Fix,
Share this :